It’s taking much less time for organisations to detect attackers of their surroundings, a report by Mandiant Consulting, part of Google Cloud, has discovered. This means that firms are strengthening their safety posture.
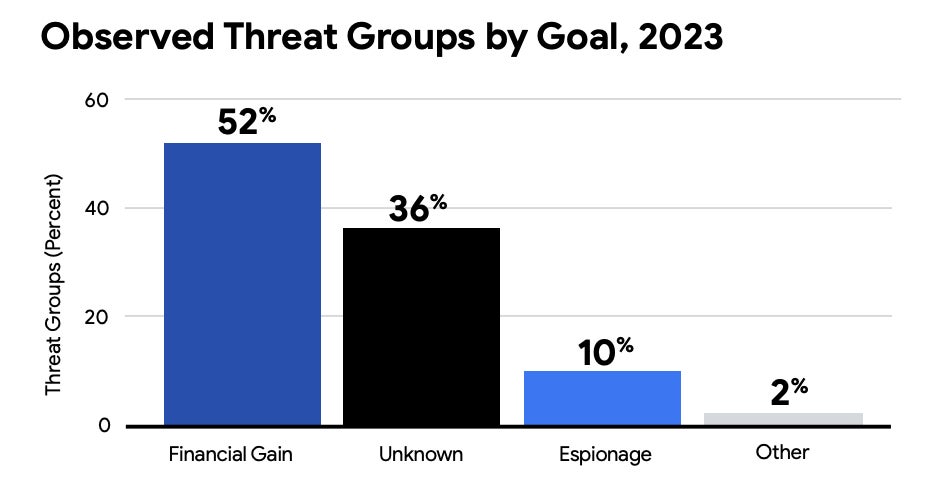
The M-Traits 2024 report additionally highlighted that the highest focused industries of 2023 have been monetary companies, enterprise {and professional} companies, tech, retail and hospitality, healthcare and authorities. This aligns with the truth that 52% of attackers have been primarily motivated by monetary achieve, as these sectors typically possess a wealth of delicate — and due to this fact priceless — data.
Financially-motivated exercise was discovered to have gone up by 8% since 2022, which is partially defined by the parallel rise in ransomware and extortion circumstances. The commonest ways in which risk actors gained entry to a goal community have been via exploits, phishing, prior compromise and stolen credentials.
Dr Jamie Collier, Mandiant Menace Intelligence Advisor Lead for Europe, instructed TechRepublic in an e mail: “Regardless of the deal with ransomware and extortion operations inside the safety neighborhood, these assaults stay efficient throughout a spread of sectors and areas. Extortion campaigns due to this fact stay extremely worthwhile for cyber criminals.
“As a result, many financially-motivated groups conducting other forms of cyber crime have transitioned to extortion operations in the last five years.”
TechRepublic takes a deeper look into the highest 5 cyber safety developments of 2023 and knowledgeable suggestions highlighted by the fifteenth annual M-Traits report:
- International organisations are enhancing their cyber defences.
- Cyber criminals have an elevated deal with evasion.
- Cloud environments are being focused extra typically.
- Cyber criminals are altering ways to bypass MFA.
- Purple groups are utilizing AI and huge language fashions.
1. International organisations are enhancing their cyber defences
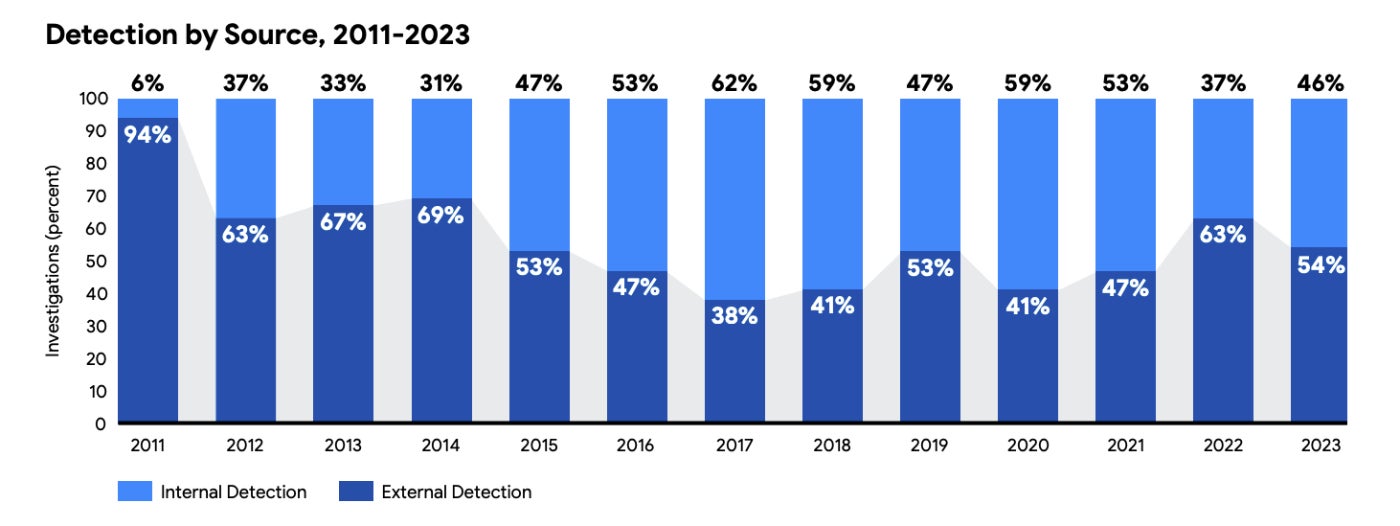
In keeping with the M-Traits report, the median dwell time of worldwide organisations decreased from 16 days in 2022 to 10 days in 2023 and is now at its lowest level in additional than a decade. The dwell time is the period of time attackers stay undetected inside a goal surroundings and signifies the power of a enterprise’s cyber posture. This determine means that firms are making significant enhancements to their cyber safety.
