Adversaries typically use complicated, multi-stage cloud assaults that evade conventional safety measures, which battle to totally visualize, prioritize, and reply to threats. Multi-domain correlation addresses this by analyzing knowledge throughout numerous domains — together with networks, purposes, databases, and storage — to uncover potential weaknesses and assault paths throughout interconnected assets.
This method enhances safety posture, offering holistic menace detection and response capabilities in as we speak’s complicated cloud surroundings.
Challenges for multi-domain correlation
stability between safety, compliance, and operational effectivity is required for multi-domain correlation. Nevertheless, a couple of challenges forestall organizations from reaching this end-to-end visibility throughout their cloud property.
Distributed infrastructure
Bigger and hybrid cloud environments want dearer applied sciences. Processing and correlating huge quantities of knowledge throughout domains like id, endpoints, companies, knowledge sources, community, and purposes is computationally costly. For instance, non-native integrations produce logs with various knowledge codecs and semantics. If poorly configured, the integrations could fail to ingest the correct knowledge that enrich cross-domain detections, velocity up investigation metrics, and prioritize dangers.
Siloed applied sciences
Siloed applied sciences function throughout completely different area sorts and forestall a complete view of a corporation’s cloud property. These fragmented options apply inconsistent safety insurance policies throughout the cloud, thereby rising the general threat profile. For instance, a misconfigured id could assign extreme permissions and inadvertently enable an insider menace actor to bypass safety guidelines, function in plain sight, and transfer laterally throughout cloud accounts. When an incident is detected, safety groups are compelled to waste precious minutes correlating knowledge from a number of alerts, dashboards, and logs.
Compliance and governance
Compliance necessities will be complicated and nuanced. Sure laws have strict necessities round knowledge privateness and dealing with of delicate data. These laws could limit shifting or combining knowledge from completely different geographic areas or enterprise models. For instance, various knowledge safety legal guidelines like NIS2, DORA, GDPR, and HIPAA restrict the flexibility to freely correlate knowledge throughout domains. Many organizations discover it tough to maintain tempo with the altering frameworks, audit each correlation rule, and guarantee their compliance checks are updated throughout all domains.
Constructing blocks for multi-domain correlation
Multi-domain correlation requires a scientific method to combine knowledge from numerous sources – resembling community logs, id and entry administration (IAM) logs, utility occasions, and endpoint behaviors – with a view to detect safety threats, implement compliance, and streamline incident response.
Centralized platform
Organizations typically depend on a mixture of cloud-native and third-party companies to gather, combination, and analyze knowledge from numerous cloud environments. There are a number of advantages of a unified platform:
- Allows safety groups to gather knowledge, analyze it, and correlate key knowledge factors to establish and deal with dangerous combos
- Enhances multi-domain correlation by offering a transparent, interactive view of safety occasions and patterns as they unfold
- Facilitates steady tuning and optimization of correlation guidelines to make sure their accuracy, scale back false positives, and enhance the system’s skill to detect true safety incidents throughout numerous cloud domains
- Consolidates options which might be innately appropriate and seamlessly integrates them with out overhead prices
- Fosters a coordinated response to incidents throughout groups, bettering communication and collaboration
Cloud APIs for knowledge ingestion
Cloud APIs for knowledge ingestion are important as a result of they supply a structured, scalable, and real-time technique for aggregating knowledge throughout multi-domain infrastructure, permitting for a centralized view throughout hybrid or multi-cloud setups. By way of APIs, safety groups can extract, normalize, and analyze knowledge from a number of sources to attain complete visibility and detect complicated, multi-stage safety incidents early within the assault chain.
Agent and agentless monitoring
For sturdy multi-domain correlation, each agent-based and agentless monitoring supplies complete protection and insights into safety occasions that span throughout a number of cloud domains. For instance, an agent could detect a privilege escalation on an endpoint, whereas agentless IAM monitoring detects a change in consumer position. Collectively, they recommend potential insider threats or lateral motion.
Synthetic intelligence for anomaly detection
Leveraging AI or machine studying for anomaly detection within the cloud permits extra correct and environment friendly identification of complicated threats. For instance, well-trained machine studying fashions are tuned to distinguish between true threats and benign anomalies, detect uncommon patterns that conventional rule-based strategies may miss, and speed up incident response with context-rich insights for each detected incident.
Automate response and mitigation
Automated response and mitigation eliminates the danger of human errors in menace investigations and ensures that the response actions are constant, repeatable, and dependable throughout all domains. In multi-cloud or hybrid infrastructures, these automated responses enable for scalable operations, lowering the time it takes to deal with potential incidents.
Obtain multi-domain correlation with Sysdig
Sysdig gives a centralized platform to carry out multi-domain correlation within the cloud, integrating knowledge from numerous sources and domains throughout cloud infrastructure, purposes, and container environments. This know-how focuses on multi-cloud, cloud-native, and containerized environments to supply visibility throughout a number of layers, resembling community, workload, utility, and consumer entry.
