BleepingComputer lately reported how a GitHub flaw, or presumably a design choice, is being abused by risk actors to distribute malware utilizing URLs related to Microsoft repositories, making the recordsdata seem reliable.
It now seems, GitLab can also be affected by this challenge and could possibly be abused in an identical method.
Whereas many of the malware-associated exercise was based mostly across the Microsoft GitHub URLs, this “flaw” could possibly be abused with any public repository on GitHub or GitLab, permitting risk actors to create very convincing lures.
GitLab feedback may also be abused to push malware
On Saturday, BleepingComputer reported how risk actors have been abusing GitHub feedback to push malware whereas making it look like the malicious recordsdata had been hosted on official supply code repos of credible organizations.
The next URLs, for instance, which had been used within the assault made it look like these ZIPs had been current on Microsoft’s supply code repo:
https://github[.]com/microsoft/vcpkg/recordsdata/14125503/Cheat.Lab.2.7.2.zip
https://github[.]com/microsoft/STL/recordsdata/14432565/Cheater.Professional.1.6.0.zip
Following our investigation, nevertheless, we realized that these recordsdata—that are malware, had been nowhere to be discovered on Microsoft’s code repo.
Relatively, these existed on GitHub’s CDN and had been seemingly uploaded by a risk actor who abused the platform’s “comments” characteristic.
When leaving a touch upon a commit or pull request, a GitHub consumer can connect a file (archives, paperwork, and many others), which shall be uploaded to GitHub’s CDN and related to the associated mission utilizing a singular URL on this format: ‘https://www.github.com/{project_user}/{repo_name}/recordsdata/{file_id}/{file_name}.‘
For movies and pictures, the recordsdata shall be saved beneath the /belongings/ path as a substitute.
As a substitute of producing the URL after a remark is posted, GitHub robotically generates the obtain hyperlink after you add the file to an unsaved remark, as proven beneath. This enables risk actors to connect their malware to any repository with out them realizing.
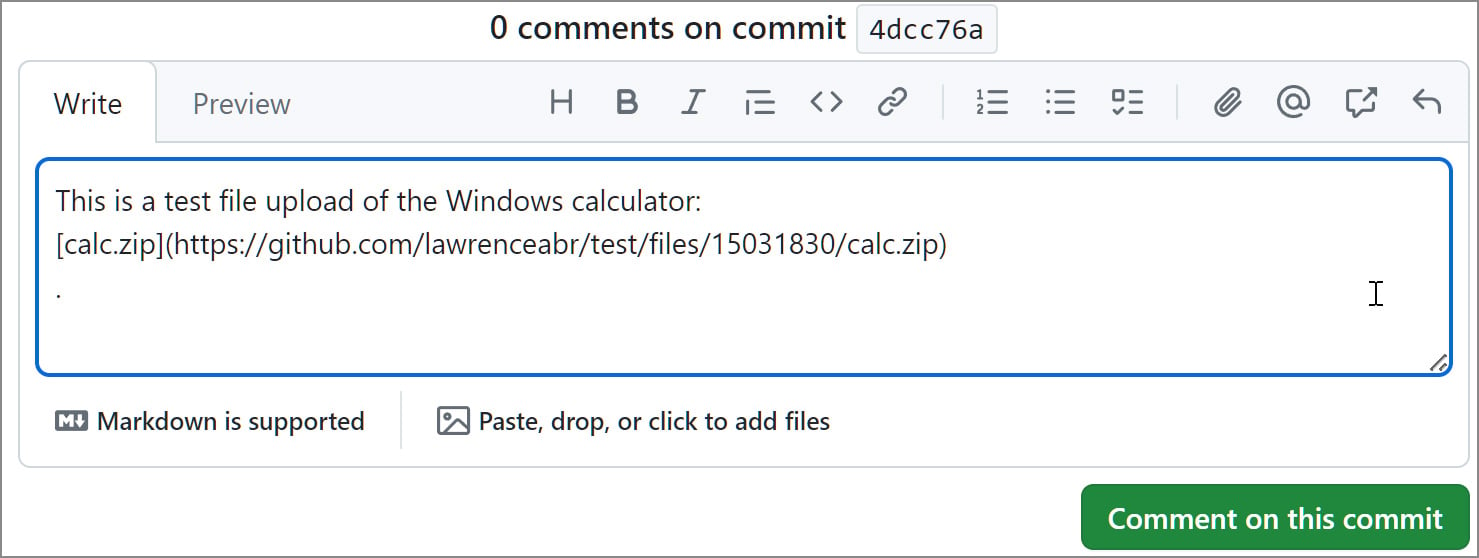
Supply: BleepingComputer
Even when the remark isn’t really posted or later deleted by the consumer (or an attacker), the hyperlink to the file stays stay.
Sergei Frankoff, of automated malware evaluation service UNPACME, had livestreamed about this bug simply final month, saying that risk actors had been actively abusing it.
Shortly after our reporting, readers identified that GitLab was not immune from this challenge both.
BleepingComputer can verify that customers can certainly abuse the “comments” characteristic on GitLab in a similar way.
In our checks, we had been capable of add recordsdata that will get uploaded to GitLab’s CDN however appear to be these existed with GitLab repos of common open supply initiatives like Inkscape and Wireshark:
https://gitlab[.]com/inkscape/inkscape/uploads/edfdbc997689255568a7c81db3f3dc51/InkScape-2024-Newest.exe
https://gitlab[.]com/wireshark/wireshark/uploads/b4162053fbb4dc6ee4f673c532009e16/WireShark-v4.2.4-stable-release.exe
The file used in our check is a benign JPG picture, renamed to .exe to reveal how, by abusing this characteristic, risk actors can mislead customers into downloading counterfeit software program releases laced with malware.
