A just lately mounted “Windows MSHTML spoofing vulnerability” tracked beneath CVE-2024-43461 is now marked as beforehand exploited after it was utilized in assaults by the Void Banshee APT hacking group.
When first disclosed as a part of the September 2024 Patch Tuesday, Microsoft had not marked the vulnerability as beforehand exploited. Nonetheless, on Friday, Microsoft up to date the CVE-2024-43461 advisory to point it had been exploited in assaults earlier than it was mounted.
The flaw’s discovery was attributed to Peter Girnus, a Senior Menace Researcher at Pattern Micro’s Zero Day, who informed BleepingComputer that the CVE-2024-43461 flaw was exploited in zero-day assaults by Void Banshee to put in information-stealing malware.
Void Banshee is an APT hacking group first tracked by Pattern Micro that targets organizations in North America, Europe, and Southeast Asia to steal knowledge and for monetary acquire.
The CVE-2024-43461 zero-day
In July, Test Level Analysis and Pattern Micro each reported on the identical assaults that exploited Home windows zero-days to infect gadgets with the Atlantida info-stealer, used to steal passwords, authentication cookies, and cryptocurrency wallets from contaminated gadgets.
The assaults utilized zero-days tracked as CVE-2024-38112 (mounted in July) and CVE-2024-43461 (mounted this month) as a part of the assault chain.
The invention of the CVE-2024-38112 zero-day was attributed to Test Level researcher Haifei Li, who says it was used to pressure Home windows to open malicious web sites in Web Explorer relatively than Microsoft Edge when launching specifically crafted shortcut information.
“Specifically, the attackers used special Windows Internet Shortcut files (.url extension name), which, when clicked, would call the retired Internet Explorer (IE) to visit the attacker-controlled URL,” defined Li in a July Test Level Analysis report.
These URLs had been used to obtain a malicious HTA file and immediate the person to open it. When opened, a script would run to put in the Atlantida info-stealer.
The HTA information utilized a unique zero-day tracked as CVE-2024-43461 to cover the HTA file extension and make the file seem as a PDF when Home windows prompted customers as as to if it needs to be opened, as proven beneath.
ZDI researcher Peter Girnus informed BleepingComputer that the CVE-2024-43461 flaw was additionally used within the Void Banshee assaults to create a CWE-451 situation via HTA file names that included 26 encoded braille whitespace characters (%E2percentA0percent80) to cover the .hta extension.
As you may see beneath, the file title begins as a PDF file however contains twenty-six repeated encoded braille whitespace characters (%E2percentA0percent80) adopted by a remaining ‘.hta’ extension.
Books_A0UJKO.pdfpercentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80percentE2percentA0percent80.hta
When Home windows opens this file, the braille whitespace characters push the HTA extension exterior the person interface, solely delineated by a ‘…’ string in Home windows prompts, as seen beneath. This brought about the HTA information to seem as PDF information, making them extra prone to be opened.
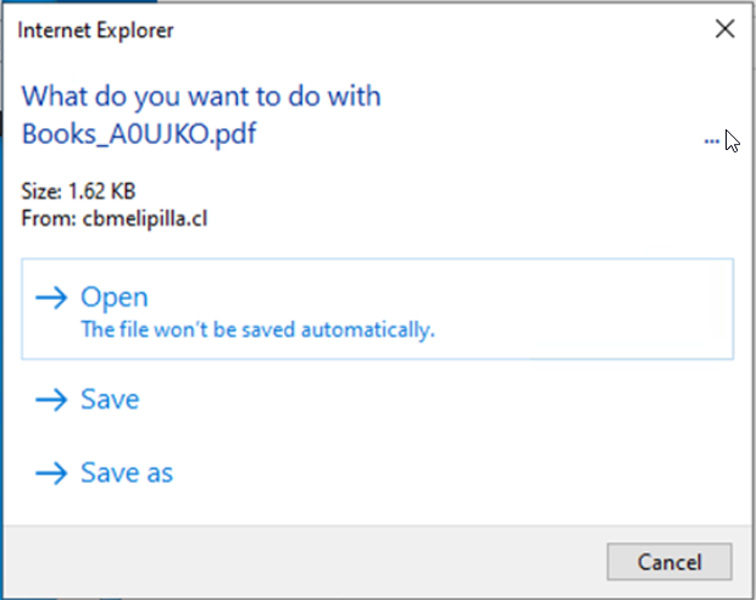
Supply: Pattern Micro
After putting in the safety replace for CVE-2024-43461, Girnus says the whitespace is just not stripped, however Home windows now reveals the precise .hta extension for the file in prompts.
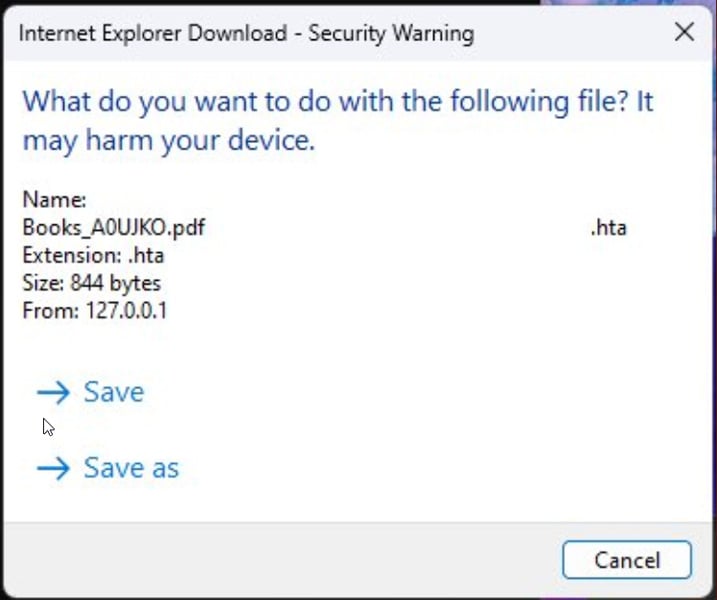
Supply: Peter Girnus
Sadly, this repair is just not excellent, because the included whitespace will probably nonetheless confuse folks into pondering the file is a PDF relatively than an HTA file.
Microsoft mounted three different actively exploited zero-days within the September Patch Tuesday, together with CVE-2024-38217, which was exploited in LNK stomping assaults to bypass the Mark of the Net safety function.
