Satirically, cybercriminals now use Google search ads to advertise phishing websites that steal advertisers’ credentials for the Google Adverts platform.
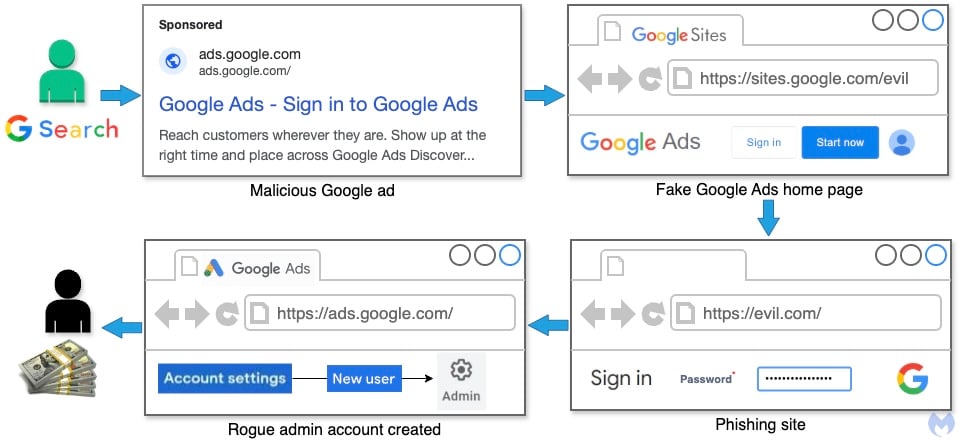
The attackers are operating adverts on Google Search impersonating Google Adverts, exhibiting as sponsored outcomes that redirect potential victims to faux login pages hosted on Google Websites however trying just like the official Google Adverts homepage, the place they’re requested to log into their accounts.
Google Websites is used to host phishing pages as a result of it permits attackers to camouflage their faux adverts, on condition that the URL (websites.google.com) matches Google Adverts’ root area for full impersonation.
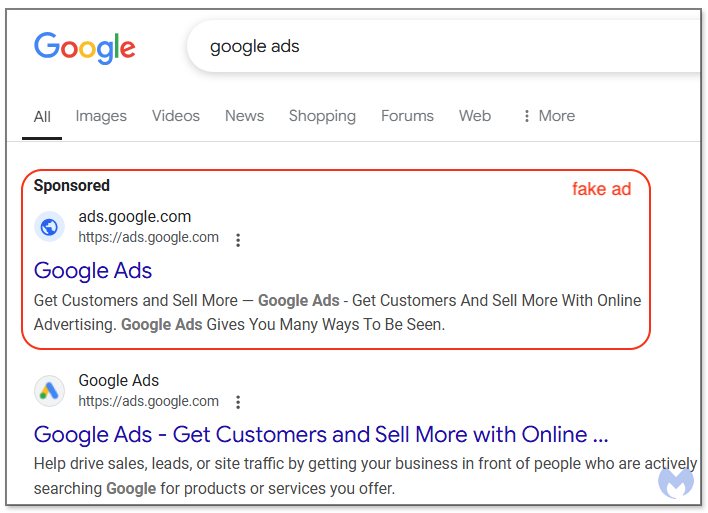
“Indeed, you cannot show a URL in an ad unless your landing page (final URL) matches the same domain name. While that is a rule meant to protect abuse and impersonation, it is one that is very easy to get around,” mentioned Jérôme Segura, Senior Director of Analysis at Malwarebytes.
“Looking back at the ad and the Google Sites page, we see that this malicious ad does not strictly violate the rule since sites.google.com uses the same root domains ads ads.google.com. In other words, it is allowed to show this URL in the ad, therefore making it indistinguishable from the same ad put out by Google LLC.”
In keeping with individuals who both fell sufferer to those assaults or noticed them in motion, the assaults embody a number of levels:
- The sufferer enters their Google account info into the phishing web page.
- The phishing equipment collects distinctive identifiers, cookies, and credentials.
- The sufferer could obtain an e-mail indicating a login from an uncommon location (Brazil)
- If the sufferer fails to cease this try, a brand new administrator is added to the Google Adverts account by way of a distinct Gmail handle.
- Menace actor goes on a spending spree and locks out the victims if they will
At the least three cybercrime teams are behind these assaults, together with Portuguese audio system almost certainly working out of Brazil, Asia-based risk actors utilizing advertiser accounts from Hong Kong (or from China), and a 3rd gang seemingly made out of Japanese Europeans.
Malwarebytes Labs, which noticed this ongoing marketing campaign, believes that the criminals’ finish purpose is to promote the stolen accounts on hacking boards and use a few of them to run future assaults utilizing the identical phishing strategies.
“This is the most egregious malvertising operation we have ever tracked, getting to the core of Google’s business and likely affecting thousands of their customers worldwide. We have been reporting new incidents around the clock and yet keep identifying new ones, even at the time of publication,” Segura added.
“Ironically, it’s quite possible that individuals and businesses that run ad campaigns are not using an ad-blocker (to see their ads and those from their competitors), making them even more susceptible to fall for these phishing schemes.”
Stolen Google Adverts accounts are extremely wanted by cybercriminals, who repeatedly use them as gasoline in different assaults that additionally abuse Google search adverts to push malware and numerous scams.
“We expressly prohibit ads that aim to deceive people in order to steal their information or scam them. Our teams are actively investigating this issue and working quickly to address it,” Google instructed BleepingComputer when requested to offer extra particulars on the assaults.
All through 2023, Google additionally blocked or eliminated 206.5 million ads for violating its Misrepresentation Coverage. It additionally eliminated over 3.4 billion adverts, restricted over 5.7 billion, and suspended over 5.6 million advertiser accounts.
