KEY SUMMARY POINTS
- Google Calendar Focused: Hackers are exploiting Google Calendar’s options to ship phishing emails disguised as legit invitations.
- Refined Ways: Assaults leverage instruments like Google Types and Google Drawings to bypass conventional e-mail safety and improve credibility.
- Widespread Affect: Over 4,000 phishing emails linked to this marketing campaign had been detected in a four-week interval, affecting round 300 manufacturers.
- Social Engineering: Cybercriminals use urgency, concern, and impersonation to trick victims into clicking malicious hyperlinks and getting into delicate info.
- Preventive Measures: Superior e-mail safety, monitoring third-party app utilization, and habits analytics are important to mitigate these evolving threats.
In keeping with the most recent analysis from Examine Level, shared with Hackread.com, a extensively used scheduling software known as Google Calendar has develop into the latest goal for cybercriminals.
In your info, Google Calendar is a part of Google Workspace (previously often known as G Suite). It’s a fashionable software for organizing schedules and managing time utilized by over 500 million individuals in 41 languages.
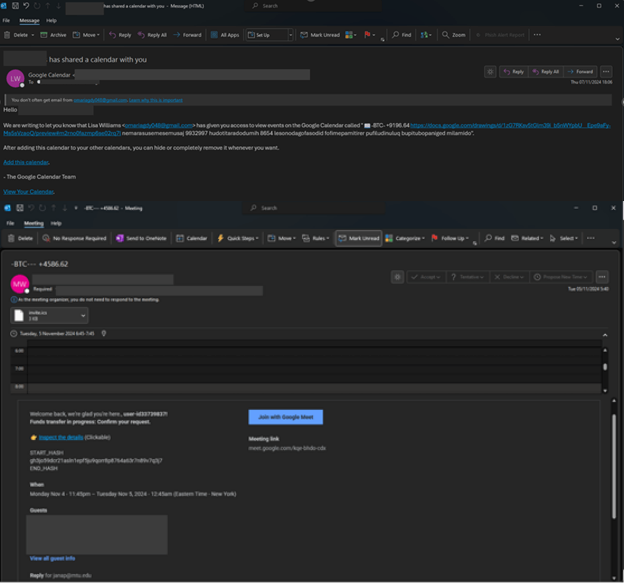
In keeping with CPR’s analysis, attackers are manipulating Google Calendar and its related options, like Google Drawings, to launch phishing assaults by sending seemingly legit emails with hyperlinks that bypass conventional e-mail safety measures. These hyperlinks seem to hook up with Google Types or Google Drawings, additional enhancing the assault’s credibility.
Initially, they exploited the user-friendly options inherent in Google Calendar, providing hyperlinks connecting to Google Types. Nevertheless, after observing that safety merchandise may flag malicious Calendar invitations, they developed the assault to align with Google Drawings capabilities.
“Cyber criminals are modifying “sender” headers, making emails look as if they had been despatched through Google Calendar on behalf of a recognized and legit particular person. Roughly 300 manufacturers have been affected by this marketing campaign so far, with cyber researchers observing over 4,000 of those phishing emails in a four-week interval,” revealed Examine Level’s weblog submit.
The attackers leverage the belief and familiarity related to Google Calendar to lure victims into clicking malicious hyperlinks. They create a seemingly legit calendar invite, typically from a recognized contact or a well-recognized group. This preliminary invite could comprise a hyperlink to a Google Kind Google Drawing or ICS file attachment, which seems to be a easy request for info or a survey, typically displaying a CAPTCHA or assist button.
Nevertheless, as soon as the sufferer clicks on the hyperlink, they’re redirected to a malicious web site designed to steal private info or company knowledge via a faux authentication course of, doubtlessly resulting in monetary scams. This web site would possibly mimic a legit login web page, a cryptocurrency trade, or a tech assist web page.
The aim is to trick the sufferer into getting into delicate info like passwords, bank card particulars, or private identification numbers. Stolen info can be utilized for bank card fraud or unauthorized transactions, posing vital dangers to each events.
It’s price noting that the attackers typically use social engineering ways to extend the credibility of the assault. They may create a way of urgency, concern, or curiosity to entice victims to click on on the malicious hyperlink. They could additionally impersonate trusted people or organizations to realize the sufferer’s belief.
To remain shielded from phishing threats, organizations ought to implement superior e-mail safety options, monitor third-party Google App utilization, implement sturdy authentication mechanisms, and use habits analytics instruments to detect uncommon login makes an attempt or suspicious actions to make sure a safe and safe on-line surroundings for all customers.