Financially motivated cybercriminals abuse the Home windows Fast Help function in social engineering assaults to deploy Black Basta ransomware payloads on victims’ networks.
Microsoft has been investigating this marketing campaign since not less than mid-April 2024, and, as they noticed, the menace group (tracked as Storm-1811) began their assaults by electronic mail bombing the goal after subscribing their addresses to varied electronic mail subscription companies.
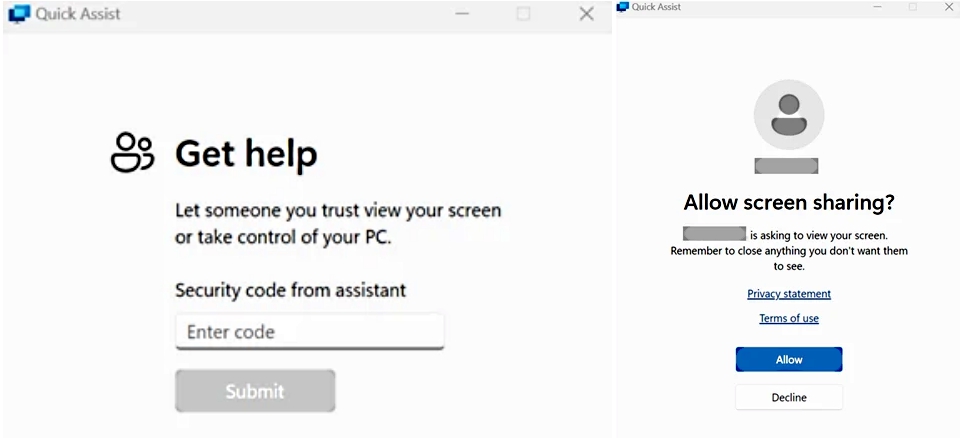
As soon as their mailboxes flood with unsolicited messages, the menace actors name them whereas impersonating a Microsoft technical assist or the attacked firm’s IT or assist desk workers to assist remediate the spam points.
Throughout this voice phishing assault, the attackers trick the victims into granting them entry to their Home windows gadgets by launching the Fast Help built-in distant management and screen-sharing device.
“Once the user allows access and control, the threat actor runs a scripted cURL command to download a series of batch files or ZIP files used to deliver malicious payloads,” Microsoft stated.
“In several cases, Microsoft Threat Intelligence identified such activity leading to the download of Qakbot, RMM tools like ScreenConnect and NetSupport Manager, and Cobalt Strike.”
After putting in their malicious instruments and concluding the cellphone name, Storm-1811 performs area enumeration, strikes laterally by way of the sufferer’s community, and deploys Black Basta ransomware utilizing the Home windows PsExec telnet-replacement device.
Cybersecurity firm Rapid7, which additionally noticed the assaults, says the malicious actors will use “a batch script to harvest the victim’s credentials from the command line using PowerShell.”
“The credentials are gathered under the false context of the ‘update’requiring the user to log in. In most of the observed batch script variations, the credentials are immediately exfiltrated to the threat actor’s server via a Secure Copy command (SCP),” Rapid7 added.
“In at least one other observed script variant, credentials are saved to an archive and must be manually retrieved.”
To dam these social engineering assaults, Microsoft advises community defenders to dam or uninstall Fast Help and comparable distant monitoring and administration instruments if they don’t seem to be used and to coach staff to acknowledge tech assist scams.
These focused in these assaults ought to solely permit others to connect with their gadget in the event that they contacted their IT assist personnel or Microsoft Help and instantly disconnect any Fast Help classes if they believe malicious intent.
The Black Basta ransomware operation
After the Conti cybercrime group shut down two years in the past following a collection of embarrassing information breaches, it broke up into a number of factions, considered one of which is believed to be Black Basta.
Black Basta surfaced as a Ransomware-as-a-Service (RaaS) operation in April 2022. Since then, its associates have breached many high-profile victims, together with German protection contractor Rheinmetall, U.Ok. know-how outsourcing firm Capita, Hyundai’s European division, the Toronto Public Library, the American Dental Affiliation, industrial automation firm and authorities contractor ABB, Sobeys, Knauf, and Yellow Pages Canada.
Extra not too long ago, Black Basta was linked to a ransomware assault that hit U.S. healthcare big Ascension, forcing it to divert ambulances to unaffected amenities.
As CISA and the FBI revealed in a joint advisory final week, Black Basta ransomware associates have breached greater than 500 organizations between April 2022 and Could 2024, encrypting and stealing information from not less than 12 out of 16 vital infrastructure sectors.
Well being-ISAC (Info Sharing and Evaluation Heart) additionally warned in a menace bulletin that the ransomware gang “has recently accelerated attacks against the healthcare sector.”
In keeping with cybersecurity firm Elliptic and cyber insurance coverage agency Corvus Insurance coverage analysis, Black Basta has collected not less than $100 million in ransom funds from over 90 victims till November 2023.
