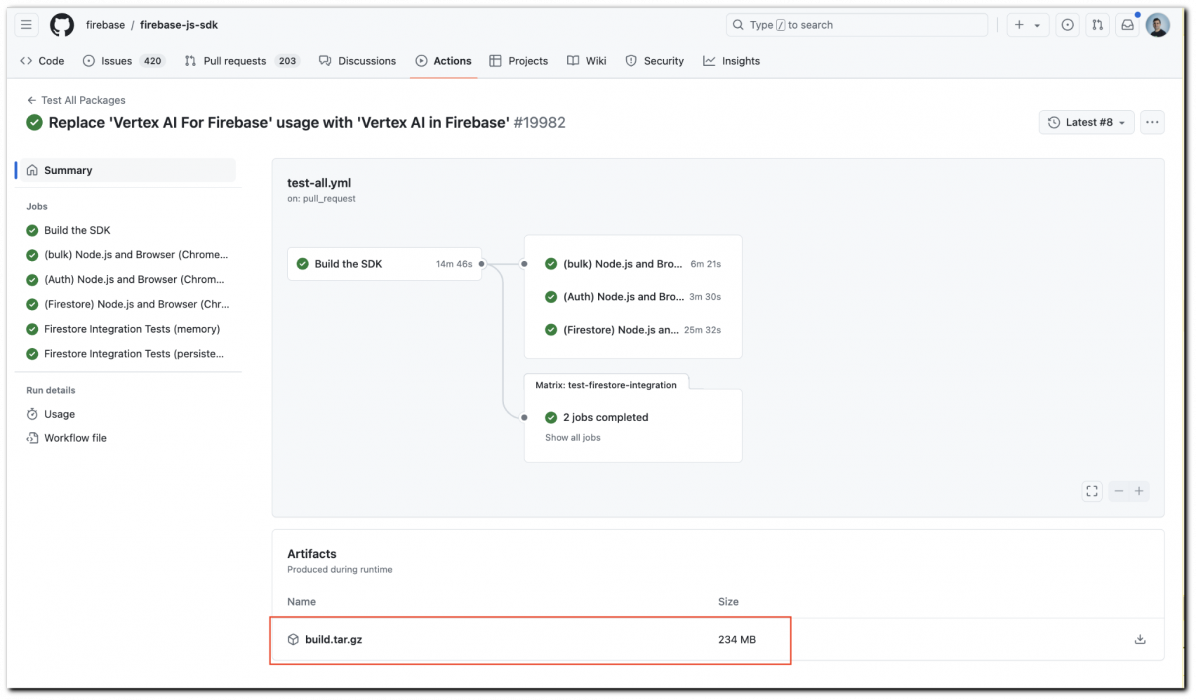
A number of high-profile open-source tasks, together with these from Google, Microsoft, AWS, and Crimson Hat, had been discovered to leak GitHub authentication tokens by GitHub Actions artifacts in CI/CD workflows.
Attackers stealing these tokens might achieve unauthorized entry to non-public repositories, steal supply code, or inject malicious code into tasks.
The invention by Palo Alto Networks’ Unit 42 prompted motion by house owners of standard repositories the place secrets and techniques had been leaked by GitHub Actions artifacts. Nevertheless, the underlying issues stay unfixed as GitHub determined to not tackle the danger, inserting the duty on customers to safe their artifacts.
Given the scenario, GitHub customers want to grasp the dangers, consider their publicity, and take measures to forestall leaks sooner or later.
Supply: Unit 42
Leaking GitHub tokens
Unit 42’s report highlights a mix of things, together with insecure default settings, person misconfiguration, and inadequate safety checks, that may result in the leakage of GitHub tokens in what they name an “ArtiPACKED” assault.
The primary threat level is the ‘actions/checkout’ motion, generally utilized in GitHub workflows to clone the repository code in order that it’s out there through the workflow run.
By default, this motion persists the GitHub token to the native .git listing (hidden) as required for authenticated operations throughout the workflow.
