A Cascade of Errors
Once I wrote Delphi code, I needed to compile code into binaries to run on Home windows. The compiler would not produce a binary except my code was semantically right. If the code was semantically right, however had potential logic errors, the compiler would situation warnings. My workforce all the time had an ironclad rule that we should always by no means commit code with warnings. (There have been additionally hints that resulted from semantically right, however syntactically meaningless, code. We additionally by no means needed to check-in code with hints…)
Generally a compilation would lead to many, many warnings. A fast examination would normally reveal the rationale and making one repair in a single spot would typically resolve all of the warnings.
The same factor can occur with safety vulnerabilities in your code. Generally, when doing a Static Evaluation Safety Testing (SAST) scan, you will get a ton of (seemingly) unrelated errors. You may have a look at that and suppose “Sweet Baby Elvis, this is going to take a long time to fix!” However concern not – our Static Utility Safety Testing (SAST) instrument could make it simpler so that you can clear these errors as shortly as attainable.
The Greatest Place
Fairly often, a single change to your code may cause most of the vulnerabilities in your code to go away. However it’s discovering that spot in your code can typically be the problem.
Checkmarx SAST has a characteristic referred to as “Best Fix Location,” or BFL for brief. The BFL is designed to seek out that “one fix, many vulnerabilities disappear” spot in your code. As a part of the scanning course of, our SAST will course of our code evaluation, after which attempt to discover the easiest place to repair any given alert. Fairly often, that remediates the foundation drawback for a lot of different points.
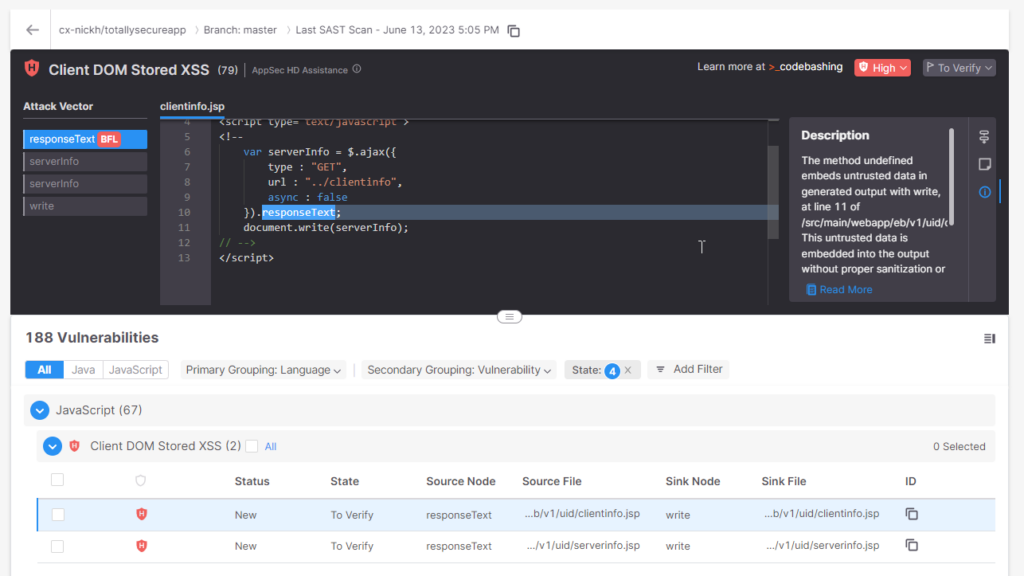
Above, you possibly can see the Checkmarx One interface exhibiting an alert in some JavaScript code that would result in a DOM Saved Cross-site Scripting assault. It is a frequent drawback that has a straightforward answer. Generally, it may be tough to determine the perfect place to begin.
Within the higher proper, you possibly can see hyperlinks to a series of assault vectors – locations {that a} malicious actor may attempt to place script code into your utility. The underside hyperlink is the road of code “closest to the surface”, and every line above it digs in slightly deeper.
The highest one, the fourth within the name stack, is the Greatest Repair Location. It’s the spot within the code that’s the “root of the problem.” Make a correction there, and it’s probably that different vulnerabilities that use that code at a “higher” level within the code will go away as effectively.
On this case, we will see that the responseText property will enable malicious customers to have the ability to place unsanitized code into our web page, leaving our utility open to assault.
How This All Works
Our SAST instruments do one thing that is named “Data Flow Analysis.” Knowledge Circulate Evaluation focuses on how information flows by means of the applying, exhibiting how information is handed between totally different statements or blocks of code. It tracks the connection between totally different variables, expressions, and operators in a specific program, and the way they’re used to compute values or change information. Our answer makes use of this data to seek out vulnerabilities in your code.