Nevertheless, there might be one other contributing issue; the typical proportion of assaults on account of ransomware elevated to 23% in 2023 over 18% in 2022.
Dr. Collier defined to TechRepublic: “The impact of extortion operations is immediately obvious. In the event when ransomware is deployed, a victim’s systems will be encrypted and rendered unusable. Alternatively, if data is stolen, a cyber criminal will quickly be in touch to extort a victim.”
SEE: High 7 Cybersecurity Threats for 2024
Organisations within the Asia-Pacific area noticed the largest discount in median dwell time, with it reducing by 24 days over the past 12 months. Mandiant analysts hyperlink this to the truth that the vast majority of assaults detected have been ransomware-related, and this majority was increased than every other area. In the meantime, firms in Europe, the Center East and Africa noticed the typical dwell time enhance by two days. That is regarded as because of the regional knowledge normalising following a concerted defensive effort by Mandiant in Ukraine in 2022.
One other proof that companies are getting higher at detecting cyber threats is that Mandiant discovered that 46% of compromised organisations first recognized proof of compromise internally relatively than by an outdoor entity like a legislation enforcement company or cyber safety firm, up from 37% in 2022.
2. Cyber criminals have an elevated deal with evasion
Cyber criminals are more and more focusing on edge units, utilizing “living off the land” strategies, and deploying zero-day exploits, suggesting a renewed deal with sustaining persistence on networks for so long as doable.
Dr. Collier instructed TechRepublic: “With network defenders increasingly on the lookout for extortion campaigns, evasive tactics increase the chances of a successful operation. Ransomware operations are far more effective when cyber criminals can reach the most sensitive and critical areas of a target’s network and evasive tactics help them to achieve this.”
Focusing on edge units
Edge units usually lack endpoint detection and response (EDR) capabilities, so they’re strong targets for cyber criminals seeking to go beneath the radar. In 2023, Mandiant investigators discovered that the primary and third most focused vulnerabilities have been associated to edge units. These have been:
- CVE-2023-34362: A SQL injection vulnerability within the MOVEit file switch utility.
- CVE-2023-2868: A command injection vulnerability in bodily Barracuda E mail Safety Gateway home equipment.
The report authors wrote: “Mandiant expects that we will continue to see targeting of edge devices and platforms that traditionally lack EDR and other security solutions due to the challenges associated with discovery and investigation of compromise. Exploitation of these devices will continue to be an attractive initial access vector for Chinese espionage groups to remain undetected and maintain persistence into target environments.”
SEE: Q&A on how Dell sees safety on the edge
Distant administrator instruments and “living off the land” strategies
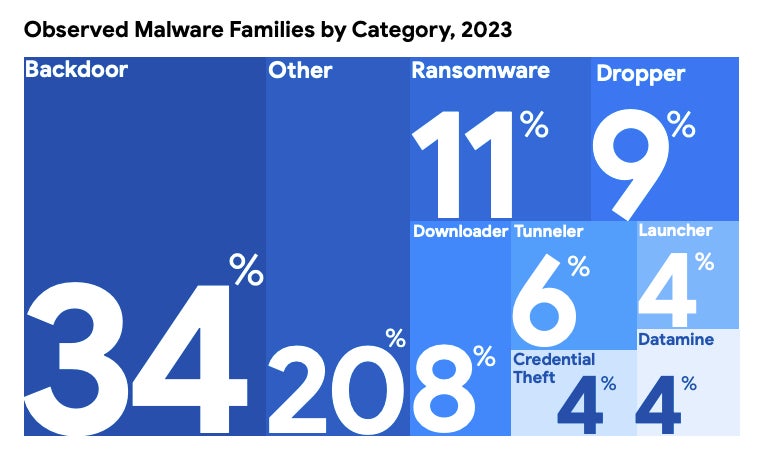
About 20% of malware households detected by Mandiant in 2023 didn’t match right into a typical class, which is a better proportion than earlier years. Moreover, 8% of assaults on this “other” class concerned the usage of distant administration instruments and different utilities. These are much less prone to be flagged by default by EDR, or different safety instruments, which may preserve the attacker undetected, and are sometimes coupled with “living off the land” strategies.