If a person mistakenly uploads your complete checkout listing as a part of an artifact, the GitHub token contained in the git folder will now be uncovered.

Supply: Unit 42
Different delicate info that is likely to be contained in that folder embody API keys, cloud service entry tokens, and varied account credentials.
The same publicity by misguided artifact uploads can occur by artifacts generated through the CI/CD course of, equivalent to construct outputs and take a look at outcomes, that are saved and accessible for as much as three months.
One other level of failure is CI/CD pipelines that use setting variables to retailer GitHub tokens. If actions or scripts throughout the workflow log these variables, both purposefully or by mistake, the logs are uploaded as artifacts.
Unit 42 notes that the ‘super-linter’ motion can create detailed logs that embody setting variants when the ‘CREATE_LOG_FILE’ property is ready to ‘True.’
Exploiting the leakages
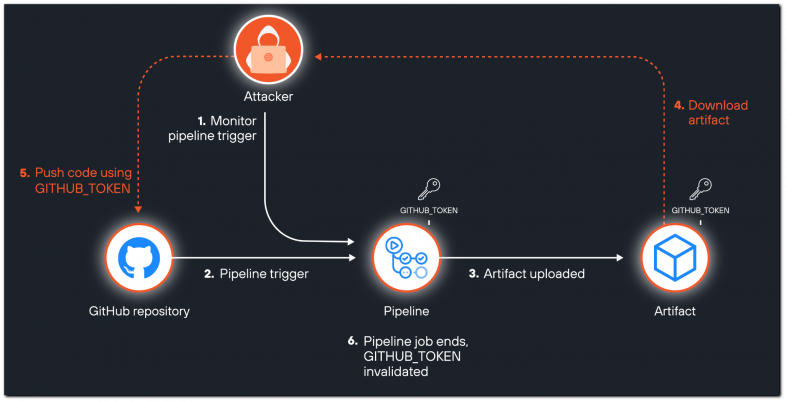
In the end, attackers would search to use particular race situation situations the place the ephemeral GitHub tokens should be extracted from logs and used earlier than they expire.
GitHub tokens stay legitimate all through the workflow job, so their exploitation potential varies per case.
The ‘Actions_Runtime_Token,’ used internally by GitHub for caching and managing artifacts, is usually legitimate for six hours, so the exploitation window is small.
Customized secrets and techniques and tokens, equivalent to API keys or entry tokens for cloud providers, have various lifespans, from a couple of minutes to by no means expire.
Unit 42 presents an assault situation that identifies tasks or public repositories that use GitHub Actions and makes use of automated scripts to scan them for standards that improve the chance of artifact technology.
A unique set of scripts might robotically obtain artifacts from the CI/CD pipelines of goal repositories, which is an easy course of within the case of public repositories. Then, it will scrutinize them for secrets and techniques.
Supply: Unit 42
Mitigation
Unit 42 recognized the next 14 circumstances of enormous open-source tasks exposing artifacts with GitHub tokens and reported it to the affected events for remediation:
- Firebase (Google)
- OpenSearch Safety (AWS)
- Clair (Crimson Hat)
- Lively Listing System (Adsys) (Canonical)
- JSON Schemas (Microsoft)
- TypeScript Repos Automation, TypeScript Bot Check Triggerer, Azure Draft (Microsoft)
- CycloneDX SBOM (OWASP)
- Stockfish
- Libevent
- Guardian for Apache Kafka (Aiven-Open)
- Git Annex (Datalad)
- Penrose
- Deckhouse
- Concrete-ML (Zama AI)
Normally, GitHub customers are really useful to keep away from together with total directories in uploaded artifacts, sanitize logs, and usually assessment CI/CD pipeline configurations.
The default settings for harmful actions like ‘actions/checkout’ ought to be adjusted so credentials don’t persist. Moreover, token permissions utilized in workflows ought to be set to the least privilege essential to restrict harm in case they’re uncovered.
