A risk actor focused low-skilled hackers, referred to as “script kiddies,” with a faux malware builder that secretly contaminated them with a backdoor to steal knowledge and take over computer systems.
Safety researchers at CloudSEK report that the malware contaminated 18,459 units globally, most positioned in Russia, the US, India, Ukraine, and Turkey.
“A trojanized version of the XWorm RAT builder has been weaponized and propagated,” reads the CloudSEK report.
“It is targeted specially towards script kiddies who are new to cybersecurity and directly download and use tools mentioned in various tutorials thus showing that there is no honour among thieves.”
CloudSEK has discovered the malware included a kill change that was activated to uninstall the malware from most of the contaminated machines, however on account of sensible limitations, some stay compromised.
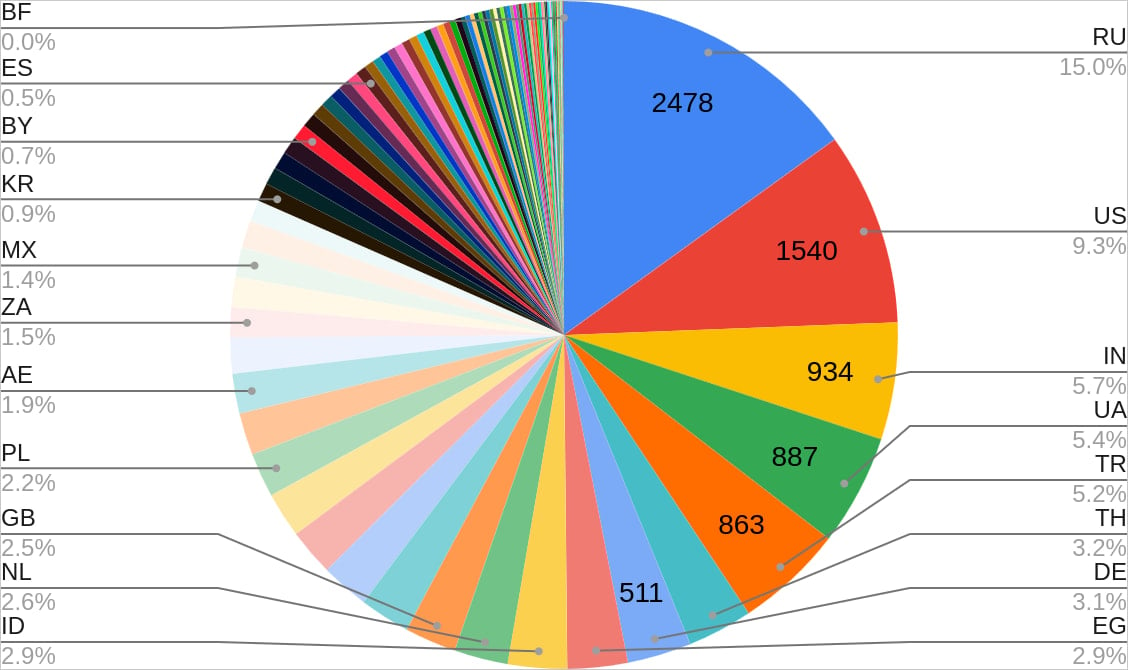
Supply: CloudSEK
Faux RAT builder installs malware
The researchers say they just lately found a Trojanized XWorm RAT builder being distributed by way of varied channels, together with GitHub repositories, file internet hosting platforms, Telegram channels, YouTube movies, and web sites.
These sources promoted the RAT builder, stating it could enable different risk actors to make the most of the malware with out having to pay for it.
Nonetheless, as a substitute of being an precise builder for the XWorm RAT, it contaminated the risk actor’s units with the malware.
As soon as a machine is contaminated, the XWorm malware checks the Home windows Registry for indicators it’s operating on a virtualized surroundings and stops if the outcomes are optimistic.
If the host qualifies for an infection, the malware performs the required Registry modifications to make sure persistence between system boots.
Each contaminated system is registered to a Telegram-based command and management (C2) server utilizing a hardcoded Telegram bot ID and token.
The malware additionally routinely steals Discord tokens, system data, and site knowledge (from IP tackle), and exfiltrates it to the C2 server. Then, it waits for instructions from the operators.