Dwelling off the land is the usage of reliable, pre-installed instruments and software program inside a goal surroundings throughout a cyber assault to assist evade detection. This will cut back the general complexity of the malware by permitting the attacker to weaponize present options which have already been safety examined by the organisation. It’s notably efficient with edge units as a result of they’re usually not monitored by community defenders, permitting them to stay on the community for longer.
A latest instance the Mandiant researchers noticed is a backdoor named THINCRUST, which was appended into the net framework recordsdata that have been liable for offering the API interface for FortiAnalyzer and FortiManager units. The risk actors have been capable of harness the native API implementation to entry and ship instructions to THINCRUST by merely interacting with a brand new endpoint URL that they had added.
Zero-day exploits
In 2023, Mandiant researchers tracked 97 distinctive zero-day vulnerabilities exploited within the wild, representing a greater than 50% progress in zero-day utilization over 2022. The zero-days have been exploited by espionage teams and financially-motivated attackers seeking to steal priceless knowledge to show a revenue.
The report’s authors anticipate the variety of recognized zero-day vulnerabilities and exploits that concentrate on them will proceed to develop within the coming years on account of plenty of components, together with:
- Rise of zero-day exploitation by ransomware and knowledge extortion teams: In 2023, zero-day exploits in MOVEit, GoAnywhere, Citrix and PaperCut have been focused considerably because of leak website posts.
- Continued state-sponsored exploitation assaults: A Microsoft report discovered cases of nation-state cyber espionage rose final 12 months.
- Development of “turnkey” exploit kits: Turnkey exploit kits are off-the-shelf instruments that may be bought from business surveillance distributors. A report by HP Wolf Safety famous a surge in Excel recordsdata with DLLs contaminated with a budget Parallax distant entry Trojan in 2023.
Suggestions from the M-Traits report
- Keep patch administration of edge units to stop exploitation of recognized vulnerabilities.
- Take a “defence-in-depth” method to assist in detecting proof of zero-day exploitation.
- Carry out investigations and community looking actions if there’s suspicion of compromise and, if there’s, goal to find how attackers entered and maintained entry.
- Comply with safety distributors’ steering for hardening structure to reinforce defences.
- Guarantee you have got an incident response plan and conduct broad environmental monitoring.
- Layer community segmentation and logging with superior EDR options.
- Consider distributors’ safety practices and community necessities earlier than deploying new {hardware} or software program to determine a baseline for regular use.
3. Cloud environments are being focused extra typically
Cloud adoption is repeatedly rising — Gartner predicts greater than 50% of enterprises will use business cloud platforms by 2028 — and, due to this fact, extra attackers are turning their consideration to those environments. In keeping with CrowdStrike, there was a 75% enhance in cloud intrusions in 2023 over 2022.
Mandiant analysts say attackers are focusing on weakly applied identification administration practices and credential storage to acquire reliable credentials and circumvent multifactor authentication (MFA).
SEE: UK’s NCSC Points Warning as SVR Hackers Goal Cloud Companies
Mandiant noticed cases the place attackers gained entry to cloud environments as a result of they occurred throughout credentials that weren’t saved securely. Credentials have been found on an internet-accessible server with default configurations or had been stolen or leaked in a earlier knowledge breach and never been modified since. In addition they gained entry utilizing totally different strategies to bypass MFA, lined in additional element within the subsequent part.
As soon as contained in the cloud surroundings, the authors noticed dangerous actors performing plenty of ways to abuse the cloud companies, together with:
- Utilizing native instruments and companies to take care of entry, transfer laterally or steal knowledge: Exploiting pre-installed instruments like Azure Knowledge Manufacturing facility and Microsoft Entra ID meant the adversaries may lower their operational profile and evade detection for longer.
- Creating digital machines (VMs) to get unmonitored entry to the organisation’s cloud: When an attacker creates a VM that runs on the organisation’s cloud infrastructure, it is not going to have their mandated safety and logging software program put in on them. It may possibly additionally enable for lateral motion to the on-premises community through VPN.
- Utilising the cloud’s processing energy for cryptomining.
