Tremendous Low RPO with Steady Knowledge Safety:
Dial Again to Simply Seconds Earlier than an Assault
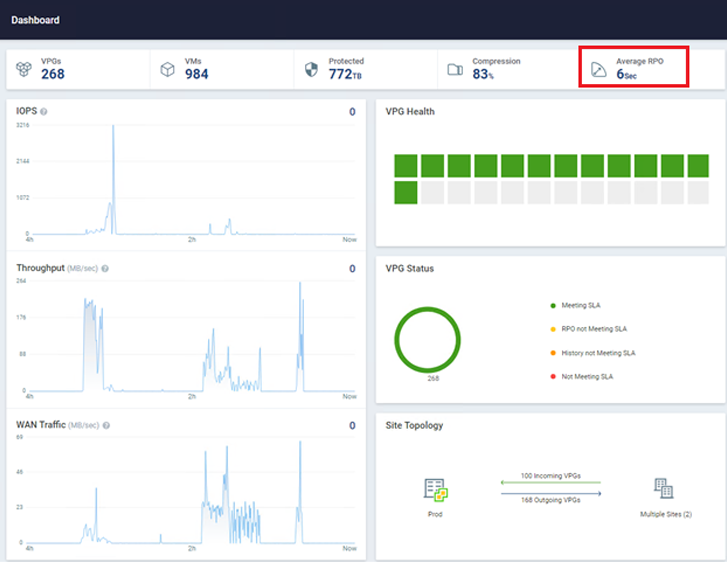
Zerto, a Hewlett Packard Enterprise firm, can assist you detect and get well from ransomware in close to real-time. This resolution leverages steady information safety (CDP) to make sure all workloads have the bottom restoration level goal (RPO) doable. Essentially the most worthwhile factor about CDP is that it doesn’t use snapshots, brokers, or some other periodic information safety methodology. Zerto has no affect on manufacturing workloads and might obtain RPOs within the area of 5-15 seconds throughout hundreds of digital machines concurrently. For instance, the surroundings within the picture under has almost 1,000 VMs being protected with a mean RPO of simply six seconds!
Software-Centric Safety:
Group Your VMs to Achieve Software-Stage Management
You possibly can shield your VMs with the Zerto application-centric method utilizing Digital Safety Teams (VPGs). This logical grouping of VMs ensures that your entire utility stacks might be recovered in a single cohesive unit, with checkpoints taken solely seconds aside from the very same time limit throughout a number of VMs within the group.
Actual-Time, In-Line Encryption Detection:
Obtain Early Warning When an Assault Happens
Zerto can detect doable ransomware assaults in real-time, in contrast to different merchandise that want to attend for a backup to finish earlier than scanning the information. Zerto scans information in-line in real-time as it’s being replicated, supplying you with the earliest warning signal of a possible cyberattack occurring inside your surroundings.
Let’s check out what a ransomware assault and Zerto restoration appear like.