The format adopted by such recordsdata uploaded to GitLab CDN is:
https://gitlab.com/{project_group_namr}/{repo_name}/uploads/{file_id}/{file_name}
The file_id right here seems to be like an MD4 or MD5 hash versus a less complicated numeric identifier.
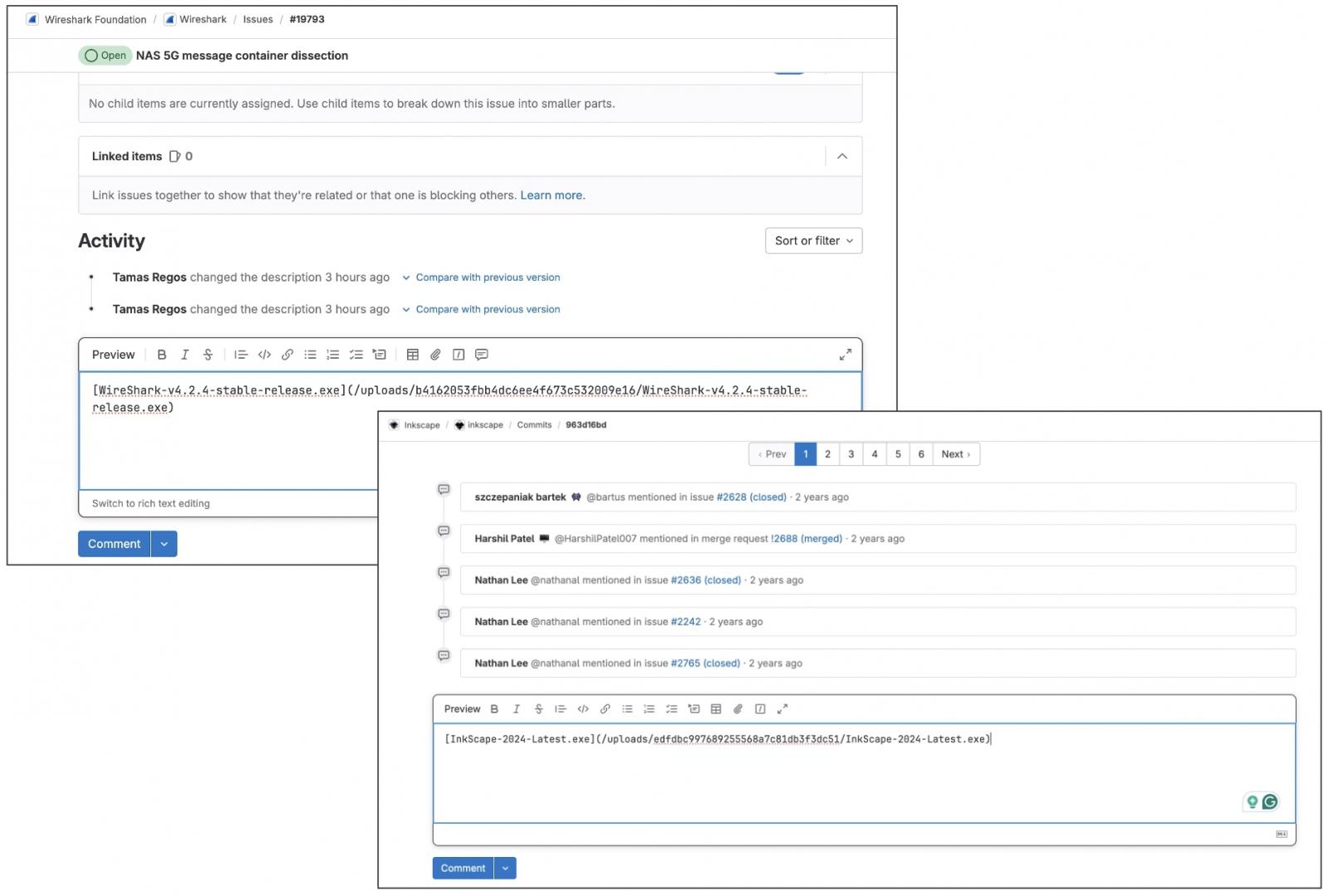
Supply: BleepingComputer
Very similar to with GitHub, the generated GitLab file hyperlinks would stay alive even when the remark was by no means posted by the attacker or later deleted.
GitLab does immediate customers to register earlier than they will add or obtain these recordsdata, however that does nothing to stop risk actors from importing these recordsdata within the first place.
Since nearly each software program firm makes use of GitHub or GitLab, this flaw allow permit risk actors to develop terribly artful and reliable lures.
For instance, a risk actor might add a malware executable in NVIDIA’s driver installer repo that pretends to be a brand new driver fixing points in a well-liked sport. Or a risk actor might add a file in a remark to the Google Chromium supply code and faux it is a new check model of the net browser.
These URLs would additionally seem to belong to the corporate’s repositories, making them much more reliable.
Sadly, even when an organization learns their repos are abused to distribute malware, we couldn’t discover any settings that will permit them to handle or delete recordsdata connected to their initiatives.
BleepingComputer contacted each GitHub and Microsoft on Thursday, April 18th about this abuse however didn’t obtain a response. We’ve got additionally approached GitLab for remark upfront of publishing and are awaiting a response.
