Hackers are making an attempt to take advantage of two zero-day vulnerabilities in PTZOptics pan-tilt-zoom (PTZ) reside streaming cameras utilized in industrial, healthcare, enterprise conferences, authorities, and courtroom settings.
In April 2024, GreyNoise found CVE-2024-8956 and CVE-2024-8957 after its AI-powered menace detection device, Sift, detected uncommon exercise on its honeypot community that didn’t match any recognized threats.
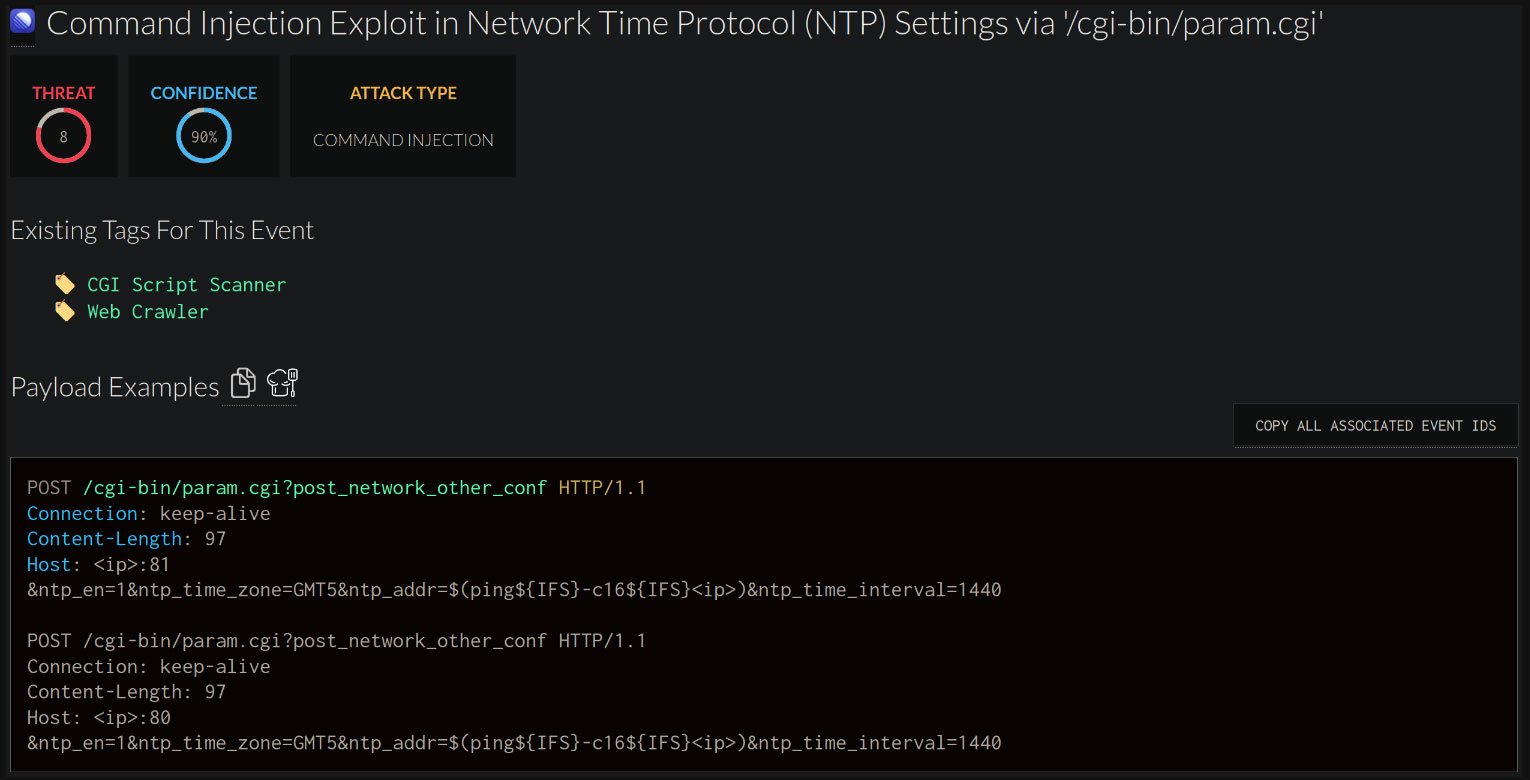
Upon examination of the alert, GreyNoise researchers uncovered an exploit try that focused the digicam’s CGI-based API and embedded ‘ntp_client’ aiming to attain command injection.
A technical deep-dive by GreyNoise researcher Konstantin Lazarev gives extra information on the 2 flaws.
CVE-2024-8956 is a weak authentication downside within the digicam’s ‘lighthttpd’ net server, permitting unauthorized customers to entry the CGI API with out an authorization header, which exposes usernames, MD5 password hashes, and community configurations.
CVE-2024-8957 is attributable to inadequate enter sanitization within the ‘ntp. addr’ discipline processed by the ‘ntp_client’ binary, permitting attackers to make use of a specifically crafted payload to insert instructions for distant code execution.
Greynoise notes that exploitation of those two flaws can result in full digicam takeover, an infection with bots, pivoting to different gadgets linked on the identical community, or disruption of video feeds.
The cybersecurity agency reviews that whereas the supply of the preliminary exercise went silent shortly after the honeypot assaults, a separate try utilizing wget to obtain a shell script for reverse shell entry was noticed in June.
Disclosure and fixing standing
Upon discovering CVE-2024-8956 and CVE-2024-8957, GreyNoise labored with VulnCheck for accountable disclosure to impacted distributors.
Supply: GreyNoise
Gadgets impacted by the 2 flaws are NDI-enabled cameras based mostly on Hisilicon Hi3516A V600 SoC V60, V61, and V63, which run VHD PTZ digicam firmware variations older than 6.3.40.
This consists of a number of fashions from PTZOptics, Multicam Programs SAS cameras, and SMTAV Company gadgets.
PTZOptics launched a safety replace on September 17, however fashions just like the PT20X-NDI-G2 and PT12X-NDI-G2 didn’t get a firmware replace as a consequence of having reached end-of-life.
Later, GreyNoise found that at the least two newer fashions, PT20X-SE-NDI-G3, and PT30X-SE-NDI-G3, which additionally did not obtain a patch, have been impacted too.
PTZOptics was notified in regards to the expanded scope via VulnCheck on October 25, however no fixes for these fashions have been launched as of writing.
GreyNoise informed BleepingComputer that the issues seemingly have an effect on a broad vary of digicam fashions.
“We (strongly) believe that a wider range of devices is affected, potentially indicating that the actual culprit lies within the SDK the manufacturer (ValueHD / VHD Corporation) uses,” GreyNoise informed BleepingComputer.
That being stated, customers ought to test with their machine vendor to see if fixes for CVE-2024-8956 and CVE-2024-8957 have been included within the newest obtainable firmware replace for his or her gadgets.
