COMMENTARY
Greater than half of chief info safety officers (CISOs) battle to successfully talk cyber-risk to their management groups, in keeping with FTI Consulting. In the event you’re a part of this majority, you are not alone. I spend numerous hours every month in dialog with CISOs, speaking about their issues and challenges. Repeatedly, I hear the identical frustration: translating complicated cyber-risks right into a digestible narrative for management is an uphill battle.
The problem is multifaceted:
-
CISOs are competing for consideration in a sea of enterprise dangers. In lots of trendy enterprise organizations, safety groups exist alongside enterprise danger administration (ERM) or governance, danger, and compliance (GRC) groups that observe enterprise danger holistically. Cyber issues are only one merchandise on a prolonged listing of priorities, together with financials, broader financial components, geopolitics, local weather points, and personnel challenges.
-
Conventional danger communication instruments aren’t efficient storytelling automobiles. When ERM or GRC groups evaluation danger with management, they typically current warmth maps that cut back complexity, or danger registers that overwhelm with lots of, if not 1000’s, of strains of content material. In both case, the nuances of cyber-risk get misplaced within the information, which implies that leaders are disconnected from the main points that matter.
-
The stakes are increased than ever. With the typical value of an information breach reaching $4.88 million in 2024, the necessity for clear, compelling danger communication has by no means been extra crucial.
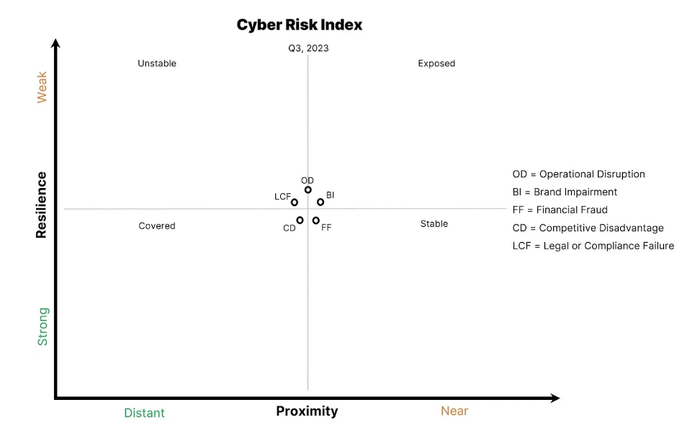
Decoding Cyber-Threat: What Goes Right into a Proximity Resilience Graph
Within the face of rising cyber threats and communication challenges, how can CISOs current their information to management in a clearer, extra compelling means? I like to recommend making a proximity resilience graph — a strong visible device that transforms summary danger information into an interesting, actionable narrative.
Supply: Recorded Future
Let’s break down the elements of the graph to see why it is so helpful:
The Y-axis, labeled Resilience, represents a corporation’s cybersecurity muscle. It encompasses all controls, efforts, plans, processes, applied sciences, and assets, going properly past normal GRC checklists. For instance, think about implementing a gamified phishing coaching program. As worker engagement and resilience towards social engineering enhance, you’d see this mirrored in a downward motion alongside the Y-axis. This axis is essential as a result of it showcases the tangible influence of a corporation’s safety investments and initiatives.
The X-axis, labeled Proximity (as in Assault Proximity), captures the totality of threats surrounding a corporation. When mapping this axis, a CISO ought to use all the safety and menace information out there to them from inner safety telemetry, exterior menace telemetry, and public cyberattack occasions. As an example, if a healthcare firm discovers a spike in ransomware assaults focusing on its sector, assault proximity would shift proper. Equally, if a producing agency’s safety operations heart (SOC) detects a surge in phishing makes an attempt, that inner telemetry sign would transfer proximity to the proper as properly. This axis offers important context, displaying how inner and exterior components affect a corporation’s danger posture.
The graph midlines assist viewers visualize motion, and the highest label is absolutely the reference to anchor time increments. The quantity of motion and the midline labels are versatile, turning it right into a dynamic story that reveals the evolution of a corporation’s safety posture. A CISO ought to select a time phase that is massive sufficient to indicate motion. In the event that they meet quarterly with their board or administrators, they’ll use the beginning of 1 / 4 because the label.
The quadrant labels — Unstable, Secure, Uncovered, and Coated — are easy and expressive, however a CISO can regulate or get rid of them as wanted after seeing their impact on viewers engagement and comprehension.
Lastly, the info factors symbolize the 5 key danger impacts: Operational Disruption, Model Impairment, Monetary Fraud, Aggressive Drawback, and Authorized or Compliance Failure. In the end, the proximity resilience graph offers worth by highlighting motion, displaying whether or not resilience is bettering or getting worse for a selected danger influence. For instance, after a profitable ransomware tabletop train, the Operational Disruption level would shift down on the Y-axis, indicating improved resilience. This granular method permits for nuanced discussions about particular danger areas, relatively than generalizing all cyber-risk.
On the X-axis, menace classes gas danger influence motion, and it is as much as CISOs to translate how menace classes map to varied danger impacts. For instance, a enterprise electronic mail compromise (BEC) primarily creates a Monetary Fraud danger influence, however it may additionally set off Model Impairment if the occasion turns into public.
Bridging the Communication Hole: Construct Your Proximity Resilience Graph
Not solely does a proximity resilience graph supply a extra correct illustration of danger than warmth maps and danger registers, it additionally permits CISOs to inform a fancy story in a single visualization. It avoids subjective labels and permits for various interpretations so leaders can see the place and the way resilience is altering and begin asking knowledgeable questions. It additionally eliminates the possibility of cyber-risk getting misplaced within the noise of broader enterprise danger.
A proximity resilience graph enhances leaders’ danger comprehension and engagement, boosts their confidence within the timing of current and future cybersecurity investments, and improves perceptions of the safety workforce’s worth.