Cybersecurity researchers on the Optimistic Applied sciences Knowledgeable Safety Middle (PT ESC) have discovered a sneaky malware marketing campaign concentrating on the Python Bundle Index (PyPI), a preferred on-line repository for Python software program. The assault targeted on builders, machine studying engineers, and AI fans who would possibly combine DeepSeek AI into their initiatives.
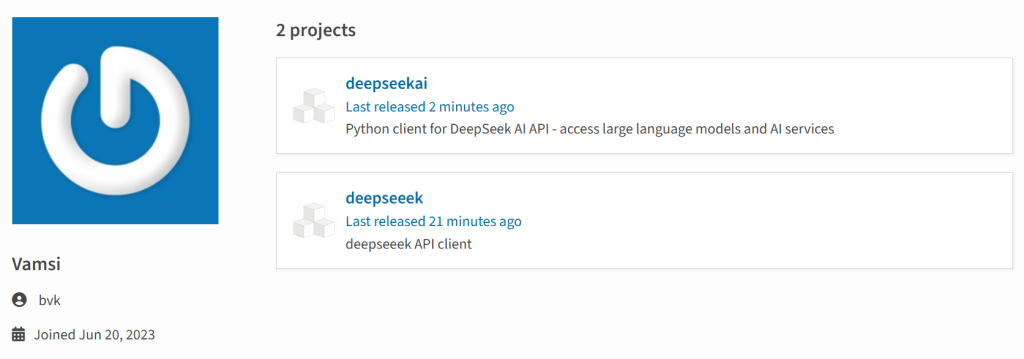
All of it started on January 29, 2025, when a suspicious person named “bvk,” whose account had been inactive since its creation in June 2023, uploaded two malicious packages: deepseeek or deepseekai. These packages have been designed to imitate respectable integrations with DeepSeek however contained malicious code aimed toward stealing delicate data from customers’ programs.
As soon as put in, the dangerous packages executed instructions that collected system data and stole atmosphere variables. These variables usually include important information, akin to credentials for cloud storage, database entry, or different infrastructure sources. The stolen data was then despatched to a command-and-control (C2) server hosted on Pipedream, a developer integration platform.
Curiously, in accordance with PT ESC’s weblog submit shared with Hackread.com, the attackers appeared to make use of an AI-powered assistant to write down their malicious script, as evidenced by the code’s feedback explaining its performance. AI-generated content material and codes have grow to be a major cybersecurity menace, with consultants warning that the danger is just rising.
Fast Motion
After discovering the malicious packages, Optimistic Applied sciences instantly alerted PyPI directors, who quarantined and deleted the packages inside an hour. Nonetheless, throughout that brief window, the packages had already been downloaded 222 instances throughout numerous instruments and strategies within the following international locations:
- Different international locations, together with Germany, Canada, and Hong Kong, additionally reported downloads.
Exploiting DeepSeek’s Recognition
Though the assault was contained earlier than inflicting large-scale hurt, it presents essential questions concerning the safety of open-source repositories. Cybercriminals regularly monitor rising traits and exploit them to trick unsuspecting customers. On this instance, the recognition of DeepSeek doubtless attracted malicious actors searching for to use its rising person base.
In a remark to Hackread.com, Jason Soroko, Senior Fellow at Sectigo, emphasised the impression of this incident stating, “This report underscores how attackers exploit trusted naming conventions and the reliance on authentic package sources within the open-source ecosystem. While the threat was neutralized quickly, it serves as a reminder of the growing risks associated with software supply chains.”
Defending Your self from Related Threats
This incident is an efficient signal to watch out when downloading and putting in software program, particularly from public repositories like PyPI. Listed here are a couple of fast ideas that will help you keep protected:
- Safety Instruments: Use providers like Optimistic Applied sciences’ PyAnalysis, which screens PyPI for malicious exercise in real-time.
- Confirm Bundle Sources: Solely obtain well-established packages with a robust fame. Be cautious of newly uploaded instruments, particularly these with names much like well-liked initiatives.
- Scan Dependencies: Use instruments to investigate the code of packages earlier than putting in them.
- Monitor Setting Variables: Regulate delicate information saved in your system and restrict its publicity the place potential.