Out of the 56 instructions supported in complete, the next are significantly harmful:
- /machine_id*browsers – Steal saved passwords, cookies, and autofill knowledge from net browsers
- /machine_id*keylogger – Report every thing the sufferer sorts on their pc
- /machine_id*desktop – Seize the sufferer’s lively display screen
- /machine_id*encrypt*<password> – Encrypt all recordsdata on the system utilizing a offered password
- /machine_id*processkill*<course of> – Terminate particular operating processes, together with safety software program
- /machine_id*add*<file> – Exfiltrate particular recordsdata from the contaminated system
- /machine_id*uninstall – Distant the malware from the system
CloudSEK discovered that the malware operators had exfiltrated knowledge from roughly 11% of the contaminated units, principally taking screenshots of contaminated units, as proven under, and stealing browser knowledge.
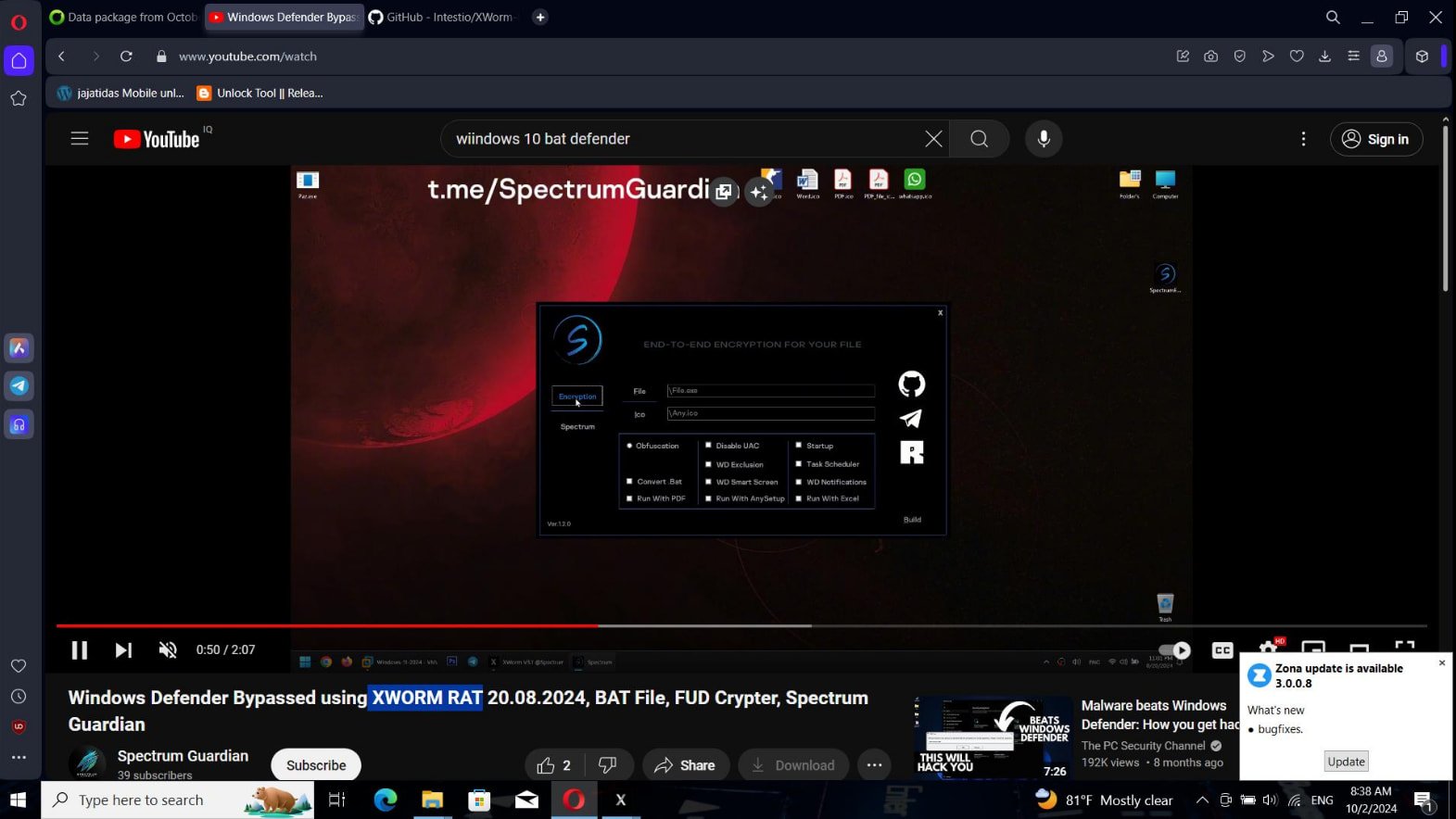
Supply: CloudSEK
Disrupting with the kill change
The CloudSEK researchers disrupted the botnet by using hard-coded API tokens and a built-in kill change to uninstall the malware from contaminated units.