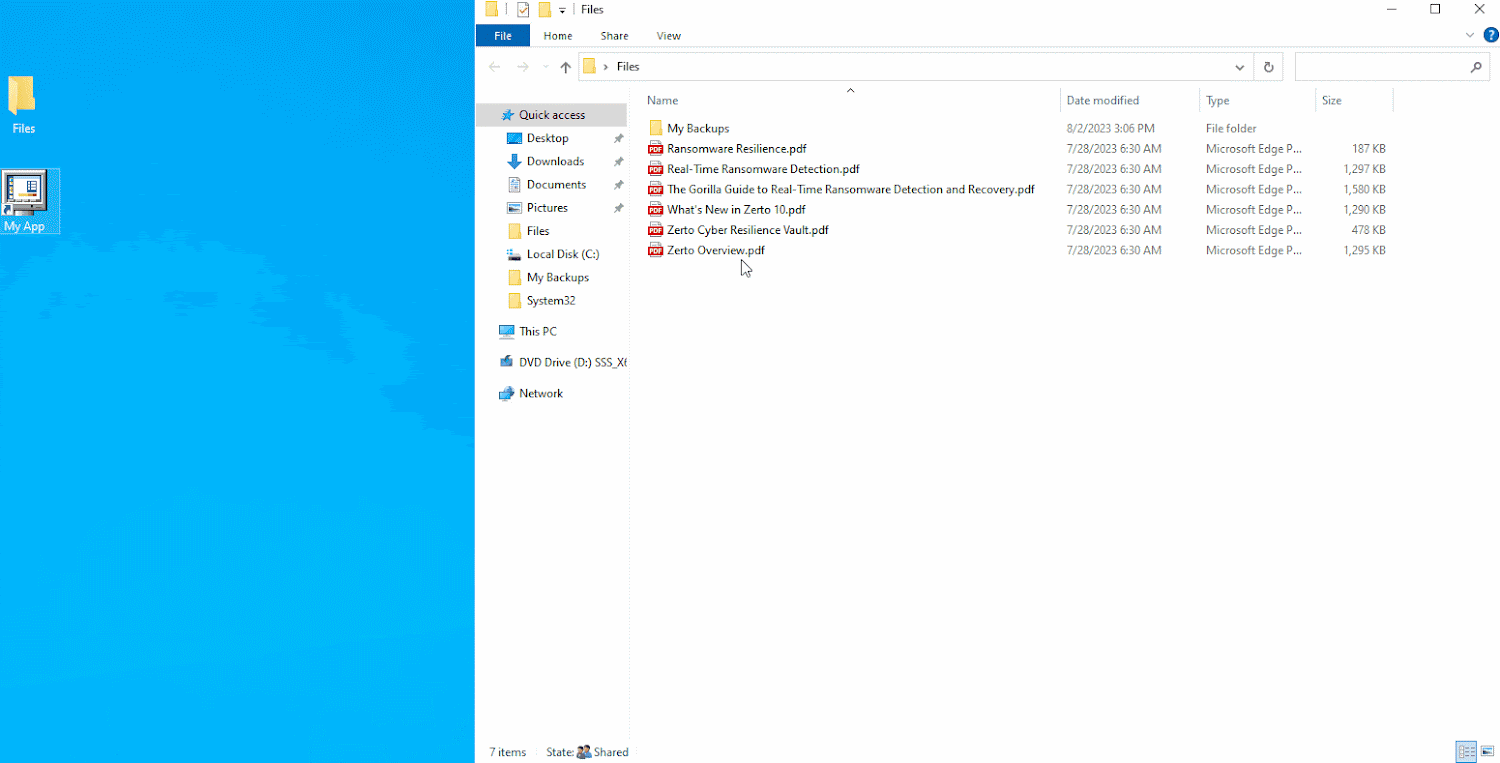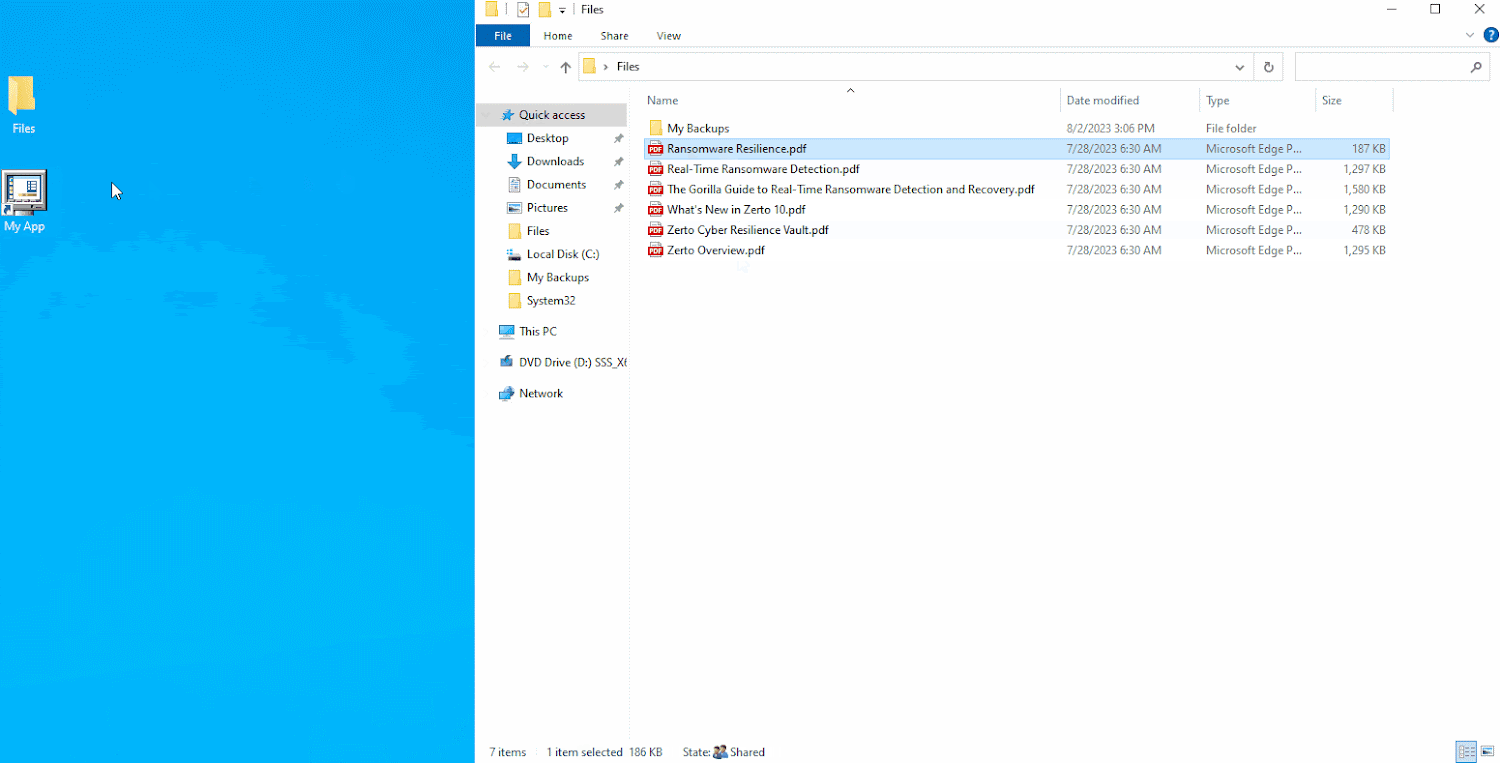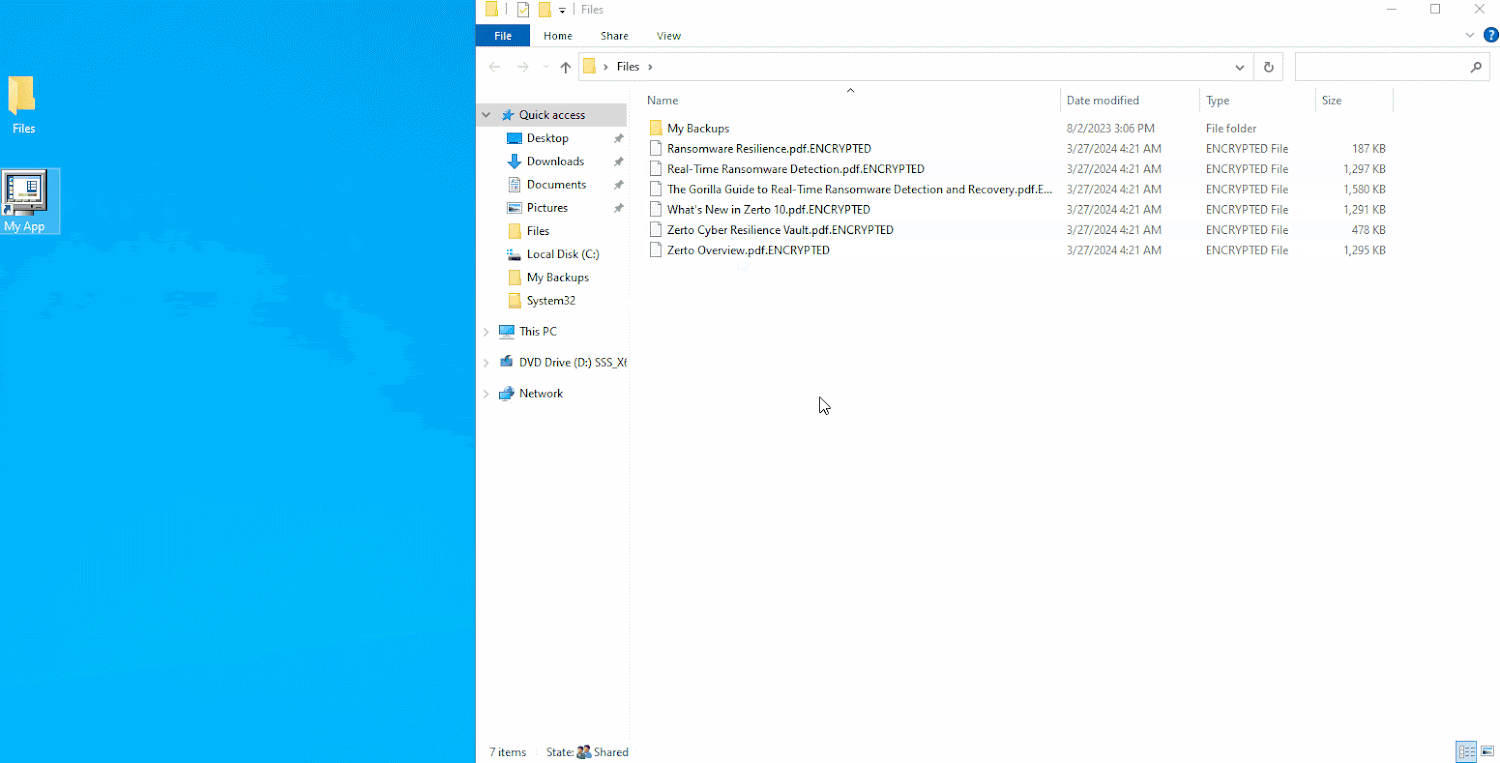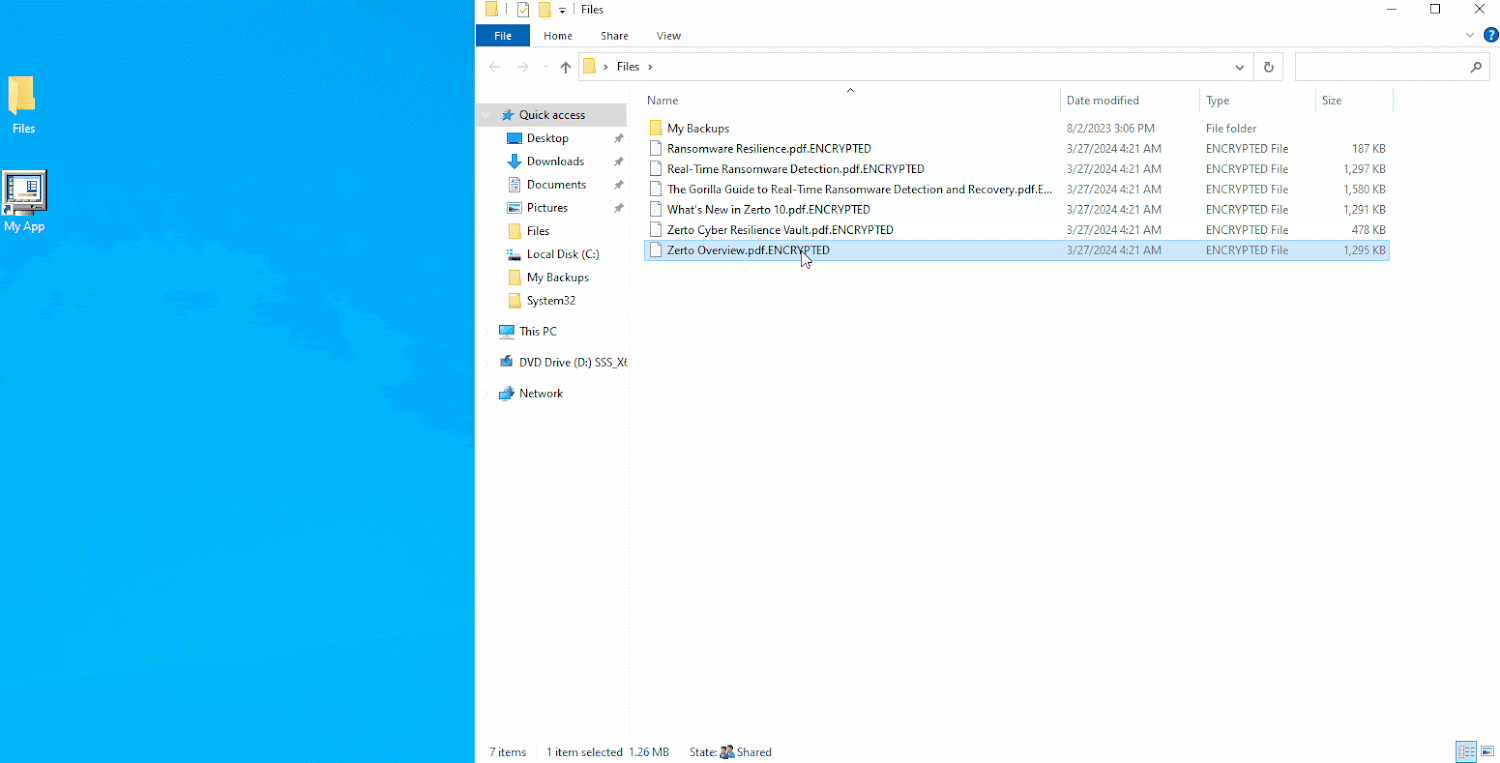
In a real-life cyberattack situation, you would not knowingly encrypt your information. It