Under are some standard use circumstances:
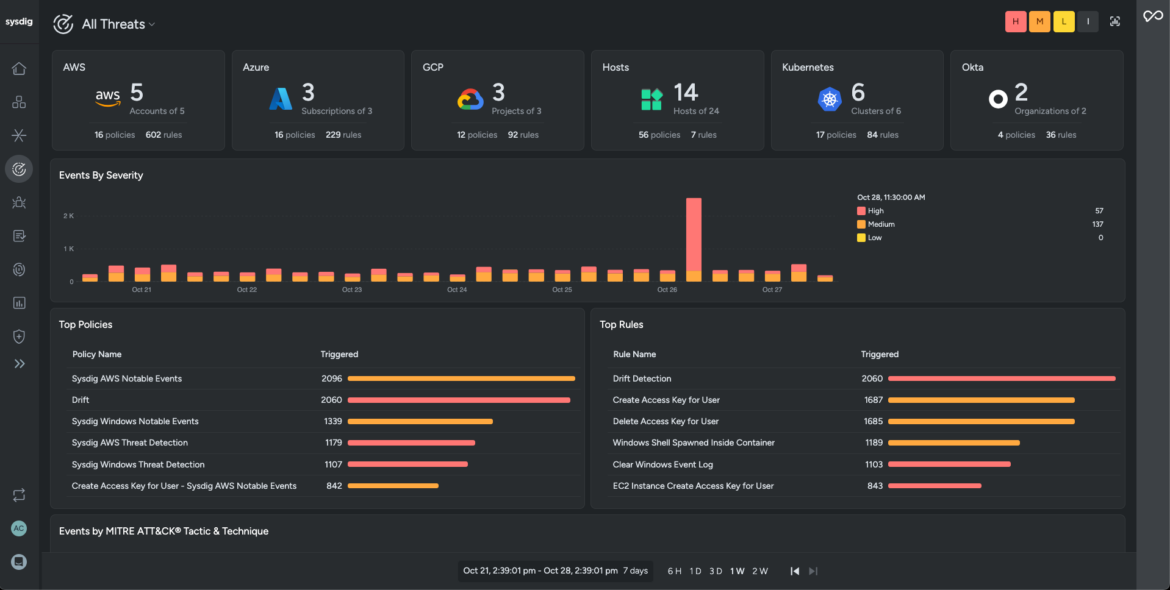
- The Sysdig platform ingests, aggregates, and analyzes safety knowledge in a centralized location to offer a single pane of glass view of your multi-cloud or hybrid infrastructure.
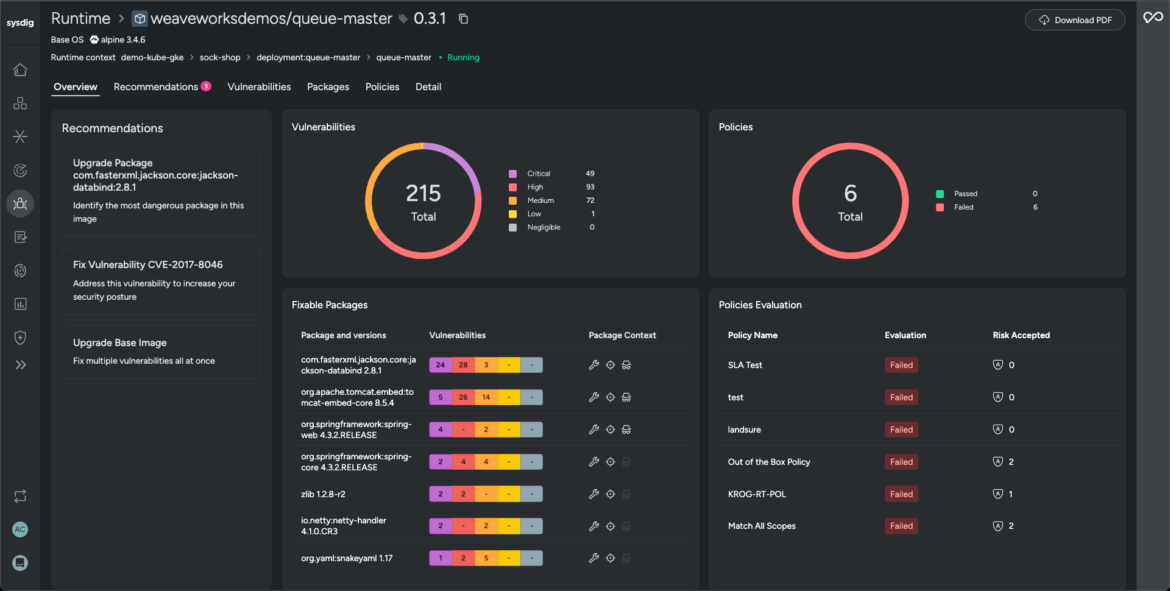
- Sysdig’s layered evaluation strengthens safety posture by offering a granular view of your container photographs right down to the OS degree. It helps organizations to visualise pre-existing gaps, handle vulnerabilities, and deal with them with guided suggestions.
