c{api}tal (Checkmarx API Coaching and Studying) is a purpose-built weak API utility primarily based on the OWASP API High 10 dangers. It’s constructed with Python (FastAPI – a fast and simple to make use of net framework for creating RESTful APIs in Python) and JS (React), and it contains 10 API safety challenges.
c{api}tal was created by the Checkmarx Analysis workforce to offer customers with a “playground” so they might study and develop their API Safety abilities. It may be used to study and exploit API Safety vulnerabilities and for conducting your personal API Safety Seize The Flag (CTF) occasion.
In laptop safety, Seize the Flag (CTF) is an train by which “flags” are secretly hidden in purposefully weak packages or web sites. The purpose is to finish challenges as quick as attainable, get the very best rating, and win the competitors. Go to capital-ctf.com to study concerning the vulnerabilities and the challenges.
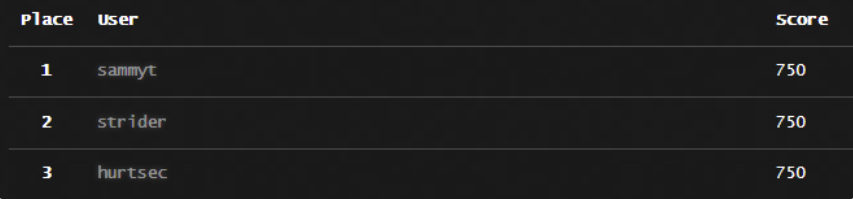
We first launched C{api}tal to the applying safety (AppSec) neighborhood at 2022 AppSec Village at DefCon30. It was an incredible expertise! Dozens of customers participated within the occasion, whereas solely 6 of them had been capable of full the ten API challenges.
We consider all contributors as winners for having the ability to up-level their safety abilities (why we had been all at DefCon), however we clearly should choose 3 for the competition. Full credit score goes to the winners:
As soon as the occasion ended, many superior write-ups had been performed by safety analysts and researchers who took half within the CTF occasion. One nice instance is that this medium write-up by Maor Tal.
Digging into API dangers
c{api}tal is a weak, running a blog utility that enables customers to register, create and delete posts, create and delete feedback, comply with different customers, and extra. The appliance could be constructed and deployed by operating a easy docker-compose command:
docker-compose up –d Among the API endpoints in c{api}tal could be seen right here:
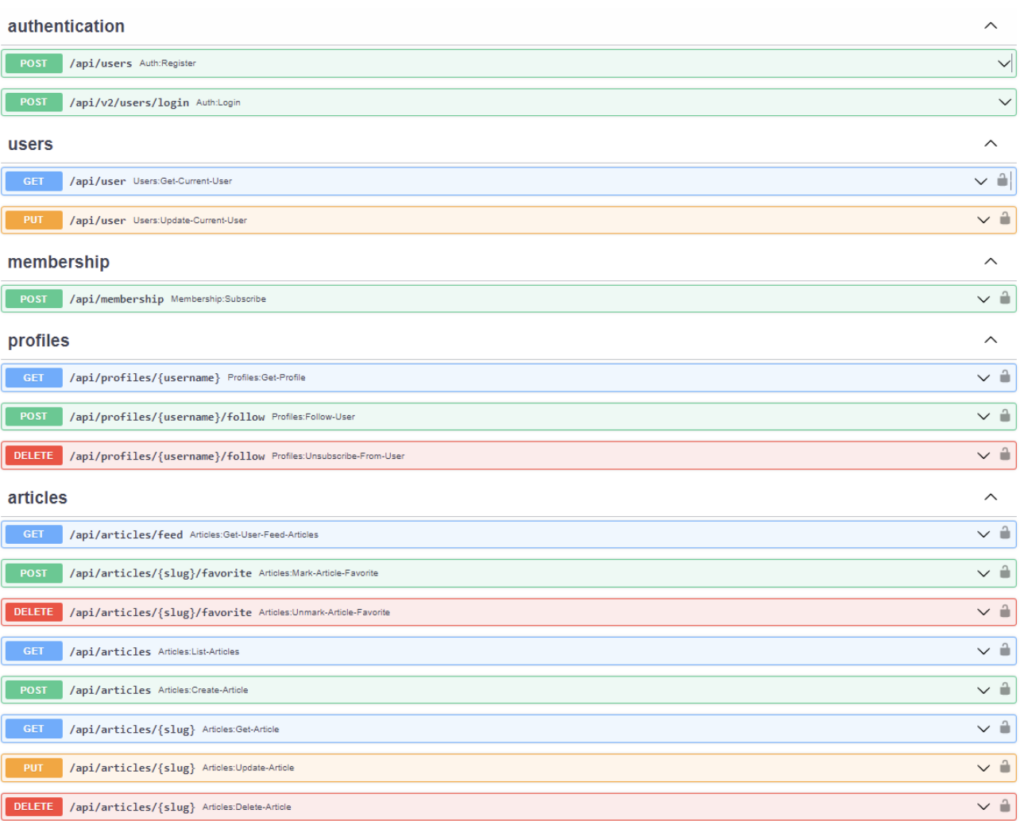
The appliance incorporates 10 dangers that align to the OWASP API High 10 Dangers:
- Damaged Operate Stage Authorization
- Damaged Object Stage Authorization
- Damaged Person Authentication
- Improper API Administration
- Extreme Information Publicity
- Improper Belongings Administration
- Lack of Sources and Price Limiting
- Safety Misconfigurations
- Injection
- Mass Task
- Safety Misconfiguration
- Inadequate Logging
On this weblog, we are going to cowl Damaged Object Stage Authorization (AKA BOLA) and Mass Task problem.
Damaged Object Stage Authorization
Object degree authorization is an entry management mechanism that’s often applied on the code degree to validate that just one consumer can entry objects that they need to have entry to.
Each API endpoint that receives an ID of an object, and performs any kind of motion on the thing, ought to implement object-level authorization checks. The checks ought to validate that the logged-in consumer does have entry to carry out the requested motion on the requested object. Failures on this mechanism usually result in unauthorized info disclosure, modification, or destruction of all information. In easy phrases, BOLA permits a consumer to have entry to fetch/replace/delete any useful resource that they shouldn’t have entry to.
The way to exploit BOLA in a weak utility? Let’s have a look at this instance.
This utility incorporates an article written by “Blastoise”, which publicizes that “Whoever comments first will get 1,000,000$ from Pikachu”. Going into the article, we will see it obtained two feedback as proven beneath:
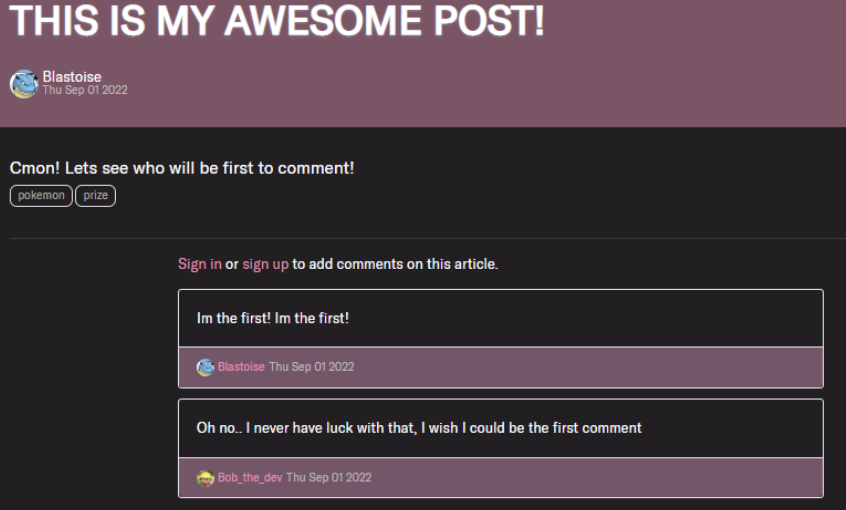
As you may see, “Bob_the_dev” was second to remark on this article, and he wished he was the primary to remark. Let’s reveal how we will make the most of a BOLA vulnerability to make Bob_the_dev #1.
We want to attempt to delete the primary remark of “Blastoise”, an motion which we shouldn’t be capable of carry out if BOLA mitigation is in place.
PoC demonstrating a BOLA exploit:
We efficiently deleted “Blastoise’s” remark whereas being authenticated to a different consumer, which suggests the applying is weak to BOLA and we acquired the flag!