is obvious that the file server on this graphic has been contaminated with ransomware, which encrypted the information hosted inside it.
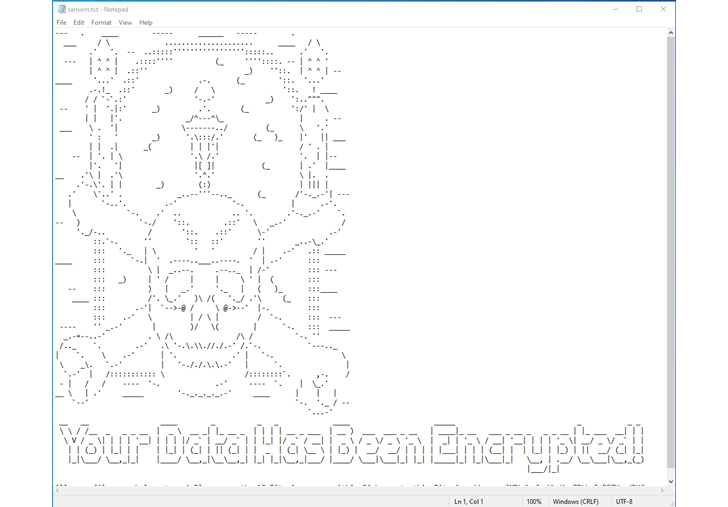
After a ransomware assault, information will all be encrypted and can’t be used.
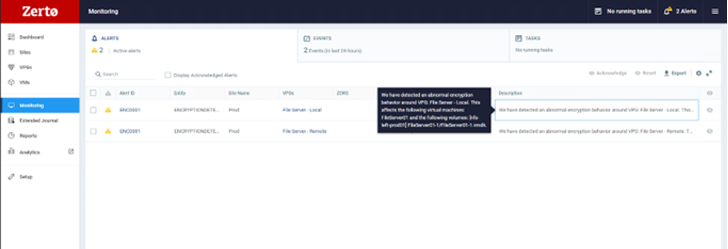
Utilizing Zerto, early in a cyberattack, you may see a triggered warning in your Zerto console, indicating potential suspicious exercise in your VM. You possibly can drill all the way down to see the precise disk the anomalous exercise is being generated from, permitting you to rapidly determine contaminated machines, restrict blast radius, and create a timeline of occasions to assist in investigations and forensics post-recovery, as proven on this picture.
