Canadian retail chain Large Tiger disclosed an information breach in March 2024.
A risk actor has now publicly claimed accountability for the info breach and leaked 2.8 million data on a hacker discussion board that they declare are of Large Tiger prospects.
Knowledge breach monitoring service HaveIBeenPwned has added the leaked database to its web site to make it straightforward for customers to verify if their data was compromised.
The low cost retailer chain operates over 260 shops and employs 8,000 individuals throughout Canada
2.8 million buyer data leaked on-line
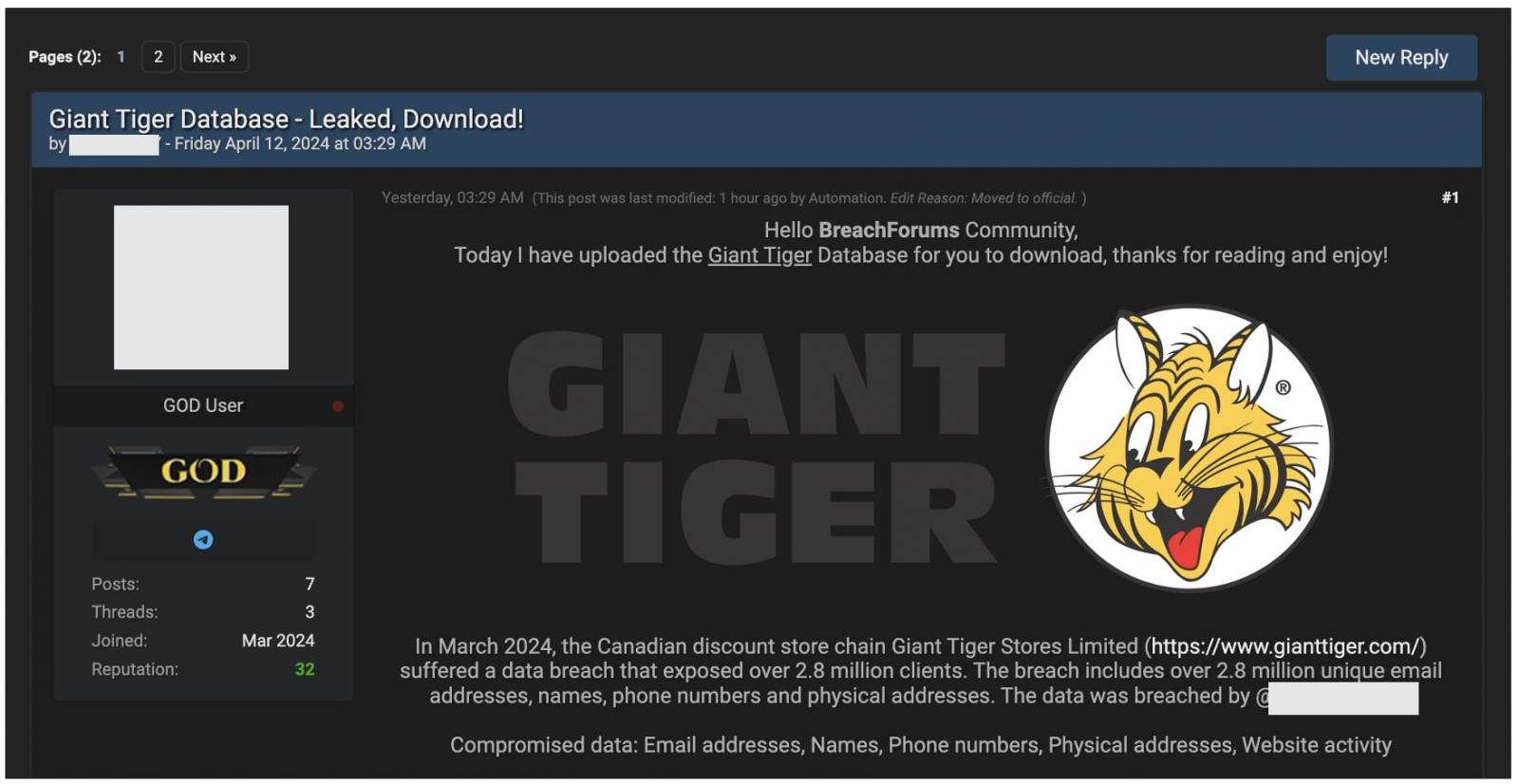
On Friday, BleepingComputer seen a publish titled “Giant Tiger Database – Leaked, Download!” surfacing on a hacker discussion board.
The risk actor behind the publish claims to have uploaded the “full” database of Large Tiger buyer data stolen in March 2024.
“In March 2024, the Canadian discount store chain Giant Tiger Stores Limited… suffered a data breach that exposed over 2.8 million clients,” states the risk actor.
“The breach includes over 2.8 million unique email addresses, names, phone numbers and physical addresses.”
(BleepingComputer)
The stolen information within the dump, claims the risk actor, moreover consists of the “website activity” of Large Tiger prospects.
“I finally opened 60 of the 60 pages of the database section!” replied one discussion board member to the publish, with others requesting to preview a pattern of the info set. The risk actor obliged and posted a small snippet.
The information set has been leaked primarily without cost. Though the obtain hyperlink to the set needs to be unlocked by spending “8 credits,” such credit are sometimes trivially generated by discussion board members by, for instance, commenting on current posts or contributing new posts.
Risk actors typically breach corporations and steal delicate information to blackmail them and extort cash. Failing profitable extortion, a risk actor might intentionally leak the stolen information on-line or promote it off on darkish internet marketplaces to patrons eager about conducting id theft and phishing assaults.
Breach attributable to a third-party vendor
BleepingComputer has not verified the authenticity of the info set, nonetheless, we did attain out to Large Tiger with questions concerning the leak.
With out commenting on the authenticity of the leaked information, a spokesperson responded:
“On March 4, 2024, Giant Tiger became aware of security concern related to a third-party vendor we use to manage customer communications and engagement,” a Large Tiger spokesperson advised BleepingComputer.
“We determined that contact information belonging to certain Giant Tiger customers was obtained without authorization. We sent notices to all relevant customers informing them of the situation.”
“No payment information or passwords were involved.”
Large Tiger declined to share the identify of the third-party vendor in query.
Information added to HaveIBeenPwned
As of April twelfth, the leaked information set has been added to the “Have I Been Pwned?” database.
HaveIBeenPwned (HIBP) is a free on-line service that enables customers to verify if their information was compromised in recognized information breaches.
The variety of breached data related to this incident added to the HIBP database is 2,842,669, with the service stating that 46% of those data had been already in its database.
Large Tiger prospects needs to be cautious of any suspicious emails or incoming communications that declare to be from the retailer. These might very seemingly be focused phishing makes an attempt from risk actors.
Though no fee data or passwords had been uncovered on this breach, signing up for an id monitoring service may very well be helpful to prospects in stopping them from turning into victims of id theft.
