Anybody who administers Linux machines seemingly is aware of safe shell. With out this device, administering these servers remotely could be fairly difficult. It might additionally turn out to be more durable to maneuver information backwards and forwards, no less than with a modicum of safety. That’s the place safe copy comes into play. With the SCP command, you possibly can copy information to and from a distant Linux server by an encrypted SSH tunnel.
SEE: How you can View Your SSH Keys in Linux, macOS, and Home windows
Nonetheless, with the assistance of SSH key authentication, you may make that much more safe. I wish to present you ways you need to use safe key authentication and SCP so you possibly can relaxation assured your information are being moved backwards and forwards securely. I’ll exhibit on an Elementary OS consumer and Ubuntu 16.04.1 server and assume you might have a safe shell put in and dealing.
SSH keys
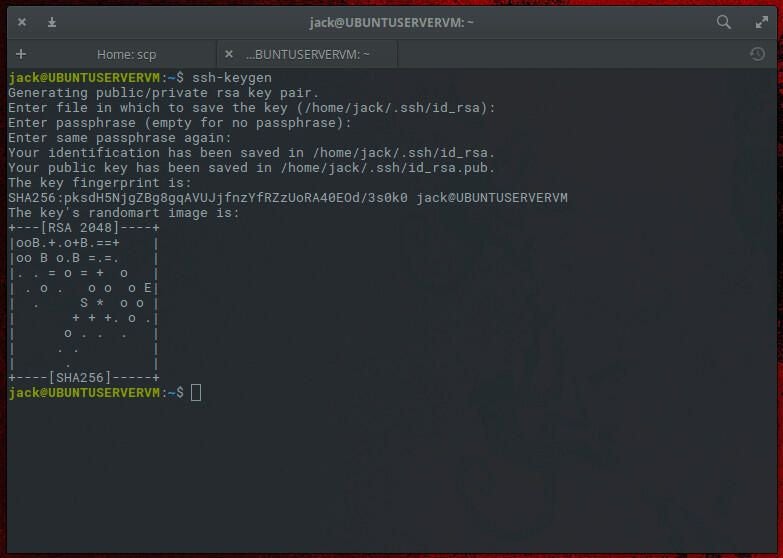
The very first thing that should be accomplished is to create an SSH key pair. To do that, open up a terminal window and problem the command:
ssh-keygen -t rsa
You’ll be requested to call the file (use the default) and provides the keypair a passphrase.
As soon as the important thing’s randomart prints, your key is able to go.
The subsequent step is to repeat the important thing to the distant server. That is accomplished with the command:
ssh-copy-id USER@SERVER
The place USER is the username of the distant server, and SERVER is the deal with of the distant server.
You’ll be prompted for the distant person password. When you efficiently authenticate, the general public key can be copied to the server. You’re able to go.
SEE: Securing Linux coverage (Tech Professional Analysis)
Utilizing SCP together with your key
Now that our keys are in all the proper locations, let’s see how we are able to use them by SCP. Assuming you accepted the default title to your SSH key upon creation, the command to ship a file to your distant server utilizing your SSH secret’s:
scp -i ~/.ssh/id_rsa.pub FILENAME USER@SERVER:/residence/USER/FILENAME
The place FILENAME is the title of the file, USER is the username on the distant machine, and SERVER is the deal with of the distant server.
You need to be prompted for the SSH key password (not the person password). As soon as authenticated, the file can be transferred.
The identical holds true if you must pull a file from the distant server. The construction of that command could be:
scp -i ~/.ssh/id_rsa.pub USER@SERVER:/residence/USER/FILENAME /residence/USER/FILENAME
Once more, you’ll be requested to your SSH key password, and the file can be pulled from the server and copied to the native machine.
SEE: How you can Add an SSH Fingerprint to Your known_hosts File in Linux
Overlook that password
Let’s say you might be about to bear an extended session of copying information to your server. Certain, you may tar all of them up into one greater file. However say they should all be positioned in numerous directories. That’s quite a lot of typing. You can also make this barely extra environment friendly through the use of the ssh-agent and ssh-add instructions.
That’s proper, utilizing the mix of SCP, SSH key authentication, and ssh-agent works nicely. It will preserve you from having to kind that SSH key password each time you problem the SCP command. The one caveat is that it’s essential to keep in mind the PID of the agent session and kill it whenever you’re accomplished.
Right here’s what you must do.
- Earlier than issuing the SCP command problem eval
ssh-agentto begin the session. - Make an observation of the Course of ID you might be given when the session begins.
- Add your SSH key to the session with the command
ssh-add. - Begin utilizing SCP to repeat your information.
That’s all there’s to it. While you’re accomplished with the session, guarantee to problem the command kill PID (the place PID is the precise quantity given to you whenever you began the ssh-agent session with eval).
SEE: 20 fast tricks to make Linux networking simpler (free PDF) (TechRepublic)
Is SCP nonetheless safe?
Somebody asking if SCP is safe has seemingly learn the 2019 launch announcement for OpenSSH 8.0, which acknowledged that the SCP protocol is “outdated, inflexible and not readily fixed” and advisable SFTP and Rsync as options for file switch.
Earlier than OpenSSH 8.0, SCP couldn’t confirm file integrity throughout transfers, leaving customers uncovered to unauthorized overwrites and injection assaults if their server was compromised (CVE-2019-611). Nonetheless, the replace launched stricter filename checking because the default for the SCP command, making it safer, and moved its earlier non-checking conduct to the command scp -T.
Then, in OpenSSH 9.0, launched in 2022, SFTP was adopted because the default backend for SCP as an alternative of the legacy SCP/RCP protocol, which means that transfers are actually encrypted and authenticated with the SSH protocol. Whereas extensively thought to be safe, customers ought to nonetheless be cautious of different dangers like misconfigured servers or outdated software program variations.
What can I take advantage of as an alternative of SCP?
- SFTP: Whereas SCP defaults to utilizing the SFTP protocol, you possibly can think about using native SFTP purchasers for superior file administration because it permits for extra operations, resembling viewing directories and file deletion.
- Rsync: Best for synchronizing information and directories, particularly for incremental backups and huge datasets. See TechRepublic’s information on the way to again up a community utilizing Rsync.
- FTPS: A safe possibility for conventional FTP transfers with SSL/TLS encryption, however it may be advanced to configure.
- HTTPS-based instruments: Resembling
curlorwget, for safe downloads over HTTPS. That is nice for automation, however they don’t present full listing administration like SFTP.
Fiona Jackson up to date this text in January 2025.