A North Korean risk group has been utilizing a way referred to as RID hijacking that tips Home windows into treating a low-privileged account as one with administrator permissions.
The hackers used a customized malicious file and an open supply instrument for the hijacking assault. Each utilities can carry out the assault however researchers at South Korean cybersecurity firm AhnLab say that there are variations.
How RID hijacking works
The Relative Identifier (RID) in Home windows is a part of the Safety Identifier (SID), a singular tag assigned to each person account to differentiate between them.
RID can take values that point out the account’s stage of entry, corresponding to “500” for directors, “501” for visitor accounts, “1000” for normal customers, and “512” for the area admins group.
RID hijacking happens when attackers modify the RID of a low-privilege account to match the worth of an administrator account, and Home windows will grant it elevated entry.
Nevertheless, performing the assault requires entry to the SAM registry, so the hackers have to first breach the system and acquire SYSTEM entry.
Supply: ASEC
Andariel assaults
ASEC researchers, AhnLab’s safety intelligence middle, attribute the assault to Andariel risk group, which has been linked to North Korea’s Lazarus hacker group.
The assaults start with Andariel having SYSTEM entry on the goal by way of the exploitation of a vulnerability.
The hackers obtain the preliminary escalation by utilizing instruments corresponding to PsExec and JuicyPotato to launch a SYSTEM-level command immediate.
Though SYSTEM entry is the best stage on Home windows, it doesn’t enable distant entry, can not work together with GUI apps, may be very noisy and more likely to be detected, and can’t persist between system reboots.
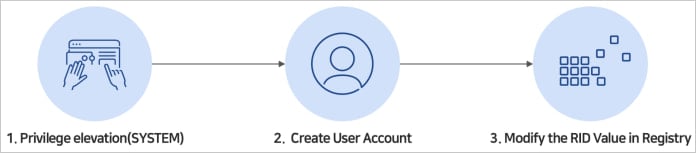
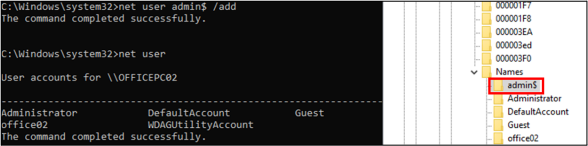
To handle these points, Andariel first created a hidden, low-privilege native person by utilizing the “net user” command and including the ‘$’ character on the finish.
In doing so, the attacker ensured that the account just isn’t seen via the “net user” command and could be recognized solely within the SAM registry. Then they carried out the RID hijacking to extend permissions to admin.
supply: AhnLab
Based on the researchers, Andariel added their account to the Distant Desktop Customers and Directors teams.
The RID hijacking required for that is potential via Safety Account Supervisor (SAM) registry modifications. The North Koreans use customized malware and an open-source instrument to carry out the modifications.
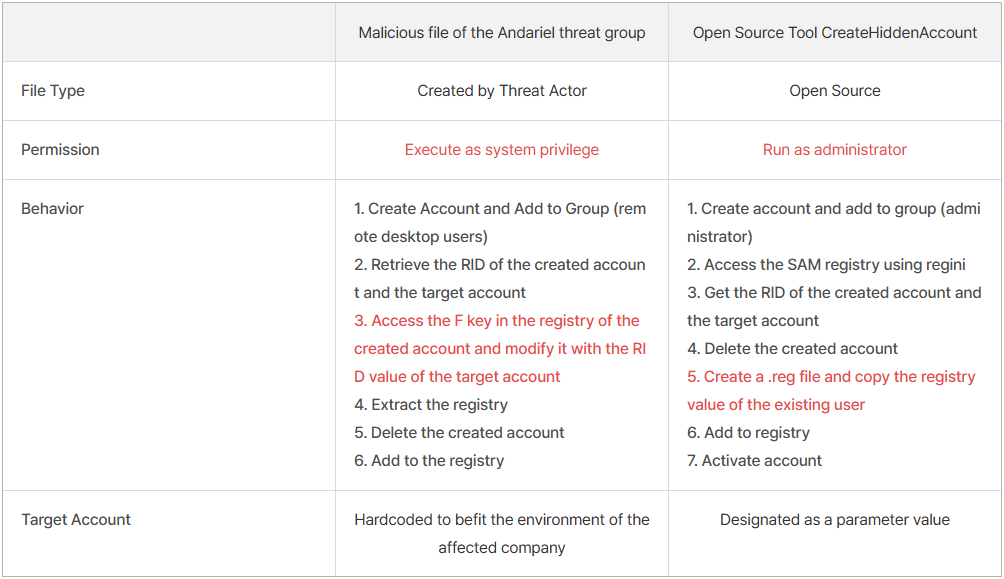
Though SYSTEM entry permits admin account creation instantly, sure restrictions might apply relying on the safety settings. Elevating the privileges of normal accounts is much stealthier and tougher to detect and cease.
Andariel additional makes an attempt to cowl its tracks by exporting the modified registry settings, deleting the important thing and the rogue account, after which re-registering it from a saved backup, permitting reactivation with out showing in system logs.
To mitigate dangers for RID hijacking assaults, system admins ought to use Native Safety Authority (LSA) Subsystem Service to verify for logon makes an attempt and password modifications, in addition to stop unauthorized entry and modifications to the SAM registry.
Additionally it is advisable to limit the execution of PsExec, JuicyPotato, and related instruments, disable the Visitor account, and shield all present accounts, even low-privileged, with multi-factor authentication.
It’s price noting that RID hijacking has been recognized since at the least 2018 when safety researcher Sebastián Castro offered the assault at DerbyCon 8 as a persistence approach on Home windows programs.
