SUMMARY
- Pretend PoCs on GitHub: Cybercriminals used trojanized proof-of-concept (PoC) code on GitHub to ship malicious payloads to unsuspecting customers, together with researchers and safety professionals.
- Credential Theft: The attackers stole over 390,000 WordPress credentials, AWS entry keys, SSH non-public keys, and different delicate knowledge from compromised methods.
- Stealth Strategies: The marketing campaign employed strategies like backdoored configuration information, malicious PDFs, Python dropper scripts, and hidden npm packages to deploy the malware.
- Phishing Campaigns: The attackers additionally focused teachers by phishing emails, tricking them into putting in malware disguised as a faux kernel improve.
- Provide Chain Affect: By leveraging trusted platforms like GitHub and standard instruments, the attackers exploited the software program provide chain, posing dangers to professionals trusting these sources.
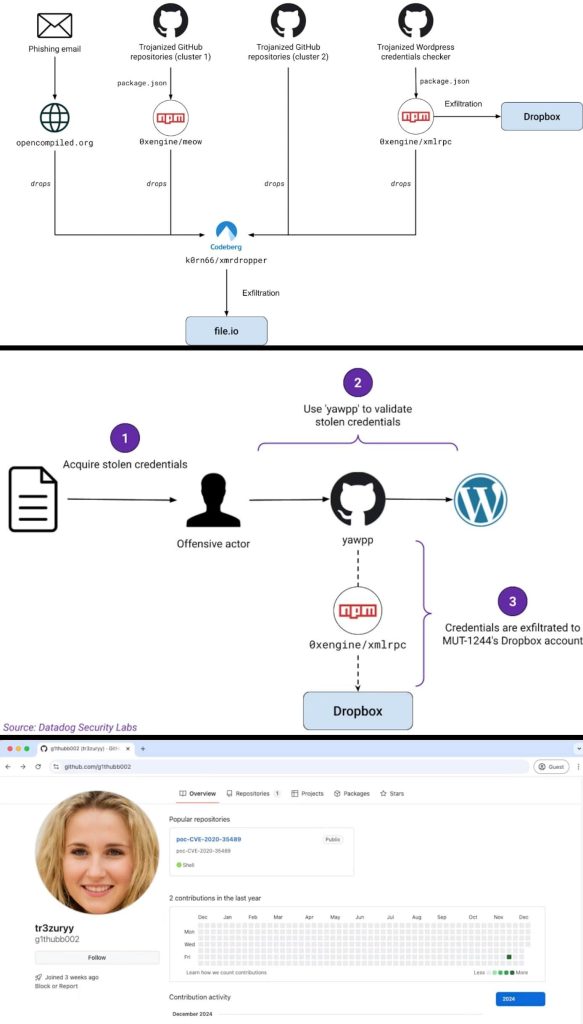
Datadog Safety Labs’ cybersecurity researchers have found a brand new, malicious year-long marketing campaign from a risk actor recognized as MUT-1244, which resulted within the theft of over 390,000 WordPress credentials.
In line with Datadog Safety Labs’ analysis, the actor used a trojanized WordPress credentials checker to steal knowledge. SSH non-public and AWS entry keys had been additionally stolen from the compromised methods of a whole lot of victims. The attackers’ key targets included pink teamers, penetration testers, safety researchers, and even different malicious actors.
Use of Phishing and Trojan
Researchers noticed that MUT-1244 has employed two principal strategies to achieve preliminary entry to sufferer methods together with phishing and trojanized GitHub repositories.
Phishing Marketing campaign: The marketing campaign focused teachers, particularly these researching high-performance computing (HPC). The e-mail urged them to put in a faux kernel improve, resulting in the obtain of malicious code.
Trojanized GitHub Repositories: MUT-1244 created quite a few faux repositories on GitHub. These repositories disguised themselves as proof-of-concept (PoC) codes for recognized vulnerabilities. Nonetheless, they contained hidden malicious code that contaminated victims who downloaded and ran them.
Pretend PoCs: A New But Acquainted Weapon
It’s value noting that the usage of faux PoCs has emerged as a brand new weapon for cybercriminals to focus on cybersecurity researchers and unsuspecting customers. In June 2023, scammers had been caught impersonating actual cybersecurity researchers to unfold malware disguised as PoCs on GitHub and X (previously Twitter).
In July 2023, the same marketing campaign was found by which faux GitHub repositories had been used to distribute malware posing as PoCs. Curiously, the stolen id utilized in that assault belonged to Shakhriyar Mamedyarov, an Azerbaijani chess grandmaster.
By September 2023, one other malicious marketing campaign surfaced, using a faux proof-of-concept script to trick researchers into downloading and executing a VenomRAT payload. This assault exploited the WinRAR vulnerability (CVE-2023-40477).
Strategies used within the trojanized repositories:
The strategies used within the trojanized repositories included a number of strategies to cover and ship malicious payloads. Some repositories contained professional exploits however hid malicious code inside prolonged, backdoored configuration information.
In different circumstances, the malicious code was embedded inside PDF information; as soon as opened, the faux exploit would extract and execute the hidden payload. A number of repositories employed Python dropper scripts to decode base64-encoded payloads, write them to disk and execute them.
Moreover, some repositories not directly contaminated victims by incorporating malicious npm packages into their code, which then downloaded and executed the attacker’s payload.
The final word aim of those assaults was to steal delicate data from victims, together with non-public SSH keys, AWS credentials, and command historical past. Furthermore, analysis revealed the malicious code contained hardcoded credentials for Dropbox and file.io companies. These credentials allowed the attacker to entry and obtain the stolen knowledge from contaminated machines.
390,000 WordPress Credentials
One other stunning disclosure was the attacker’s potential to entry over 390,000 WordPress credentials. Researchers consider these credentials had been initially obtained by different malicious actors and subsequently compromised when the attackers used a trojanized instrument referred to as “yawpp” to validate them.
“We assess with high confidence that before these credentials were exfiltrated to Dropbox, they were in the hands of offensive actors, who likely acquired them through illicit means,” Datadog’s report learn.
Yawpp was marketed as a professional WordPress credentials checker, making it an ideal lure for attackers unaware of its malicious nature. However, the MUT-1244 marketing campaign reveals that cybercriminals are discovering new methods to trick customers, making it important for people to enhance their abilities. That is very true for staff with cybersecurity coaching, as staying alert might help stop dangers to themselves and their organizations.
Specialists Feedback
Casey Ellis, Founder and Advisor at Bugcrowd, a San Francisco, Calif.-based chief in crowdsourced cybersecurity commented on the problem stating, “Concentrating on red-teamers and safety researchers by faux POCs is a troll approach as previous as safety analysis itself, nonetheless, as this assault demonstrates, it can be an efficient method to watering-hole assaults.“ Casey added, “This can be a good reminder for many who present offensive safety companies that they themselves are a part of an exploitable supply-chain, and that malicious attackers know this.“
RELATED TOPICS
- Researcher launch PoC exploit for 0-day in Chrome
- Facial DNA supplier leaks biometric knowledge by way of WordPress folder
- 1000’s of WordPress Web sites Hacked with Sign1 Malware
- Lazarus Targets Blockchain Professionals with Pretend Video Conferencing
- Hackers Publish PoC of 0-day Vulnerability in Home windows on Twitter