How is Bola allowed within the utility?
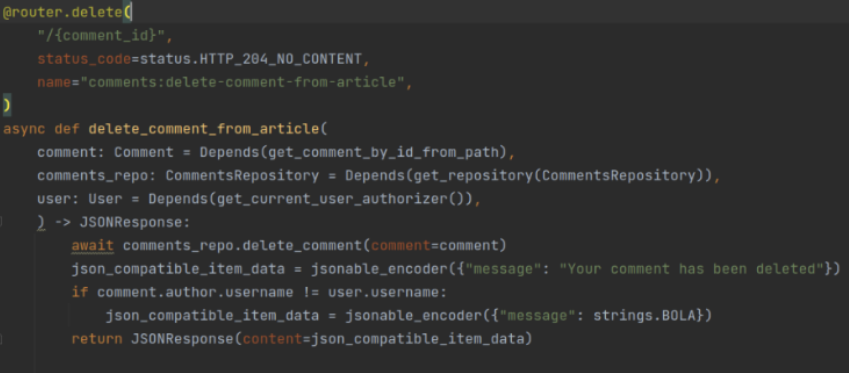
What we will see is a snippet of the applying code, the place the
delete remark routeand
delete_comment_from_article operate is outlined.
We will see the code doesn’t include a verify for the consumer who requests to delete the remark, and due to this fact, any (authenticated) consumer is ready to delete any remark, even when it’s not their very own.
Mitigation
The way in which to mitigate this kind of threat is to have a correct verify of the consumer who tries to entry/replace/delete any useful resource within the utility. In case they aren’t the consumer who ought to have entry to this useful resource, the applying ought to block the request.
if remark.creator != current_user:
elevate HTTPException(
status_code = standing.HTTP_403_FORBIDDEN,
particulars = “Forbidden”
)Mass Task
An API endpoint is weak if it routinely converts shopper parameters into inside object properties, with out contemplating the sensitivity and the publicity degree of those properties. This might enable an attacker to replace object properties that they need to not have entry to.
The way to exploit Mass Task in a weak utility?
When a consumer tries to register/login to the applying, the response the applying returns with incorporates one fascinating discipline that shouldn’t be there—“admin” parameter.
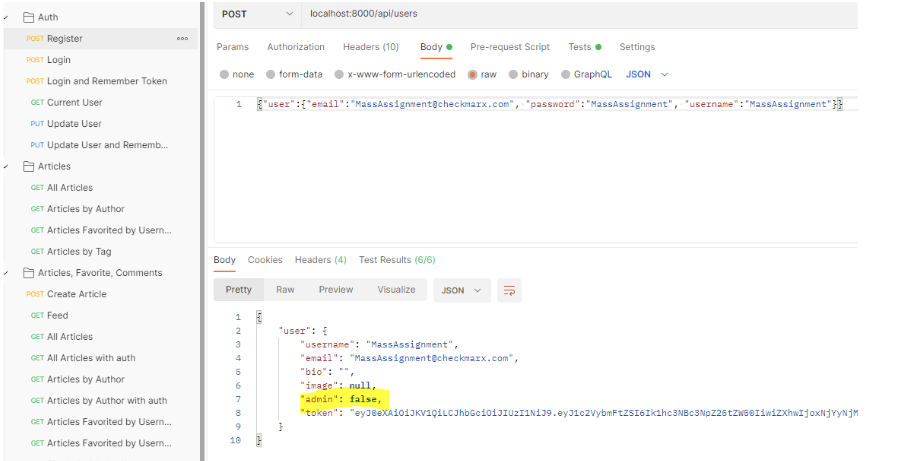
A default consumer within the utility shouldn’t be an admin, so why don’t we attempt to change that?
PoC demonstrating Mass Task exploit:
How is Mass Task allowed within the utility?