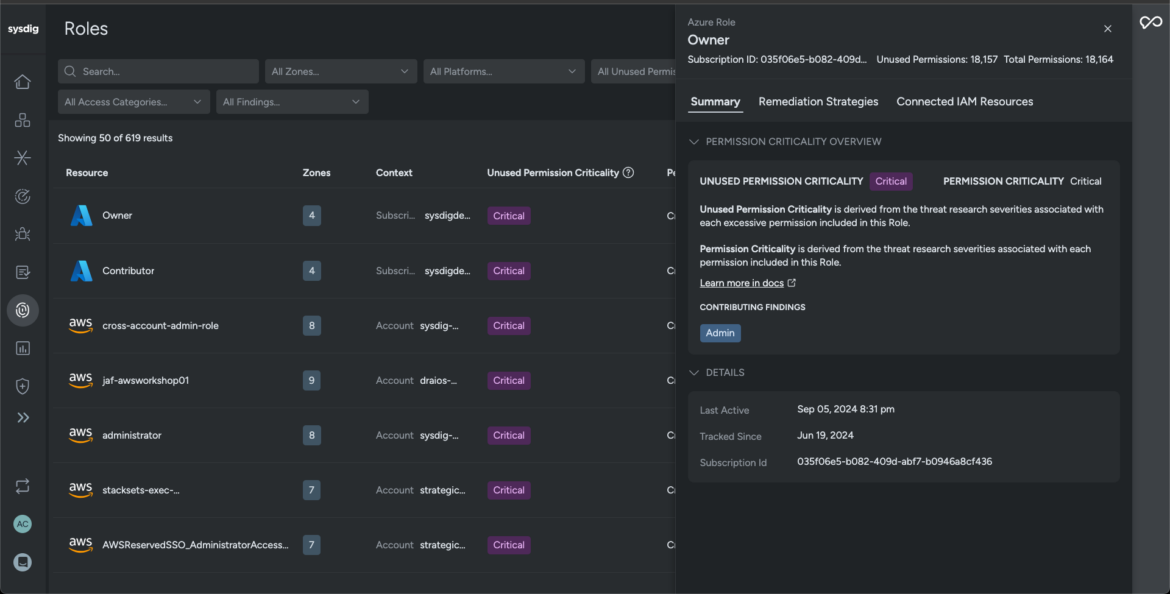
- Sysdig’s context-rich perception helps safety groups establish and remediate compromised identities, teams, and consumer roles accountable within the occasion of a safety breach.
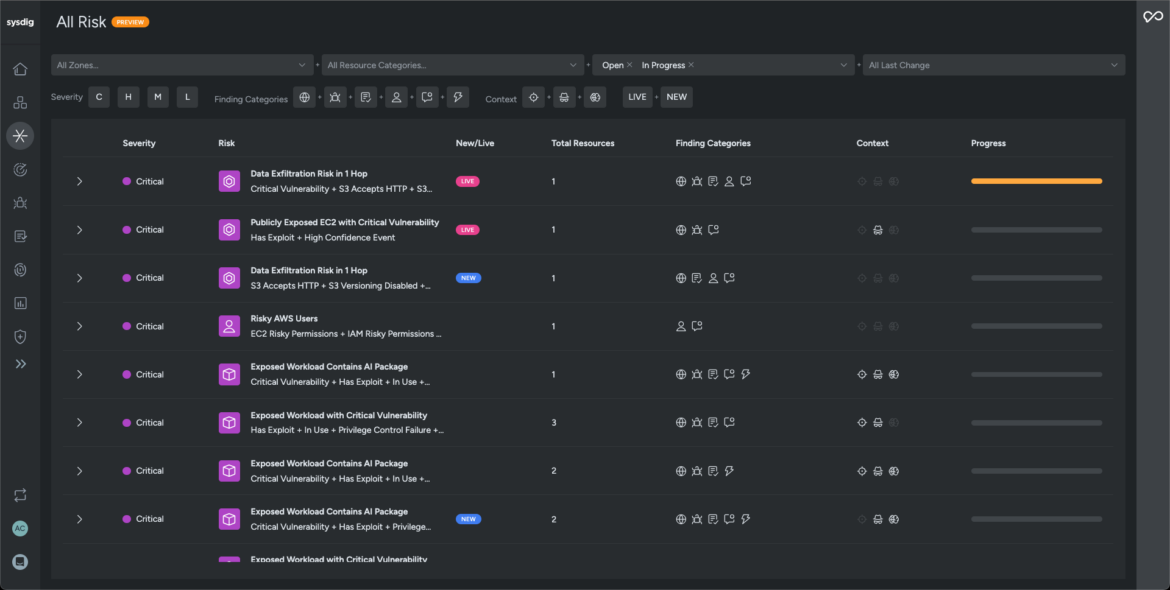
- Sysdig helps visualize and perceive potential dangers throughout compute, id, Kubernetes, and storage assets,; correlate these dangers with real-time occasions,; and pinpoint essential paths that malicious actors may take to breach their techniques. These dangers are periodically reevaluated and re-prioritized primarily based on the findings in your infrastructure.
