What Occurred?
- Joint analysis of Checkmarx and Illustria resulted with an anomaly found within the open-source ecosystem
- Over 144,000 packages have been revealed to NuGet, NPM, and PyPi by the identical risk actors
- Investigation revealed a brand new assault vector – attackers spam open-source ecosystem with packages containing hyperlinks to phishing campaigns
- All packages and associated person accounts have been most probably created utilizing automation
- The packages share comparable challenge description and auto-generated names
- The risk actors seek advice from retail web sites with referral ids to profit the risk actors with referral rewards
- Our groups disclosed the findings on this report and a lot of the packages have been unlisted
Working Collectively, Maintaining the Ecosystem Protected
The continuing battle towards software program provide chain attackers continues to be difficult as attackers always adapt and shock with new strategies. So as to higher defend towards these threats, Checkmarx and Illustria have joined forces and mixed their analysis efforts. This collaboration led to the invention of a major anomaly within the NuGet, NPM, and PyPi ecosystems.
NuGet Anomalies
Our know-how collects and indexes proof associated to packages from all open-source ecosystems, permitting us to question historic information for brand spanking new insights and uncover suspicious actions by a course of we name “retro-hunting.”
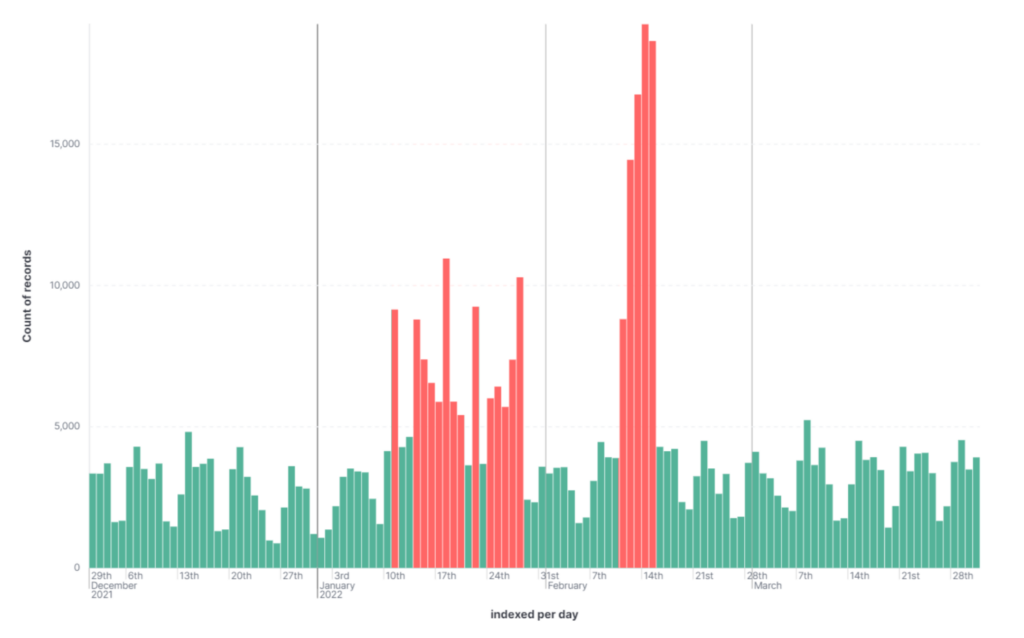
A couple of months in the past, we found an anomaly within the NuGet ecosystem once we cross-referenced new data with our databases. Clusters of packages had been revealed in massive portions to the NuGet bundle supervisor. Additional investigation revealed that the packages have been a part of a brand new assault vector, with attackers spamming the open-source ecosystem with packages containing hyperlinks to phishing campaigns.
On this state of affairs, plainly automated processes have been used to create over 135,000 packages in NuGet and associated person accounts. The descriptions for these packages contained hyperlinks to phishing campaigns. Our groups alerted the NuGet safety group, and so they replied that the packages have been unlisted to guard customers of the open-source ecosystem.
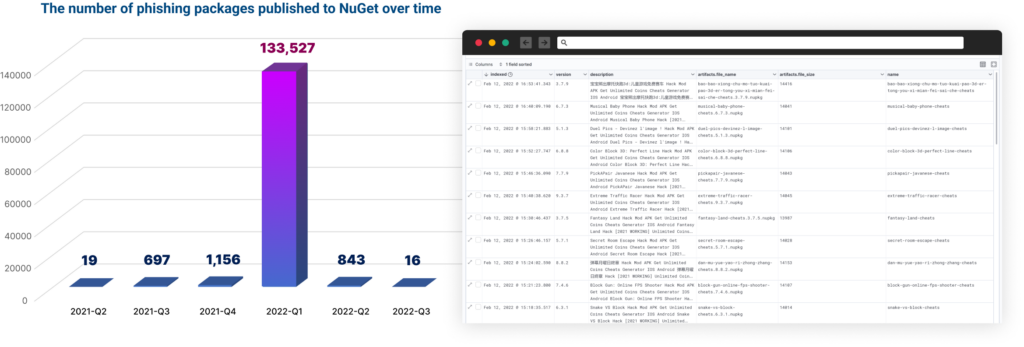
After investigating the NuGet anomaly with the creation of over 135,000 packages and associated person accounts, we found that comparable exercise had additionally taken place in NPM and PyPi.
