Risk actors are using the FastHTTP Go library to launch high-speed brute-force password assaults focusing on Microsoft 365 accounts globally.
The marketing campaign was lately found by incident response agency SpearTip, who mentioned the assaults started on January 6, 2024, focusing on the Azure Energetic Listing Graph API.
The researchers warn that the brute-force assaults should profitable account takeovers 10% of the time.
Abusing FastHTTP for takeovers
FastHTTP is a high-performance HTTP server and consumer library for the Go programming language, optimized for dealing with HTTP requests with improved throughput, low latency, and excessive effectivity even when used with quite a few concurrent connections.
On this marketing campaign, it’s leveraged to create HTTP requests to automate makes an attempt at unauthorized logins.
SpearTip says all requests goal the Azure Energetic Listing endpoints to both brute-force passwords or repeatedly ship multi-factor authentication (MFA) challenges to overwhelm targets in MFA Fatigue assaults.
SpearTip studies that 65% of the malicious site visitors originates from Brazil, leveraging a broad vary of ASN suppliers and IP addresses, adopted by Turkey, Argentina, Uzbekistan, Pakistan, and Iraq.
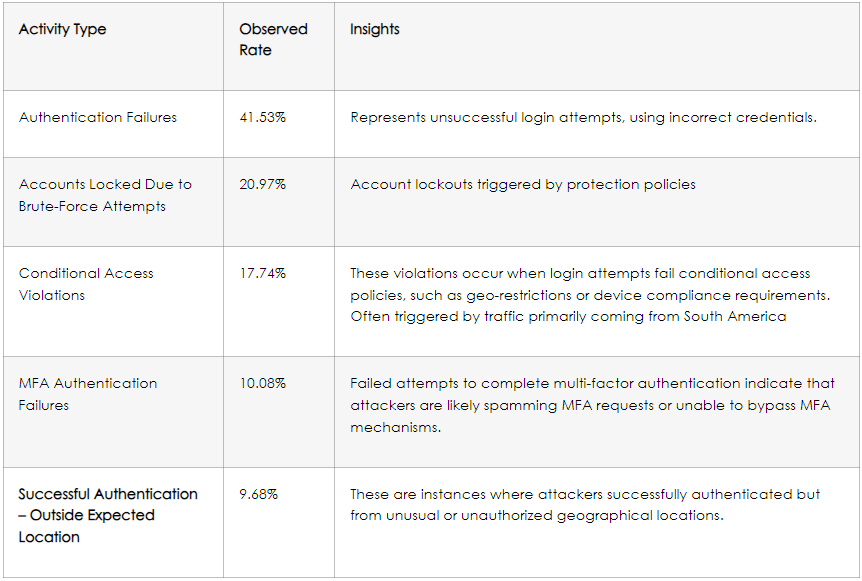
The researchers say that 41.5% of the assaults fail, 21% result in account lockouts imposed by safety mechanisms, 17.7% are rejected because of entry coverage violations (geographic or gadget compliance), and 10% had been protected by MFA.
This leaves 9.7% of instances the place the menace actors efficiently authenticate to the goal account, a notably excessive success fee.
Detect and defend
Microsoft 365 account takeovers can result in confidential knowledge publicity, mental property theft, service downtime, and different destructive outcomes.
SpearTip has shared a PowerShell script directors can use to test for the presence of the FastHTTP person agent in audit logs, indicating they had been focused by this operation.
Admins also can manually test for the person agent by logging in to the Azure portal, navigating to Microsoft Entra ID → Customers → Signal-in Logs, and making use of the filter Shopper app: “Other Clients.”
If any indicators of malicious exercise are uncovered, directors are suggested to run out person classes and reset all account credentials instantly, evaluate the enlisted MFA gadgets, and take away unauthorized additions.
A full checklist of the indications of compromise related to the marketing campaign will be discovered within the backside part of SpearTip’s report.