- Sysdig clients establish and mitigate superior threats throughout cloud environments by integrating real-time menace detection and customizable Falco guidelines, and leveraging machine studying insurance policies for anomaly detection.
Not too long ago launched cloud detection and response (CDR) options, like AWS Behavioral Analytics, Assault Chain Visualization, Cloud Identification Insights, and Sysdig SageTM, simplify safety workflows by automating the prioritization of occasions, contextualizing dangers, and suggesting actionable remediation steps.
Instance situation
Compromised container detection
Situation: A containerized utility reveals uncommon course of exercise, spawning a shell in a privileged mode and initiating an exterior community connection.
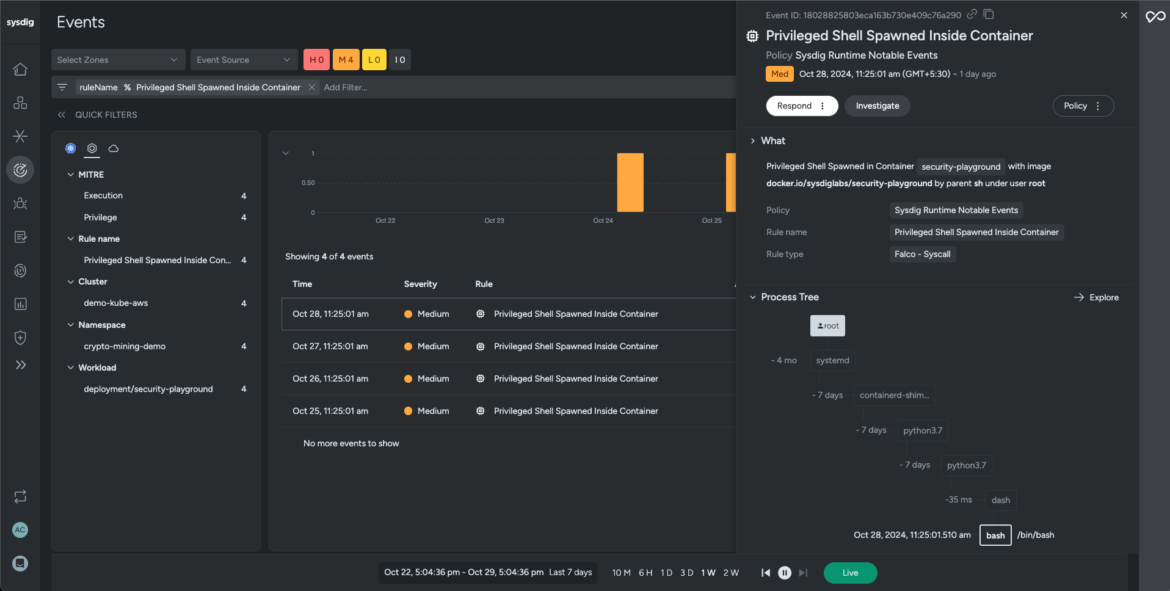
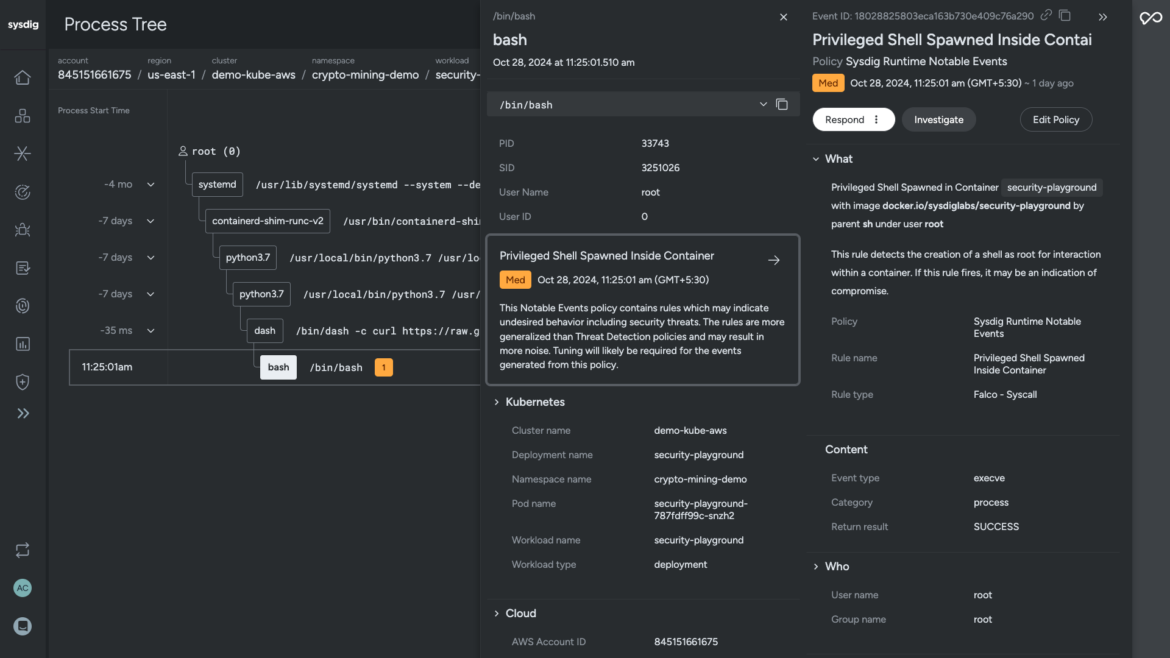
Sysdig’s Falco rule detects the shell spawned as root within the container (workload area). The method tree traces out the timeline of executed command strains captured by the agent at runtime. It illustrates the kill chain from consumer to course of, together with course of lineage, container and host data, malicious consumer particulars, and affect.
Sysdig supplies a graphical overview of the assault path. It correlates and consolidates knowledge from a number of sources — together with posture misconfigurations, current vulnerabilities, launched processes, and exercise audits — to judge the affect of the continuing menace. At a look, you’ll achieve essential understanding of the occasion’s context, resembling:
- What was the basis reason for the occasion?
- What different techniques has the menace actor accessed which may be in danger?
- What processes and instructions have been run on the impacted workloads?
- What vulnerabilities or misconfigured permissions are in use?
- What permissions and identities have been elevated?
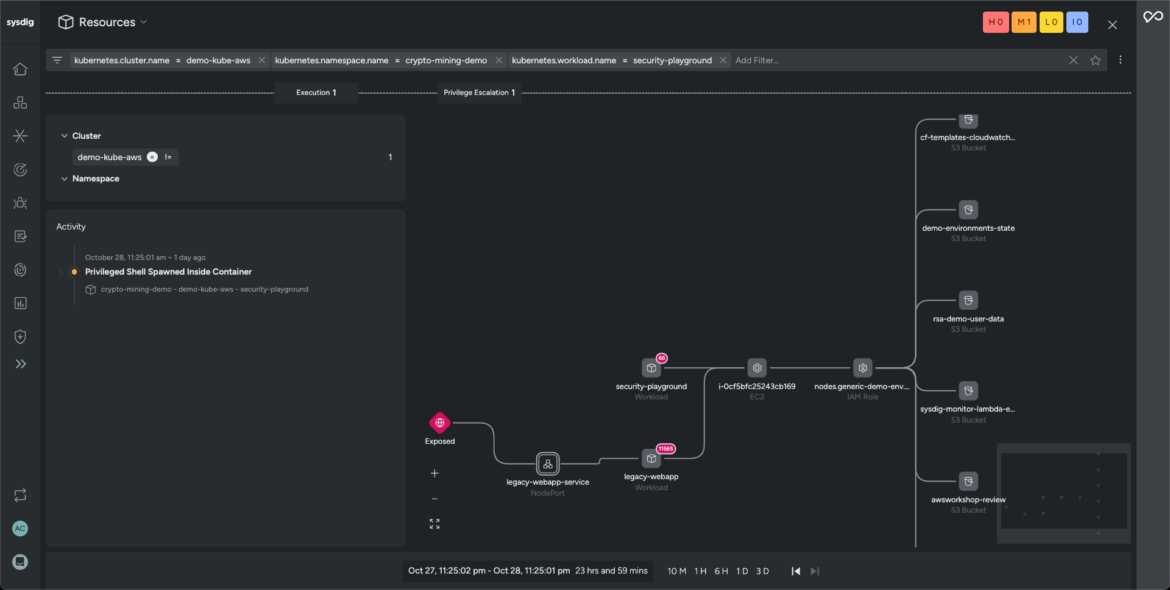
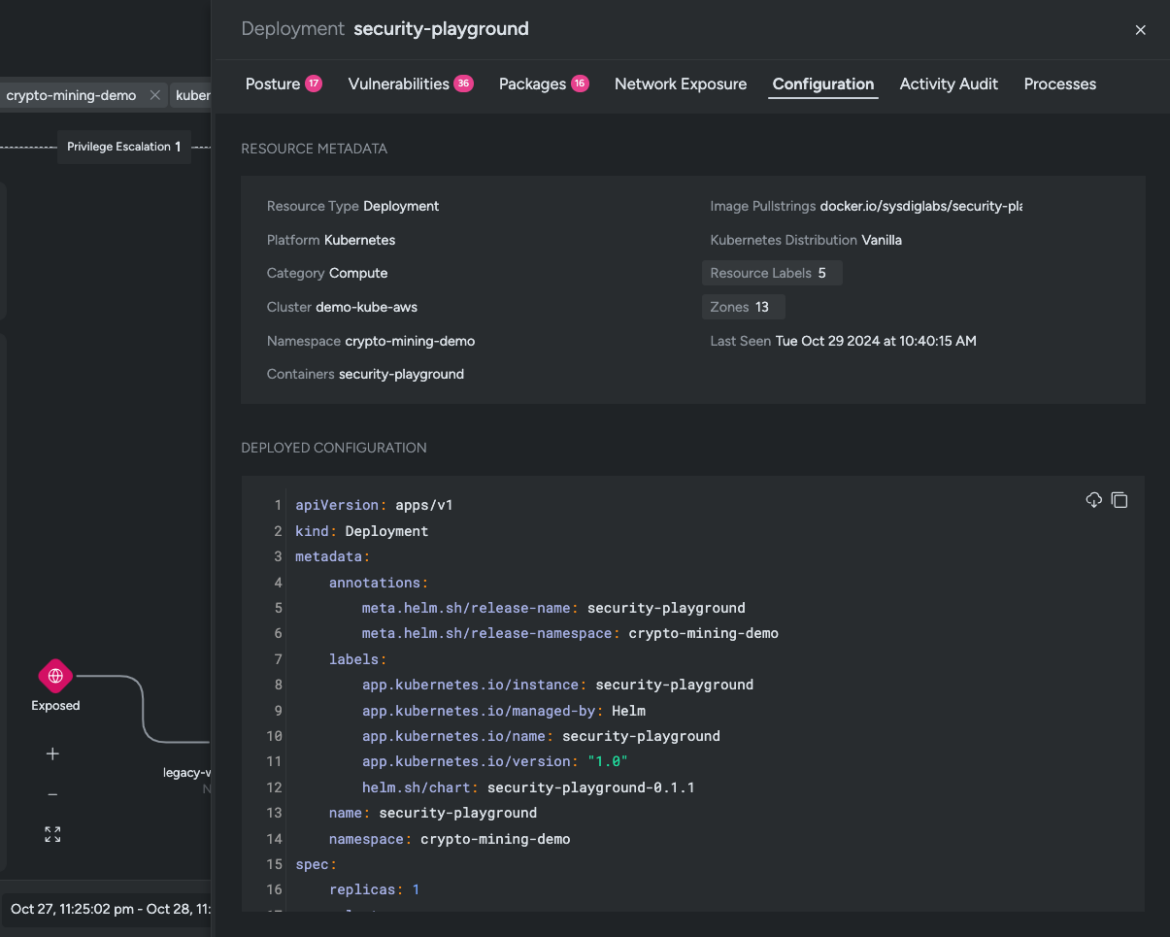
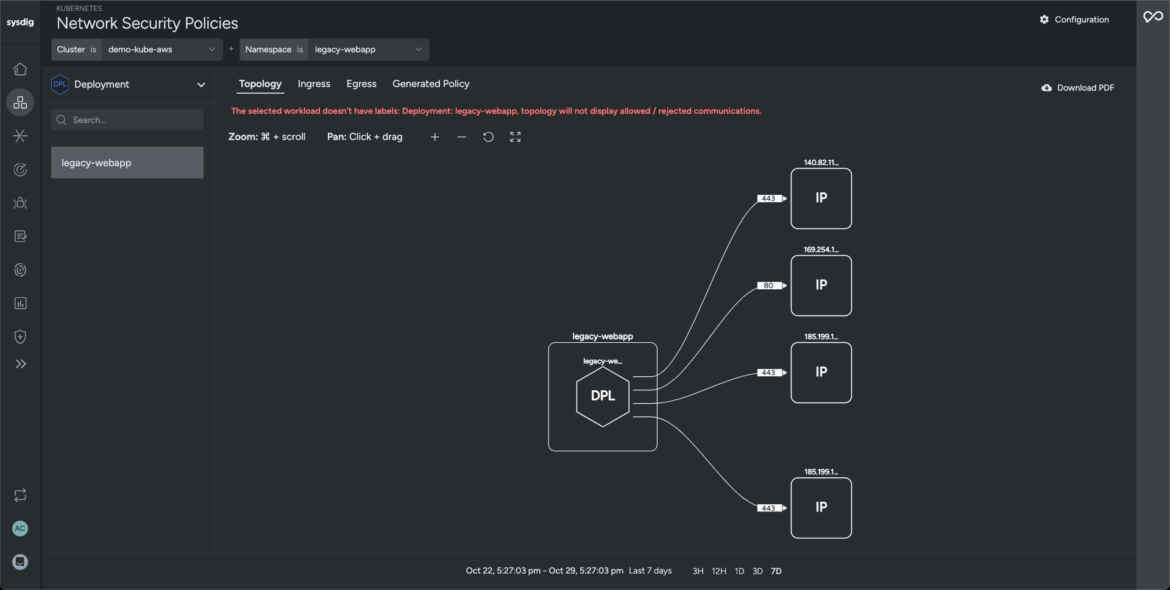
The assault chain uncovers a further workload inside our cluster uncovered to the community. The community topology reveals a number of outbound connections to unrecognized IPs (community area). Sysdig generates an optimized coverage to cease adversaries from exfiltrating delicate knowledge from our community.