- Utilizing open-source offensive safety toolsets to survey the surroundings.
Suggestions from the M-Traits report
- Replace worker authentication insurance policies.
- Use phishing-resistant MFA reminiscent of certificate-based authentication and FIDO2 safety keys through SMS as a substitute of cellphone calls and one-time passwords.
- Implement controls that prohibit entry to cloud assets to solely trusted units.
4. Cyber criminals are altering ways to bypass MFA
Now that multifactor authentication has change into a normal safety follow in lots of organisations, attackers are exploring new, artistic ways to bypass it. In keeping with Mandiant, the variety of compromises in opposition to cloud-based identities configured with MFA is growing.
In 2023, the agency noticed a rise of adversary-in-the-middle (AiTM) phishing pages that steal post-authentication session tokens and permit dangerous actors to avoid MFA. In an AiTM marketing campaign, attackers arrange a proxy server that captures a person’s credentials, MFA codes and session tokens issued by the logon portal whereas relaying the connection to the reliable server.
SEE: New phishing and enterprise e mail compromise campaigns enhance in complexity, bypass MFA
The vast majority of enterprise e mail compromise circumstances Mandiant responded to in 2023 concerned the risk actor circumventing the person’s MFA through AiTM. Previously, the relative complexity of establishing AiTM phishing infrastructure in comparison with conventional credential harvesting kinds might have stored the variety of these assaults low. Nevertheless, there at the moment are plenty of AiTM kits and phishing-as-a-service choices marketed within the cybercriminal underground, in line with Mandiant. These merchandise considerably decrease the barrier to entry for AiTM phishing, leading to an uptick.
Different strategies the Mandiant researchers noticed attackers utilizing to bypass MFA embrace:
- Social engineering assaults: For instance, spear phishing emails the place the goal is coerced into revealing their login particulars on a spoofed website. The attacker then makes use of them to sign up on the reliable website, which sends an MFA notification to the person who accepts. The organisation’s assist desk can also be focused with an instruction to reset a password or MFA machine.
- SIM-swapping: This includes transferring a goal’s cellphone quantity to a SIM card managed by an attacker, to allow them to settle for the MFA notification and take over an account. Mandiant noticed a rise in SIM-swapping assaults in 2023.
- Password-guessing: Attackers guess the passwords to dormant or service accounts that do not need MFA arrange to allow them to enrol their very own machine.
Suggestions from the M-Traits report
- Implement AiTM-resistant MFA strategies and entry insurance policies that block logons primarily based on, for instance, organisation-defined places, machine administration standing or historic logon properties.
- Monitor authentication logs for IP addresses related to phishing infrastructure, authentication with a stolen token or geographically infeasible logins.
5. Purple groups are utilizing AI and huge language fashions
Purple groups encompass cyber safety analysts who plan and execute assaults in opposition to organisations for the needs of figuring out weaknesses. In 2023, Mandiant consultants used generative AI instruments to hurry up sure actions in purple staff assessments, together with:
- The creation of preliminary drafts of malicious emails and touchdown pages for fake social engineering assaults.
- The event of customized tooling for when analysts encounter unusual or new functions and programs.
- The analysis and creation of tooling in circumstances the place environments don’t match the operational norm that can be utilized repeatedly.
Dr. Collier instructed TechRepublic: “The function of AI in purple teaming is extremely iterative with a variety of forwards and backwards between giant language fashions (LLMs) and a human knowledgeable. This highlights the distinctive contribution of each.
“AI is often well suited for repetitive tasks or fetching information. Yet, having red team consultants that understand the trade craft and possess the skills to apply context provided by LLMs in practical situations is even more important.”
AI was additionally utilized in Mandiant’s purple staff engagements, the place analysts should change into accustomed to a consumer’s surroundings from the angle of an attacker and defender to foster collaboration between purple and blue groups. Generative AI was used to assist them perceive the shopper’s platform and its safety extra rapidly.
SEE: HackerOne: How Synthetic Intelligence Is Altering Cyber Threats and Moral Hacking
Within the report, the authors speculated on how cyber safety analysts may use AI sooner or later. Purple groups generate a considerable quantity of knowledge that might be used to coach fashions tuned to assist safe buyer environments. Nevertheless, AI builders can even have to search out novel methods to make sure fashions have applicable guardrails in place whereas concurrently permitting for the reliable use of malicious exercise by purple groups.
“The combination of red team expertise and powerful AI leads could result in a future where red teams are considerably more effective, and organisations are better able to stay ahead of the risk posed by motivated attackers,” the authors wrote.
Methodology
The metrics reported in M-Traits 2024 are primarily based on Mandiant Consulting investigations of focused assault exercise performed between January 1, 2023 and December 31, 2023.