GitLab has launched safety updates to handle a essential SAML authentication bypass vulnerability impacting self-managed installations of the GitLab Neighborhood Version (CE) and Enterprise Version (EE).
Safety Assertion Markup Language (SAML) is a single sign-on (SSO) authentication protocol that permits customers to log in throughout completely different companies utilizing the identical credentials.
The flaw, tracked as CVE-2024-45409, arises from a difficulty within the OmniAuth-SAML and Ruby-SAML libraries, which GitLab makes use of to deal with SAML-based authentication.
The vulnerability happens when the SAML response despatched by an id supplier (IdP) to GitLab accommodates a misconfiguration or is manipulated.
Particularly, the flaw entails inadequate validation of key components within the SAML assertions, such because the extern_uid (exterior person ID), which is used to uniquely determine a person throughout completely different methods.
An attacker can craft a malicious SAML response that methods GitLab into recognizing them as authenticated customers, bypassing SAML authentication and getting access to the GitLab occasion.
The CVE-2024-45409 flaw impacts GitLab 17.3.3, 17.2.7, 17.1.8, 17.0.8, 16.11.10, and all prior releases of these branches.
The vulnerability is addressed in GitLab variations 17.3.3, 17.2.7, 17.1.8, 17.0.8, and 16.11.10, the place OmniAuth SAML has been upgraded to model 2.2.1 and Ruby-SAML to 1.17.0.
“We strongly recommend that all installations running a version affected by the issues described below are upgraded to the latest version as soon as possible,” warns GitLab within the bulletin.
No motion must be taken for customers of GitLab Devoted situations on GitLab.com, as the difficulty impacts solely self-managed installations.
For individuals who can not improve to a protected model instantly, GitLab suggests enabling two-factor authentication (2FA) for all accounts, and setting the SAML 2FA bypass choice to “do not allow.”
Indicators of exploitation
Whereas GitLab has not said that the flaw was beforehand exploited, they did present indicators of tried or profitable exploitation within the bulletin, suggesting that malicious actors may already be leveraging the flaw in assaults.
The indicators of tried or profitable exploitation are:
- Errors associated to RubySaml::ValidationError (unsuccessful makes an attempt).
- New or uncommon extern_uid values in authentication logs (profitable makes an attempt).
- Lacking or incorrect info in SAML responses.
- A number of extern_uid values for a single person (signifies potential account compromise).
- SAML authentication from an unfamiliar or suspicious IP tackle in comparison with the person’s standard entry patterns.
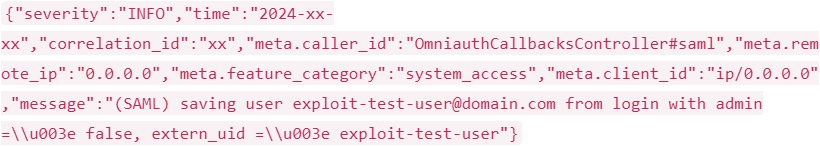
Supply: GitLab
BleepingComputer contacted GitLab yesterday to ask about whether or not or not they’ve noticed energetic exploitation of CVE-2024-45409 within the wild, however we’re nonetheless awaiting a response.