apiVersion: networking.k8s.io/v1
sort: NetworkPolicy
metadata:
title: generated-network-policy
namespace: legacy-webapp
spec:
ingress: []
egress:
- to:
- namespaceSelector: {}
ports:
- port: 53
protocol: UDP
policyTypes:
- Ingress
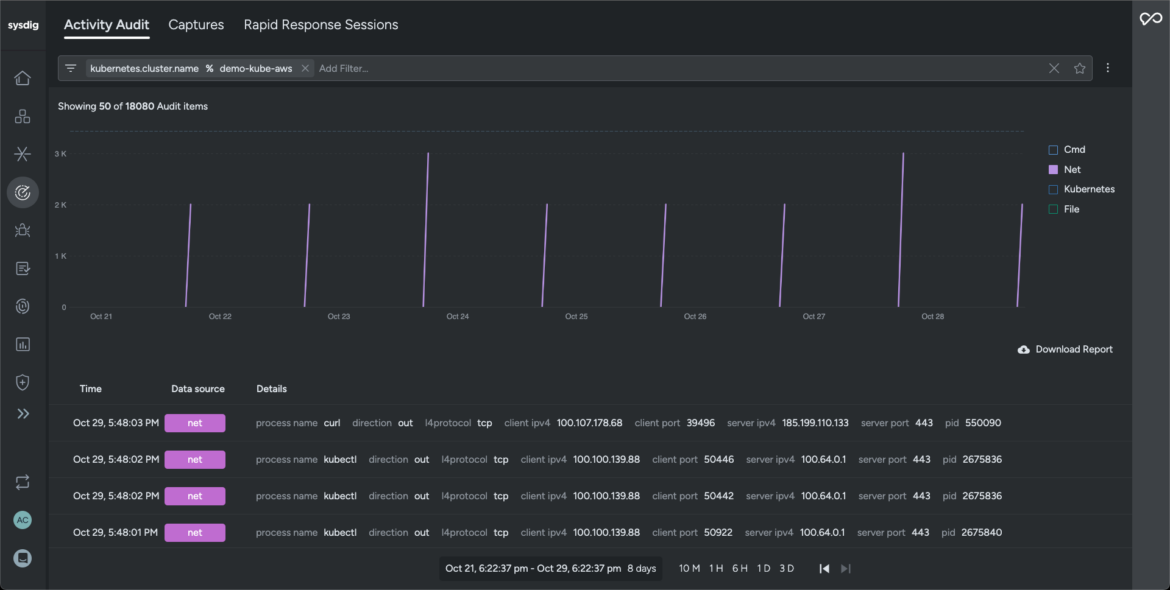
- EgressCode language: Perl (perl)Sysdig captures an audit path in our Kubernetes cluster that pinpoints the detected anomaly and isolates all instructions and community exercise generated over the chosen time interval. It helps safety groups examine logs lengthy after the impacted workload is terminated, thereby adhering to compliance requirements and governance frameworks (compliance area).
The unified platform correlates workload and community knowledge to disclose the affected IAM assets (id area) and cloud accounts. Sysdig’s Identification Insights view expands the investigation to find whether or not our adversary compromised any official consumer accounts to execute itstheir targets.