A complete of 144,294 phishing-related packages have been detected, all of which have been created by the identical risk actor. Of those, 136,258 have been revealed on NuGet, 212 on NPM, and seven,824 on PyPi
Automated Packages and Consumer Accounts
The big scale of the NuGet bundle publication and the patterns within the person accounts counsel that the method was automated. Most of the usernames adopted the sample “<a-z><1900-2022>”, and lots of customers had revealed the identical variety of packages. Our group disclosed this data to the NuGet safety group, who unlisted the packages from NuGet’s search outcomes. Whereas the packages are now not simply accessible, their net pages are nonetheless out there on NuGet’s web site, and the packages can nonetheless be downloaded from these pages. Relating to the opposite ecosystems, the packages have been taken down.
Phishing Websites in Bundle Description
The attackers used numerous packages with names associated to hacking, cheats, and free sources to advertise their phishing marketing campaign. A number of the bundle names included “free-steam-codes-generator,” “yalla-ludo-diamond-hack,” “a3-still-alive-hack-diamonds”, and “project-makeover-hack-gems.” These names have been designed to lure customers into downloading the packages and clicking on the hyperlinks to the phishing websites.
The descriptions of all of the packages we discovered contained hyperlinks to phishing websites. The risk actors behind this marketing campaign probably wished to enhance the SEO (website positioning) of their phishing websites by linking them to reputable web sites like NuGet. This highlights the should be cautious when downloading packages and solely to make use of trusted sources.
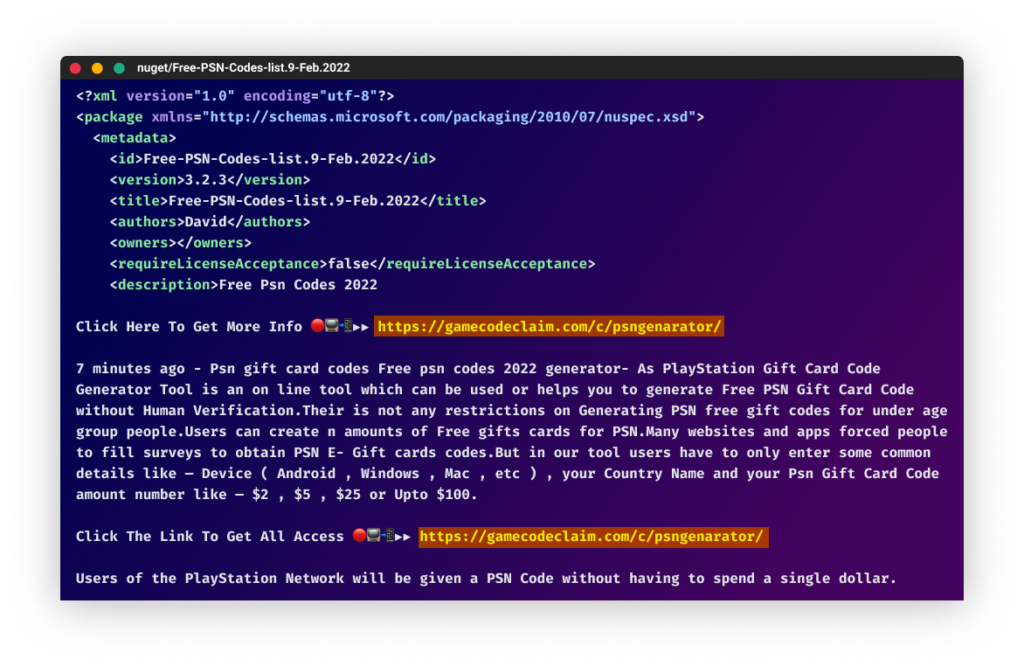
The messages in these packages try to entice readers into clicking hyperlinks with guarantees of sport cheats, free sources, and elevated followers and likes on social media platforms like TikTok and Instagram.