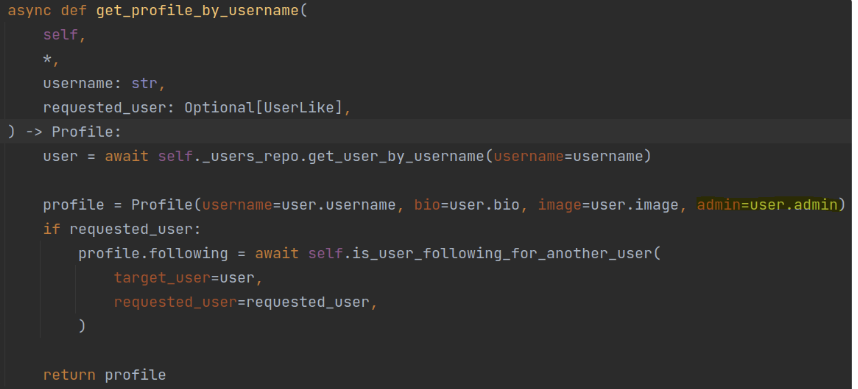
Here’s a snippet of the applying code the place the consumer profile returns the “status” of the consumer by way of admin permissions as a brand new parameter within the response – “admin”. We will see the code doesn’t limit customers from modifying such parameters, so any consumer might replace his profile and modify his admin permissions:
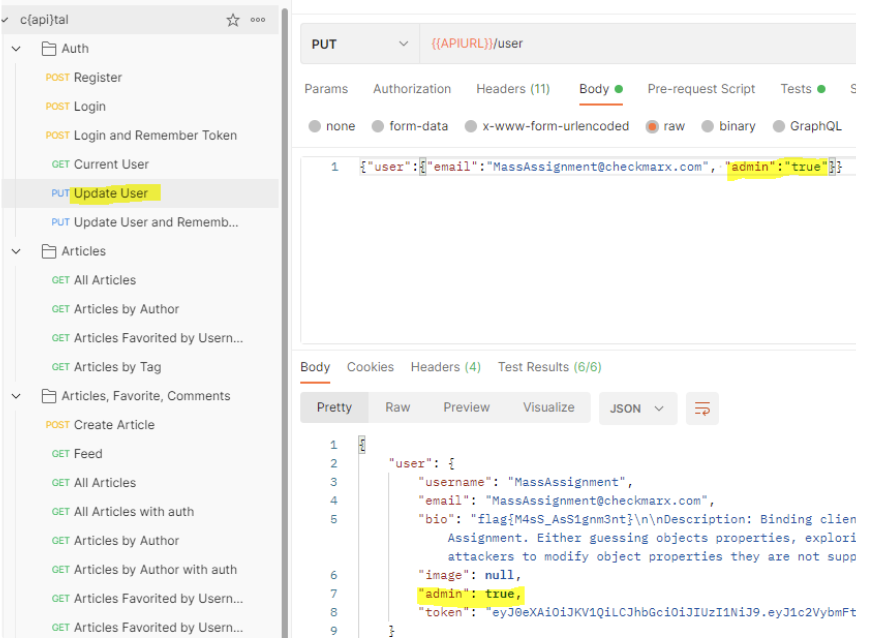
We had been capable of modify the consumer’s permissions and now the consumer is an admin! And within the context of the CTF occasion, after all, we acquired the flag as properly.
Mitigation
The way in which to mitigate such threat is to not expose delicate properties and never enable customers to replace object properties that they need to not have entry to.
Last Ideas
APIs are a essential a part of fashionable cellular, SaaS (Software program as a Service), and net functions and could be present in customer-facing, partner-facing, and inside functions. By nature, APIs expose utility logic and delicate information, doubtlessly resulting in information breaches, account takeovers, and rather more. Due to this, APIs have more and more develop into a goal for attackers.
With out safe APIs, organizations would face many safety dangers and speedy innovation can be not possible. Due to this fact, this can be very necessary to concentrate on the OWASP API High 10 dangers and implement correct API safety mitigations in your APIs.
To assist builders and AppSec groups enhance their API safety abilities, Checkmarx researchers developed c{api}tal, which once more, is a built-to-be-vulnerable API utility primarily based on the OWASP prime 10 API dangers.
Be happy to make use of c{api}tal to study, practice and exploit API Safety vulnerabilities inside your personal API Safety CTF occasion. c{api}tal will quickly be out there as an open-source mission on GitHub! We encourage you all to be proactive and sharpen your API safety and general code safety abilities!
To study extra about Checkmarx strategy to API safety, and general utility safety testing, request a demo of our Checkmarx One™ Utility Safety Platform as we speak. Or join a 14-day free trial right here.