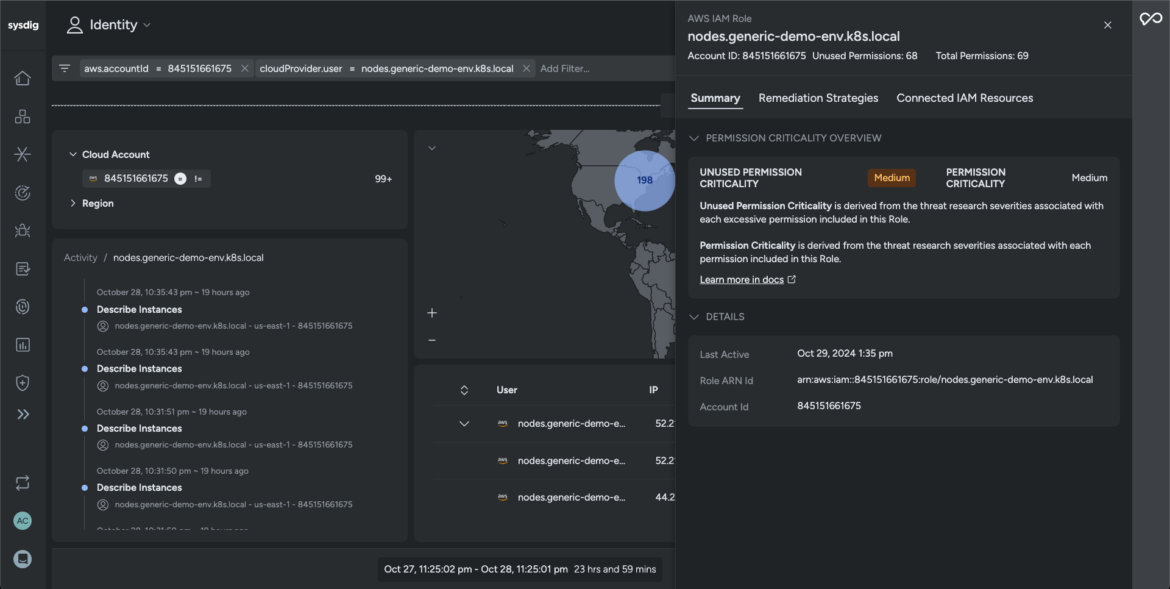
Sysdig correlates a timeline of occasions and brings forth all of the accountable elements that allowed the adversaries entry to your community. It screens lively permissions and recommends optimized configurations to cut back privileges and cease the adversary from exploiting the consumer account.
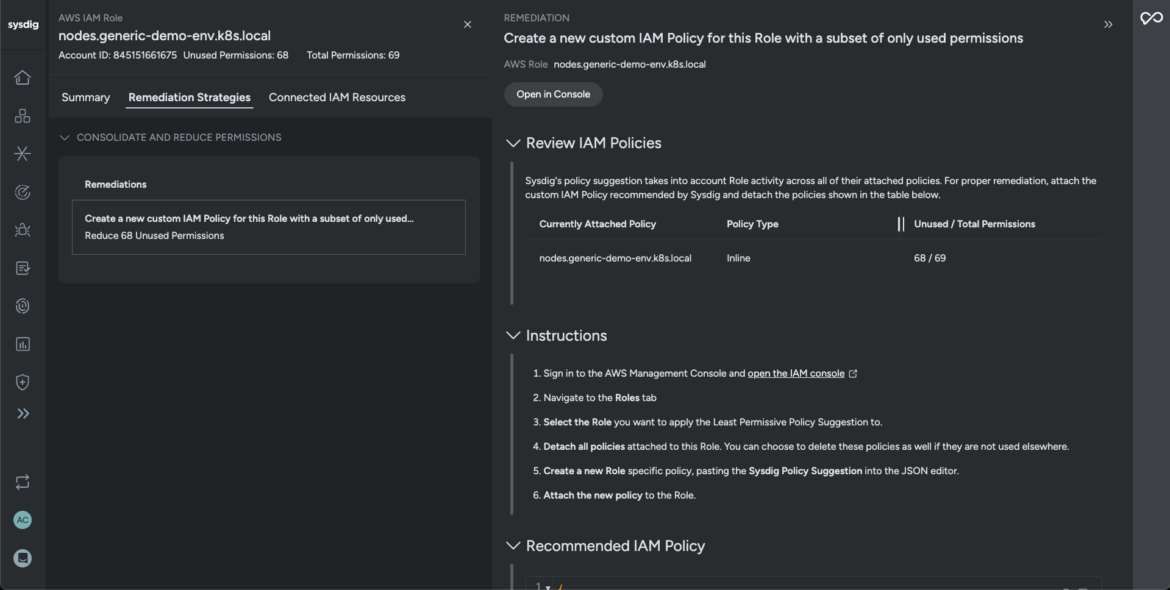
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:describeinstances"
],
"Resource": [
"*"
]
}
]
}Code language: Perl (perl)This multi-domain correlation technique, paired with actionable insights and environment friendly incident response, permits Sysdig to offer a strong protection so our clients can obtain the 555 benchmark in cloud safety.