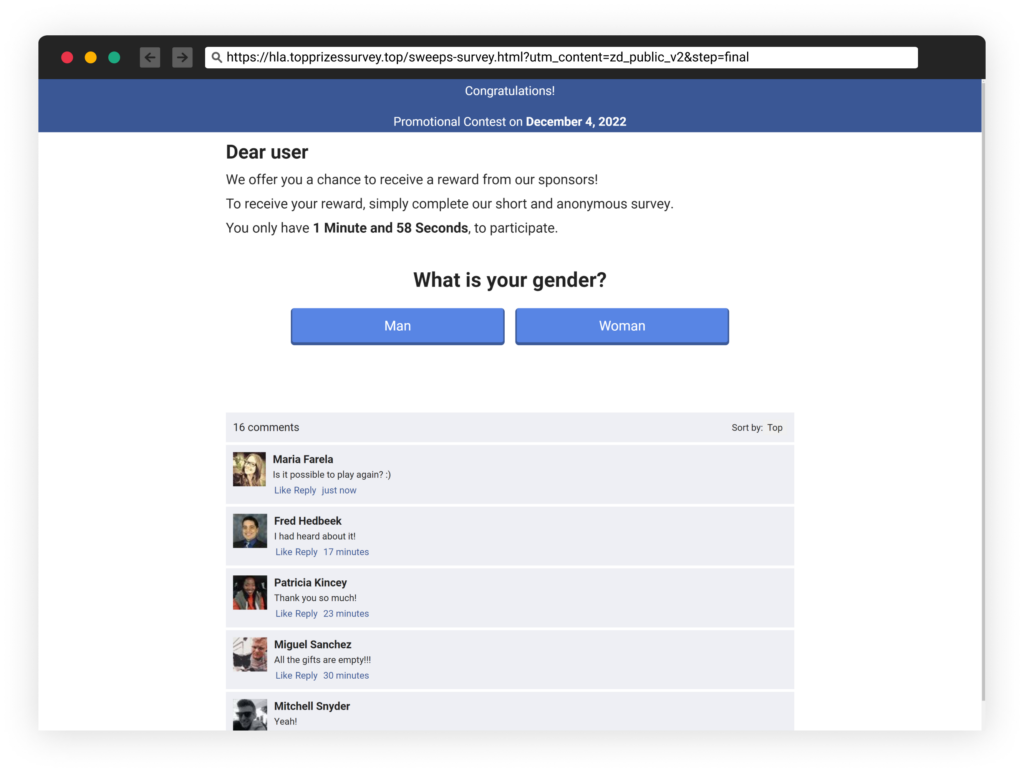
The phishing marketing campaign linked to over 65,000 distinctive URLs on 90 domains, with every area internet hosting a number of phishing webpages below totally different paths. The misleading webpages are well-designed and, in some circumstances, even embrace faux interactive chats that seem to indicate customers receiving the cheats or followers they have been promised.
These chats will even reply to messages if the reader chooses to take part, however these are all automated and fabricated. This highlights the necessity for warning when interacting with hyperlinks in packages and the significance of solely utilizing trusted sources.

The web sites included built-in faux circulation that pretended to course of information and generate the promised “gifts.” Nonetheless, this course of more often than not failed, and the sufferer was then requested to enter a “human verification” part that concerned a number of websites referring the person from one to a different. These websites included surveys that requested the person to reply to numerous questions, resulting in extra surveys or finally to reputable eCommerce web sites. This reveals the significance of being cautious when interacting with hyperlinks in packages and solely utilizing trusted sources.
Referrals Rewards
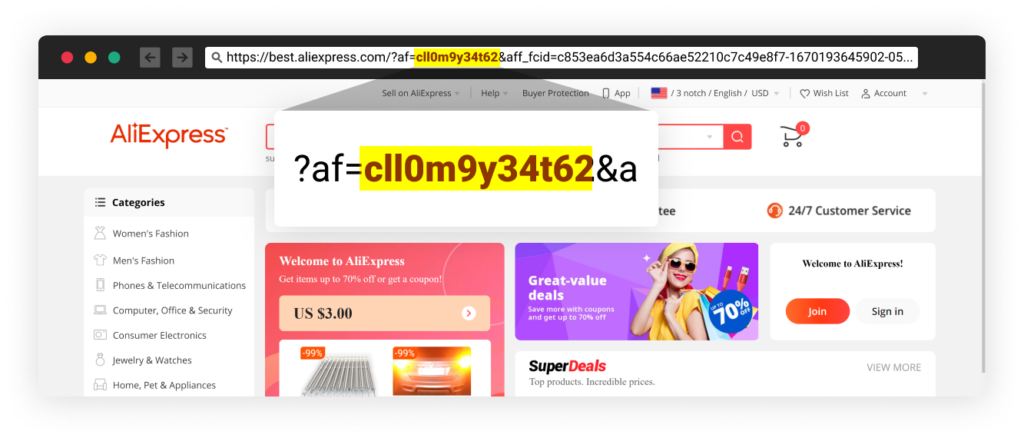
Whereas investigating the phishing web sites, we observed that a few of them redirected to eCommerce web sites with referral IDs. For instance, one among our experiments resulted in being redirected to AliExpress, one of many world’s largest on-line retail platforms. Like many different retail web sites, AliExpress affords a referral program that rewards members for referring new clients to the platform.
