Hackers are focusing on different hackers with a faux OnlyFans instrument that claims to assist steal accounts however as an alternative infects risk actors with the Lumma stealer information-stealing malware.
The operation, found by Veriti Analysis, constitutes a attribute instance of the blurred strains between being a predator or prey on the planet of cybercrime, the place ironic twists and backstabs are ample.
“Checking” right into a Lumma an infection
OnlyFans is a particularly standard subscription-based grownup content material platform the place creators can earn cash from customers (known as “fans”) who pay for entry to their content material.
Creators can share movies, pictures, messages, and stay streams with their subscribers, whereas subscribers pay a recurring price or one-time funds for unique content material.
Given its recognition, OnlyFans accounts typically turn into targets of risk actors who try and hijack them to steal fan funds, extort the account proprietor to pay a ransom, or just leak personal pictures.
Checker instruments are designed to assist validate massive units of stolen login credentials (usernames and passwords), checking if the login particulars match any OnlyFans accounts and whether or not they’re nonetheless legitimate.
With out these instruments, cybercriminals must manually take a look at out 1000’s of credential pairs, an impractical and tedious course of that might render the scheme nonviable.
Nevertheless, these instruments are generally created by different cybercriminals, inflicting hackers to belief that they’re secure to make use of, and in some instances, this backfires.
Veriti found a case of an OnlyFans checker promising to confirm credentials, examine account balances, confirm cost strategies, and decide creator privileges however as an alternative put in the Lumma information-stealing malware.
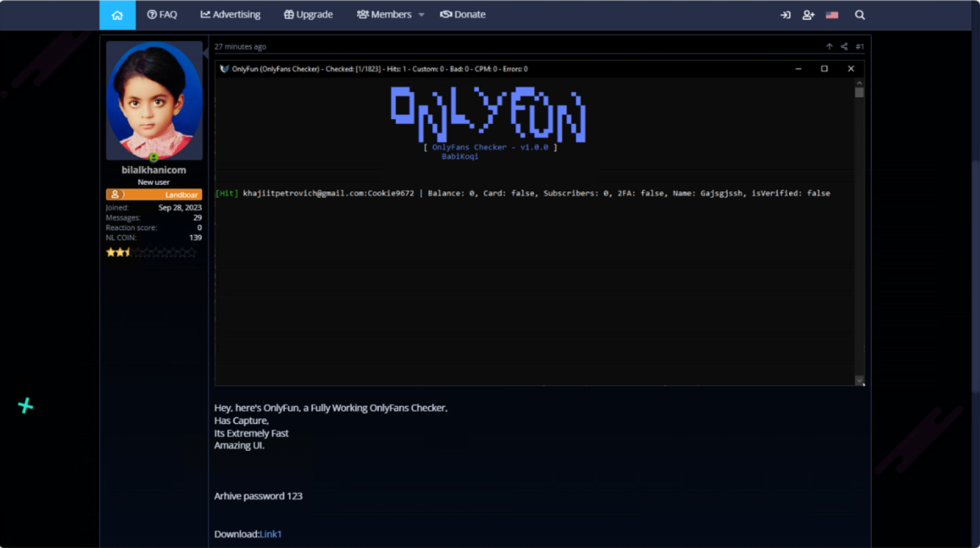
Supply: Veriti
The payload, named “brtjgjsefd.exe,” is fetched from a GitHub repository and loaded into the sufferer’s laptop.
Lumma is an information-stealing malware-as-a-service (MaaS) that has been rented to cybercriminals since 2022 for $250-$1000/month and distributed by way of varied means, together with malvertising, YouTube feedback, torrents, and, extra lately, GitHub feedback.
It’s a sophisticated data stealer with revolutionary evasion mechanisms and the flexibility to restore expired Google session tokens. It’s largely identified for stealing two-factor authentication codes, cryptocurrency wallets, and passwords, cookies, and bank cards saved on a sufferer’s browser and file system.
Lumma additionally doubles as a loader itself, able to introducing extra payloads onto the compromised system and executing PowerShell scripts.
A broader deception operation
Veriti discovered that when the Lumma Stealer payload is launched, it’ll connect with a GitHub account beneath the identify “UserBesty,” which the cybercriminal behind this marketing campaign makes use of to host different malicious payloads.
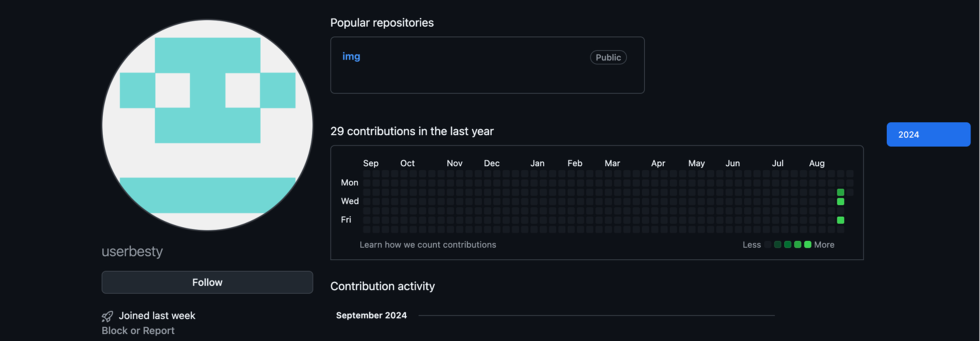
Supply: Veriti
Particularly, the GitHub repository incorporates executables that resemble checkers for Disney+ accounts, Instagram, and a supposed Mirai botnet builder:
- Disney+ account thieves are focused with “DisneyChecker.exe”
- Instagram hackers are lured by “InstaCheck.exe”
- Wannabe botnet creators are lured with “ccMirai.exe”
Digging deeper into the malware’s communications, Veriti’s researchers discovered a set of “.shop” domains that acted as command and management (C2) servers, sending instructions to Lumma and receiving the exfiltrated knowledge.
This marketing campaign isn’t the primary time risk actors have focused different cybercriminals in malicious assaults.
In March 2022, hackers focused hackers with clipboard stealers disguised as cracked RATs and malware-building instruments to steal cryptocurrency.
Later that 12 months, a malware developer backdoored their very own malware to steal credentials, cryptocurrency wallets, and VPN account knowledge from different hackers.
