A GitHub flaw, or probably a design choice, is being abused by menace actors to distribute malware utilizing URLs related to a Microsoft repository, making the information seem reliable.
Whereas many of the malware exercise has been based mostly across the Microsoft GitHub URLs, this “flaw” might be abused with any public repository on GitHub, permitting menace actors to create very convincing lures.
Abusing GitHub’s file add function
Yesterday, McAfee launched a report on a new LUA malware loader distributed by way of what gave the impression to be a official Microsoft GitHub repository for the “C++ Library Manager for Windows, Linux, and MacOS,” often known as vcpkg.
The URLs for the malware installers, proven beneath, clearly point out that they belong to the Microsoft repo, however we couldn’t discover any reference to the information within the mission’s supply code.
https://github[.]com/microsoft/vcpkg/information/14125503/Cheat.Lab.2.7.2.zip
https://github[.]com/microsoft/STL/information/14432565/Cheater.Professional.1.6.0.zip
Discovering it unusual {that a} Microsoft repo could be distributing malware since February, BleepingComputer seemed into it and located that the information usually are not a part of vcpkg however have been uploaded as a part of a remark left on a commit or challenge within the mission.
When leaving a remark, a GitHub consumer can connect a file, which will probably be uploaded to GitHub’s CDN and related to the associated mission utilizing a singular URL on this format: ‘https://www.github.com/{project_user}/{repo_name}/information/{file_id}/{file_name}.‘
As a substitute of producing the URL after a remark is posted, GitHub robotically generates the obtain hyperlink after you add the file to an unsaved remark, as proven beneath. This permits menace actors to connect their malware to any repository with out them realizing.
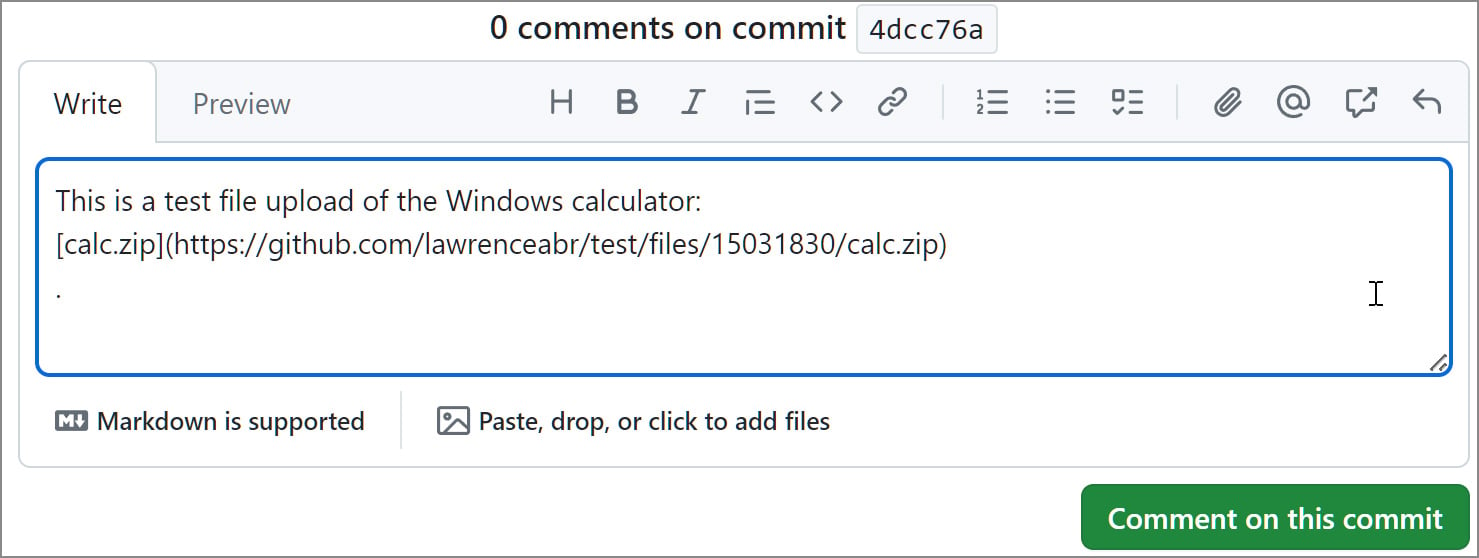
Supply: BleepingComputer
Even in the event you determine to not submit the remark or delete it after it’s posted, the information usually are not deleted from GitHub’s CDN, and the obtain URLs proceed to work without end.
Because the file’s URL comprises the identify of the repository the remark was created in, and as virtually each software program firm makes use of GitHub, this flaw can enable menace actors to develop terribly artful and reliable lures.
For instance, a menace actor might add a malware executable in NVIDIA’s driver installer repo that pretends to be a brand new driver fixing points in a well-liked recreation. Or a menace actor might add a file in a remark to the Google Chromium supply code and fake it is a new take a look at model of the net browser.
These URLs would additionally seem to belong to the corporate’s repositories, making them way more reliable.
Sadly, even when an organization learns their repos are abused to distribute malware, BleepingComputer couldn’t discover any settings that let you handle information hooked up to your initiatives.
Moreover, you may solely shield a GitHub account from being abused on this method and tarnishing your popularity by disabling feedback. In response to this GitHub help doc, you may solely quickly disable feedback for a most of six months at a time.
Nonetheless, proscribing feedback can considerably influence a mission’s growth because it is not going to enable customers to report bugs or recommendations.
Sergei Frankoff, of automated malware evaluation service UNPACME, did a livestream on Twitch about this bug simply final month, saying that menace actors have been actively abusing it.
Weeks later… GitHub bug nonetheless dropping malware pic.twitter.com/s165zOAsoI
— herrcore (@herrcore) March 27, 2024
As a part of our analysis into this bug, BleepingComputer might solely discover one different repo, httprouter, abused to distribute malware on this method, and it was the identical ‘Cheater.Professional.1.6.0.zip’ as seen in Microsoft’s URLs.
Nonetheless, Frankoff advised BleepingComputer that they found an identical marketing campaign in March that makes use of the identical LUA loader malware, which is named SmartLoader, disguised because the Aimmy cheat software program.
Frankoff advised BleepingComputer that SmartLoader is usually put in alongside different payloads, such because the RedLine information-stealing malware.
BleepingComputer contacted each GitHub and Microsoft on Thursday about this abuse however didn’t obtain a response.
On the time of this publication, the information-stealing malware remains to be being distributed by way of hyperlinks related to Microsoft’ GitHub repository.