Knowledge Circulate Evaluation is far more useful resource intensive than another options that use Common Expressions or different methods of analyzing code. This trade-off is price it although, as a result of Knowledge Circulate Evaluation is a deep and thorough examination of not merely the code, however the best way the code works.
Getting It Mounted
Now the place the issue lies. However we don’t abandon you there. We are going to level you to sources that may enable you to perceive what the chance is, why it’s a danger, and the way to make the chance go away.
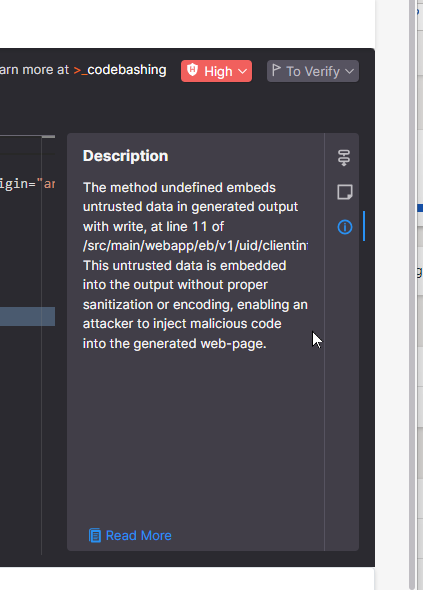
On the correct is a fast description of what the vulnerability is. It is possible for you to to proceed to be taught extra in regards to the vulnerability by following the “Read More” hyperlink. There you’ll be given a whole description of the difficulty, together with code examples of the issue occurring and really helpful options. As well as, we level you to sources inside our CodeBashing coaching answer that may give you much more data.
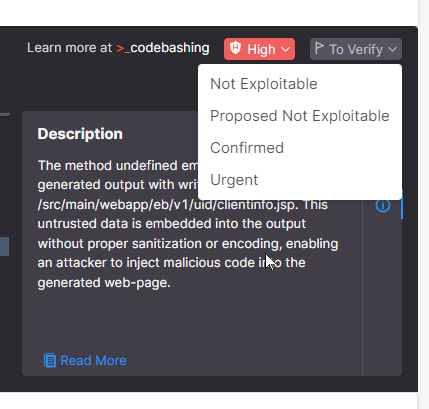
When you perceive the difficulty, we make it easy so that you can remediate it. your codebase, and so one of the simplest ways to maneuver ahead with this alert. Possibly it seems like an issue, however it isn’t. Possibly it is an issue and must be mounted in the end. Or possibly it must be mounted instantly. You need to use the dashboard to provide the difficulty a label to guarantee that it will likely be handled correctly, and so that it’s going to obtain the right stage of consideration.
Up to now, we’ve been taking a look at all of this within the Checkmarx One Dashboard. However if you’re a developer, you are able to do all of what we talked about right here proper inside your IDE. We now have plugin assist for VS Code, Visible Studio, JetBrains Final, and Eclipse. Our plugins allow you to run SAST scans to see, course of, and repair alerts with out leaving your instrument of alternative.
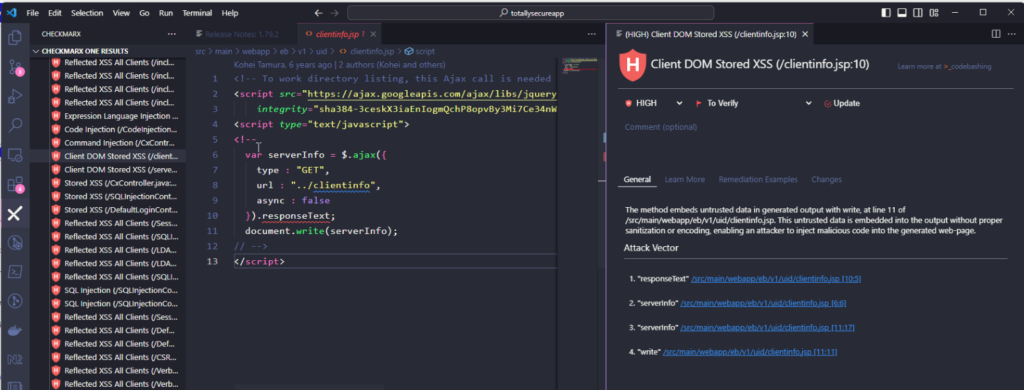
Looking down the situation of the issue is commonly the most important time-sink in coping with a code safety alert. Not having to even do the search is a big productiveness enhance. Getting all of the details about the issue and recommendation on the way to repair it’s the icing on the cake.
Ultimately, the Greatest Repair Location characteristic will provide you with all the pieces it’s worthwhile to make fast work of issues in your code.