Hackers are exploiting a crucial command injection vulnerability in Zyxel CPE Sequence gadgets that’s at present tracked as CVE-2024-40891 and stays unpatched since final July.
The vulnerability permits unauthenticated attackers to execute arbitrary instructions utilizing the ‘supervisor’ or ‘zyuser’ service accounts.
Vulnerability intelligence firm VulnCheck added the safety problem to its database final yr on July 12 and listed it amongst different points exploited within the wild for preliminary entry.
Technical particulars on the vulnerability haven’t been publicly disclosed and Zyxel didn’t launch a safety advisory or a patch for CVE-2024-40891, and the difficulty stays exploitable within the newest firmware.
It seems that hackers found tips on how to leverage the vulnerability and are utilizing it in assaults as risk monitoring platform GreyNoise has noticed just lately exploitation exercise originating from a number of distinctive IP addresses.
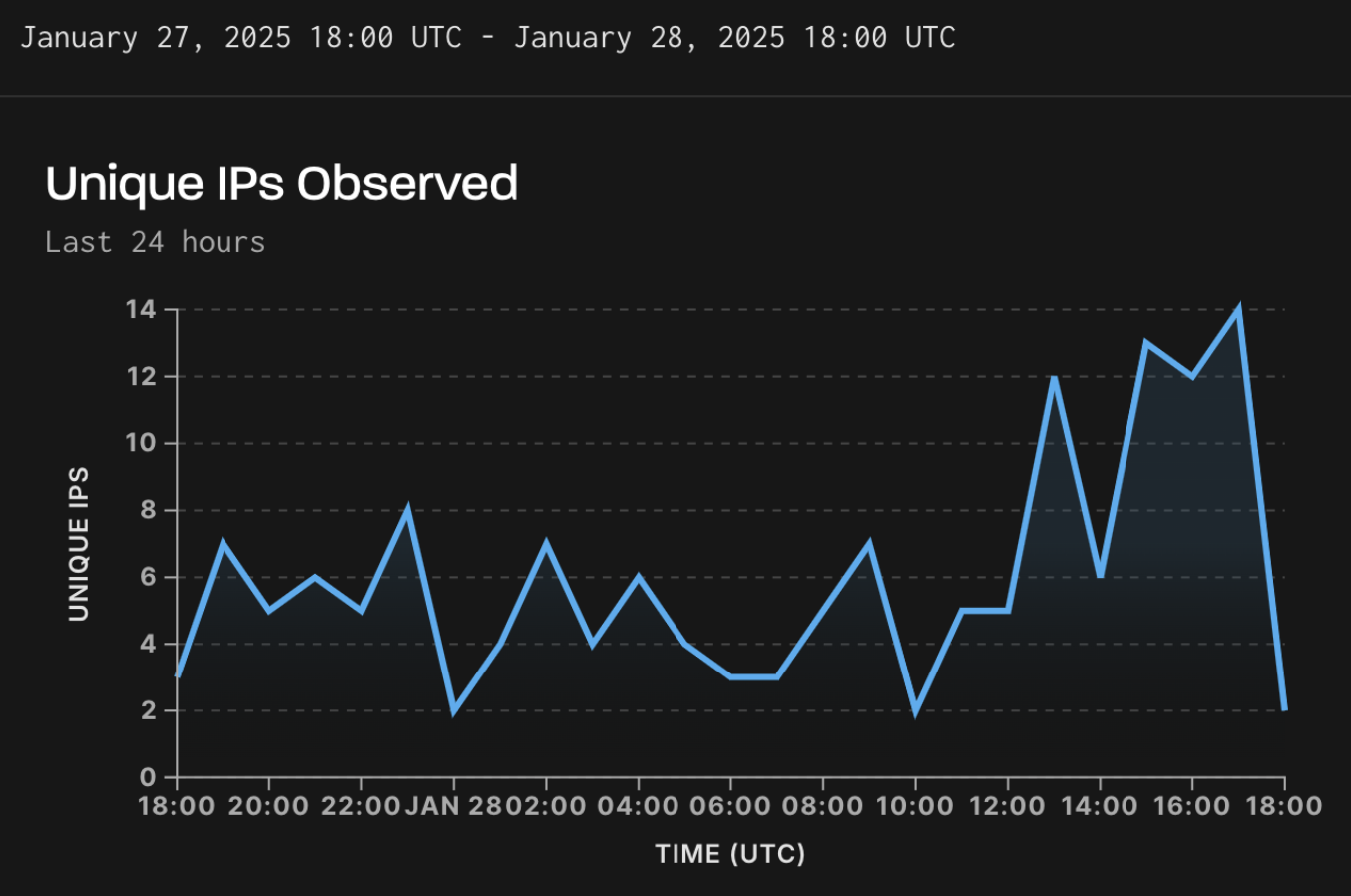
Supply: GreyNoise
GreyNoise notes that the flaw is just like CVE-2024-40890, which is HTTP-based. Nevertheless, VulnCheck confirmed that the present exploitation detection is for the unpatched CVE-2024-40891, which is predicated on the telnet protocol.
“GreyNoise is observing active exploitation attempts targeting a zero-day critical command injection vulnerability in Zyxel CPE Series devices tracked as CVE-2024-40891,” reads the bulletin.
“At this time, the vulnerability is not patched, nor has it been publicly disclosed. Attackers can leverage this vulnerability to execute arbitrary commands on affected devices, leading to complete system compromise, data exfiltration, or network infiltration” – GreyNoise
Web scanning service Censys studies that there are greater than 1,500 Zyxel CPE Sequence gadgets at present uncovered on-line, largely within the Philippines, Turkey, the UK, France, and Italy.
Contemplating that no safety replace is accessible to deal with the issue, system directors ought to no less than attempt to block the IP addresses launching the exploitation makes an attempt. Nevertheless, this assaults from different IP addresses are nonetheless potential.
For additional mitigation, it is strongly recommended to observe site visitors for atypical telnet requests to Zyxel CPE administration interfaces, and prohibit entry to the executive interface solely to a specified IP allowlist.
If distant administration options usually are not used/wanted, it’s higher to disable them fully to scale back the assault floor.
BleepingComputer has contacted Zyxel with a request for a remark, however we’re nonetheless ready for the seller’s response.