To do that, they despatched a mass uninstall command to all listening shoppers, looping by way of all recognized machine IDs that they had beforehand extracted from Telegram logs. In addition they brute-forced machine IDs from 1 to 9999, assuming a easy numeric sample.
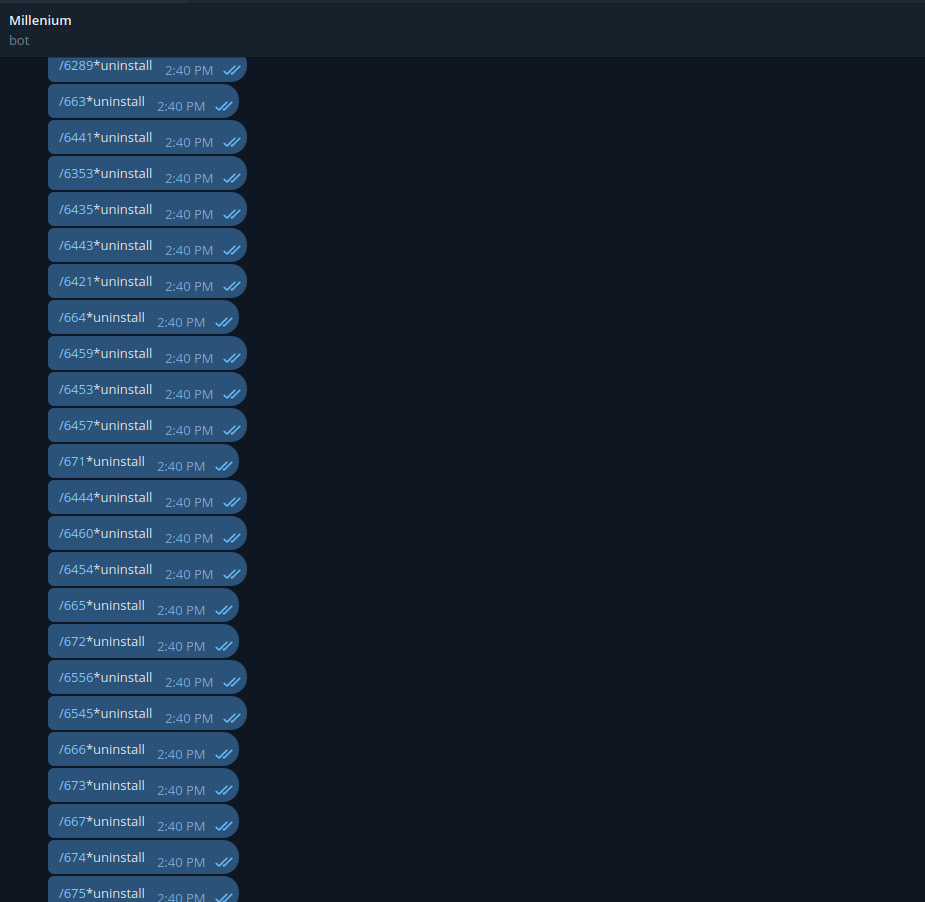
Supply: CloudSEK
Though this induced the malware to be faraway from most of the contaminated machines, these not on-line when the command was issued stay compromised.
Additionally, Telegram topics messages to price limiting, so among the uninstall instructions might have been misplaced in transit.
Hackers hacking hackers is a typical state of affairs we regularly see manifesting within the wild.
The takeaway from CloudSEK’s findings is rarely to belief unsigned software program, particularly these distributed by different cybercriminals, and solely set up malware builders on testing/evaluation environments.