If the risk actors refer their victims to AliExpress and so they make a purchase order, the risk actors’ account will obtain a referral reward within the type of a coupon or retailer credit score. This highlights the potential monetary acquire for risk actors who have interaction in phishing campaigns like this one.
Conclusion
These attackers invested in automation in an effort to poison your complete NuGet, PyPi, and NPM ecosystem with 144,294 packages. This allowed them to publish numerous packages in a brief time frame, making it tough for the totally different safety groups to establish and take away the packages rapidly. Automating the method additionally allowed the attackers to create numerous person accounts, making it tough to hint the supply of the assault. This reveals the sophistication and willpower of those attackers, who have been keen to speculate important sources in an effort to perform this marketing campaign.
The battle towards risk actors poisoning our software program provide chain ecosystem continues to be a difficult one, as attackers always adapt and shock with new and surprising strategies.
So as to higher defend towards these threats, Checkmarx and Illustria have teamed as much as mix their analysis efforts. This collaboration led to the invention of a major anomaly within the NuGet ecosystem.
By working collectively, we will keep one step forward of attackers and maintain the ecosystem protected. We consider this type of collaboration is essential within the combat towards software program provide chain assaults, and we’ll proceed working collectively to guard the open-source ecosystem.
Checklist of Packages
The dimensions of this phishing marketing campaign is important, and you’re welcome to obtain the total dataset hosted on GitHub Gist (11mb)
This can help you additional analyze the information and acquire a greater understanding of the scope and nature of the assault.
If you need entry to the unique metadata or samples from this phishing marketing campaign, please be happy to ship an electronic mail to [email protected]. Our group will likely be blissful to offer you the data you want.
IOC
In complete, we analyzed over 65,000 distinctive URLs (click on to get the total listing), which we have been in a position to cut back to roughly 90 domains. (A hyperlink to the total listing is supplied.) This reveals the dimensions of the phishing marketing campaign and the trouble that was required to establish and analyze all the URLs concerned.
- tinybit[.]cc
- gamecoins[.]codes
- gamecodeclaim[.]com
- gamesapp[.]professional
- playersworld[.]xyz
- lucymods[.]com
- redirekt[.]in
- rebrand[.]ly
- gluegames[.]xyz
- igetforfree[.]com
- techdoy[.]com
- gamemasters[.]xyz
- fabgames[.]xyz
- knightmods[.]com
- gamehunters[.]win
- getfreegem[.]com
- betabuff[.]xyz
- gamesconquest[.]xyz
- gamersahead[.]com
- gamedip[.]xyz
- bizgames[.]xyz
- gamedips[.]xyz
- gamedips[.]com
- tapasgaming[.]xyz
- iwantforfree[.]com
- gainforfree[.]com
- bigmouse[.]membership
- flamingame[.]com
- codesrbx[.]com
- free-albums[.]org
- lootcodes[.]com
- madgames[.]xyz
- gopremium[.]win
- giftboxfree[.]com
- cheersgamers[.]com
- gamervalvet[.]com
- gamesflow[.]xyz
- nastygames[.]xyz
- gameysky[.]xyz
- buxx[.]web site
- gamerblind[.]com
- gamemasters[.]xyz
- gamecodeclaim[.]com
- wikiredeem[.]com
- codefy[.]xyz
- gaminghorn[.]com
- hackcheatsgenerators[.]com
- coub[.]com
- wbld[.]xyz
- arcades[.]tech
- gamerscrew[.]xyz
- kaciestarrtriplett[.]com
- gopremium[.]win
- vipgamesgen[.]com
- freerobux[.]greatest
- rbxt[.]web site
- boom-beach-free-diamonds[.]com
- gamecheats[.]win
- dragon-city-free-gems[.]com
- getfortskins[.]com
- unlocker[.]cc
- webstoreusa[.]internet
- sbld[.]xyz
- newsdashes[.]com
- chatgamings[.]com
- m[.]vegas7games[.]com
- giftcardsking[.]xyz
- nancymarkle[.]com
- g4ming[.]cc
- justpremium[.]xyz
- kachifpro[.]information
- ocean-of-hacks[.]com
- appmobileforce[.]com
- gemtoon[.]com
- cheersgamers[.]compubg
- techiesbay[.]com
- supergame100[.]com
- vegas7games[.]professional
- windmod[.]icu
- gamerslab[.]org
- smash[.]gg
- bandicam[.]com
- onergfx[.]xyz
- wefunder[.]com
- flamingame[.]comproject
- gadgets[.]by
- gametown[.]xyz
- gainforfree[.]compubg
- imv[.]quest
- spotifyplus[.]professional
- thenewsref[.]com
- correlsense[.]com
- instagramhackonline[.]com