SUMMARY
- Cybercriminals are exploiting the Godot recreation engine to ship malware referred to as GodLoader, concentrating on a number of platforms like Home windows, macOS, and Linux.
- GodLoader hides malicious code in recreation recordsdata, bypassing antivirus detection and compromising over 17,000 gadgets since June 2024.
- The malware makes use of sandbox evasion, Microsoft Defender exclusions, and GitHub-hosted repositories to distribute assaults.
- GodLoader’s payloads embrace RedLine Stealer and cryptocurrency miners, affecting 1.2 million Godot recreation customers.
- The Godot group advises downloading software program from trusted sources and avoiding cracked recordsdata to remain protected.
Examine Level Analysis (CPR) has printed its newest analysis on a novel multi-platform method employed by cybercriminals to use the favored open-source recreation engine, Godot to ship a newly found malicious payload dubbed GodLoader after bypassing conventional safety measures.
The regarding facet is GodLoader’s cross-platform performance, making it efficient on macOS, Home windows, Linux, iOS, and Android. Though designed to focus on Home windows, it may be used on Linux and macOS with minimal changes. The malware is, reportedly, distributed through the Stargazers Ghost Community on GitHub, utilizing over 200 repositories and 225 accounts between September and October 2024.
“The threat actor behind this malware has been utilizing it since June 29, 2024, infecting over 17,000 machines,” and an assault can put 1.2 million customers of Godot-developed video games in danger, researchers famous within the weblog post.
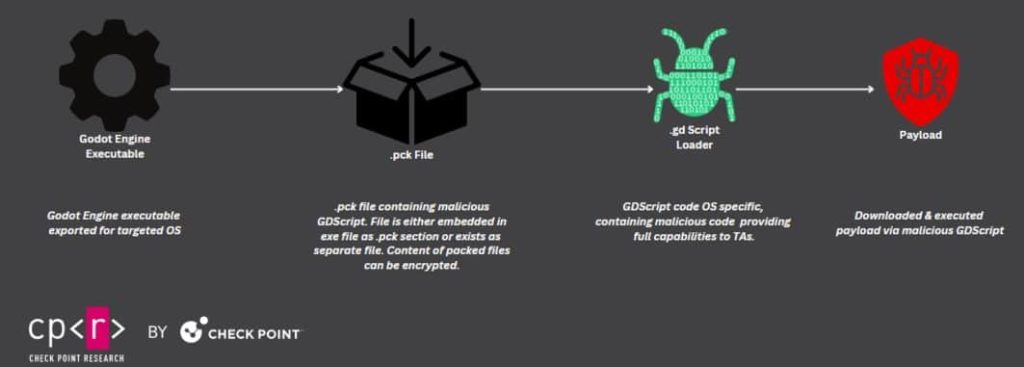
In keeping with CPR’s analysis, cybercriminals exploit the pliability of Godot’s scripting language, GDScript and embed malicious code inside recreation property, executing it when the sport is launched. It is a stealthy method, which permits attackers to bypass antivirus detection and compromise programs with out elevating alarms.
Additional probing revealed that it makes use of sandbox and digital machine detection, in addition to Microsoft Defender exclusions, to keep away from detection. The malware was hosted on Bitbucket.org and distributed throughout 4 assault waves, with preliminary payloads together with RedLine Stealer and XMRig cryptocurrency miners.
To your data, Godot is a robust instrument for recreation improvement that permits builders to bundle recreation property and scripts into .pck recordsdata, which comprise the sport’s sources, together with photos, sounds, and scripts. By injecting malicious GDScript code into these .pck recordsdata, attackers can trick the sport engine into executing dangerous instructions.
As quickly as the sport masses the contaminated .pck file, the hidden script springs into motion, downloading and deploying extra malware payloads onto the sufferer’s machine.
Godot Engine’s Assertion
The Godot Engine improvement group, in response, has issued an announcement, explaining that GodLoader doesn’t exploit a particular weak point in Godot itself as a result of like all programming language (e.g. Python or Ruby) Godot additionally permits the creation of each good and unhealthy packages. Although the malware exploits Godot’s scripting language (GDScript) to ship its payload, this doesn’t make Godot inherently unsafe.
The group additionally famous that it isn’t a one-click exploit as a result of the GodLoader malware methods customers into downloading/executing a seemingly innocent file (usually a .pck file disguised as a software program crack). This file wouldn’t work by itself and the attackers additionally should present the Godot runtime (.exe file) individually to make it profitable. This implies customers must take a number of steps to put in the malware, making it much less more likely to be a one-click exploit.
Nonetheless, group Godot emphasizes the significance of excellent safety habits and downloading from trusted sources like official web sites, established distribution platforms, or trusted people. Home windows and macOS customers ought to test for signed executables and notarization by a trusted social gathering and keep away from utilizing cracked software program as it’s a frequent goal for malicious actors.
RELATED TOPICS
- Gcore Thwarts 500M PPS DDoS Assault on Gaming Agency
- What’s Blockchain Gaming and its Play-to-Earn Mannequin?
- Exploring Knowledge Privateness and Safety in B2B Gaming Knowledge
- Winos4.0 Malware Hits Home windows through Pretend Gaming Apps
- Gaming Corporations, Neighborhood Members Hit by Darkish Frost Botnet