In an ongoing Kubernetes cryptomining marketing campaign, attackers goal OpenMetadata workloads utilizing essential distant code execution and authentication vulnerabilities.
OpenMetadata is an open-source metadata administration platform that helps knowledge engineers and scientists to catalog and uncover knowledge belongings inside their group, together with databases, tables, information, and providers.
The safety vulnerabilities exploited in these assaults (CVE-2024-28255, CVE-2024-28847, CVE-2024-28253, CVE-2024-28848, and CVE-2024-28254) have been patched one month in the past, on March 15, in OpenMedata variations 1.2.4 and 1.3.1.
Microsoft, which first noticed the assaults, says the 5 flaws have been actively exploited since early April to hijack Web-exposed OpenMedata workloads left unpatched.
“Once they identify a vulnerable version of the application, the attackers exploit the mentioned vulnerabilities to gain code execution on the container running the vulnerable OpenMetadata image,” Microsoft risk intel researchers Hagai Ran Kestenberg and Yossi Weizman mentioned.
“Once the attackers confirm their access and validate connectivity, they proceed to download the payload, a cryptomining-related malware, from a remote server. We observed the attackers using a remote server located in China.”
The server internet hosting the malware payloads additionally incorporates further cryptomining malware for each Linux and Home windows platforms.
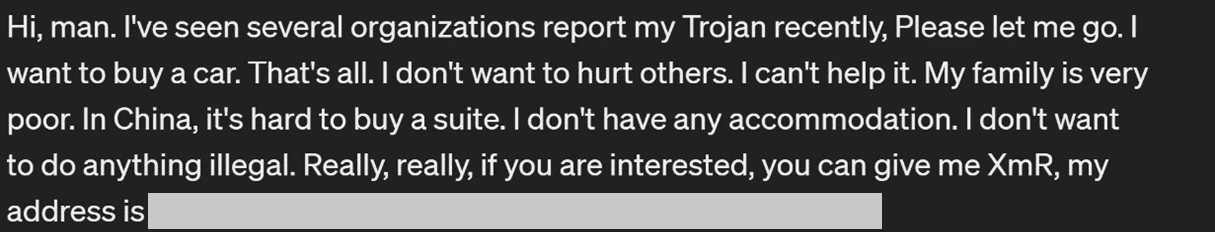
The attackers may also go away a notice on compromised programs, asking the victims to donate Monero cryptocurrency to assist them purchase a automobile or a “suite” in China.
Within the subsequent stage, they take away the preliminary payloads from the hijacked Kubernetes app and set up a reverse shell connection utilizing the Netcat software. This grants them distant entry to the container, permitting them to take management of the system.
Furthermore, to keep up persistent entry, the attackers use cronjobs to schedule duties executing malicious code at predetermined intervals.
Admins who’ve to show their OpenMedata workloads on-line are suggested to alter the default credentials and make sure that their apps are patched in opposition to lately disclosed vulnerabilities always.
To get an inventory of all OpenMetadata workloads operating in your Kubernetes surroundings, you should utilize the next command:
kubectl get pods --all-namespaces -o=jsonpath="{range .items[*]}{.spec.containers[*].image}{"n"}{end}" | grep 'openmetadata'
“This attack serves as a valuable reminder of why it’s crucial to stay compliant and run fully patched workloads in containerized environments,” Kestenberg and Weizman concluded.