Immediate File Stage Restoration:
Restore an Software or a VM—or Even Drill Right down to a Single File
Upon an assault, you may obtain automated alerts by way of e-mail or notifications from the Zerto extensible APIs, enabling you to take motion rapidly. You possibly can restore information instantly again into the VM in actual time, from solely seconds earlier than the encryption occasion, making certain minimal information loss.
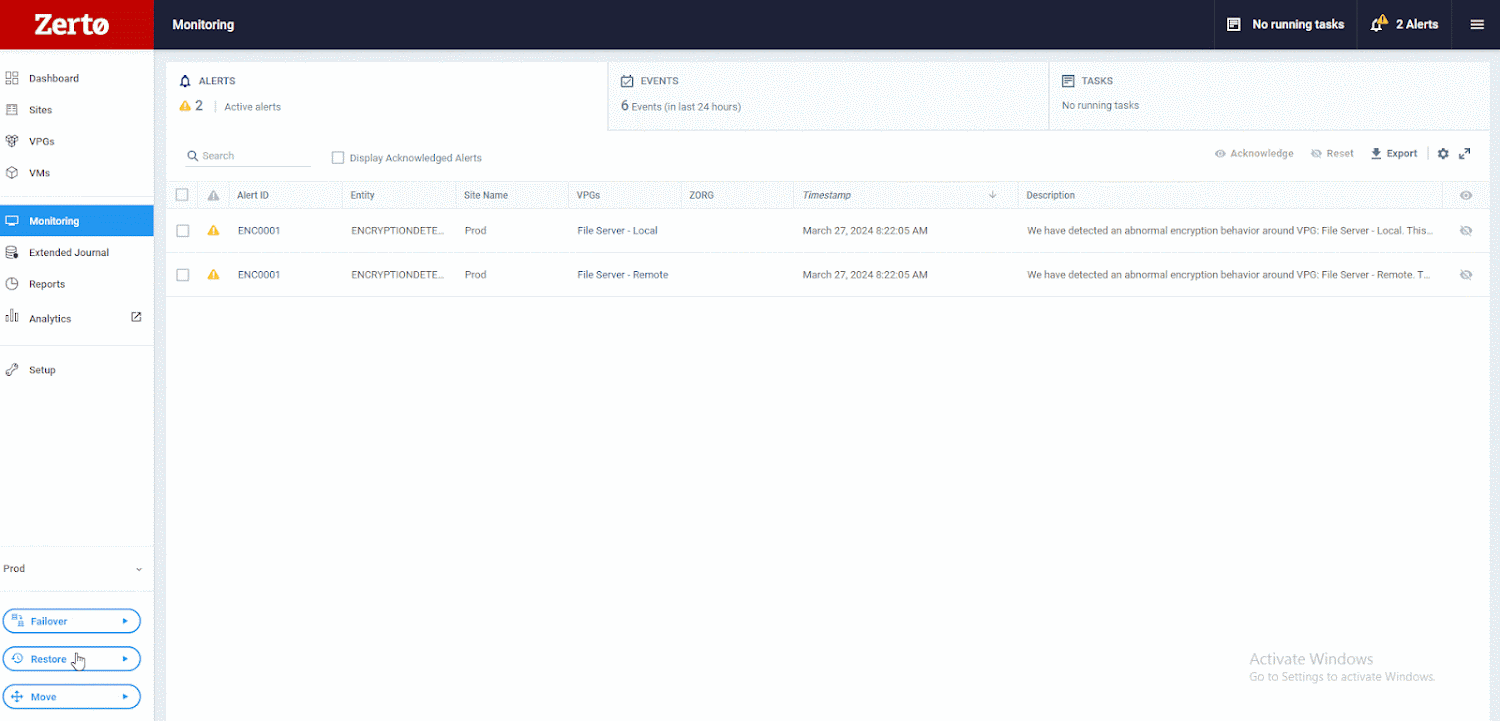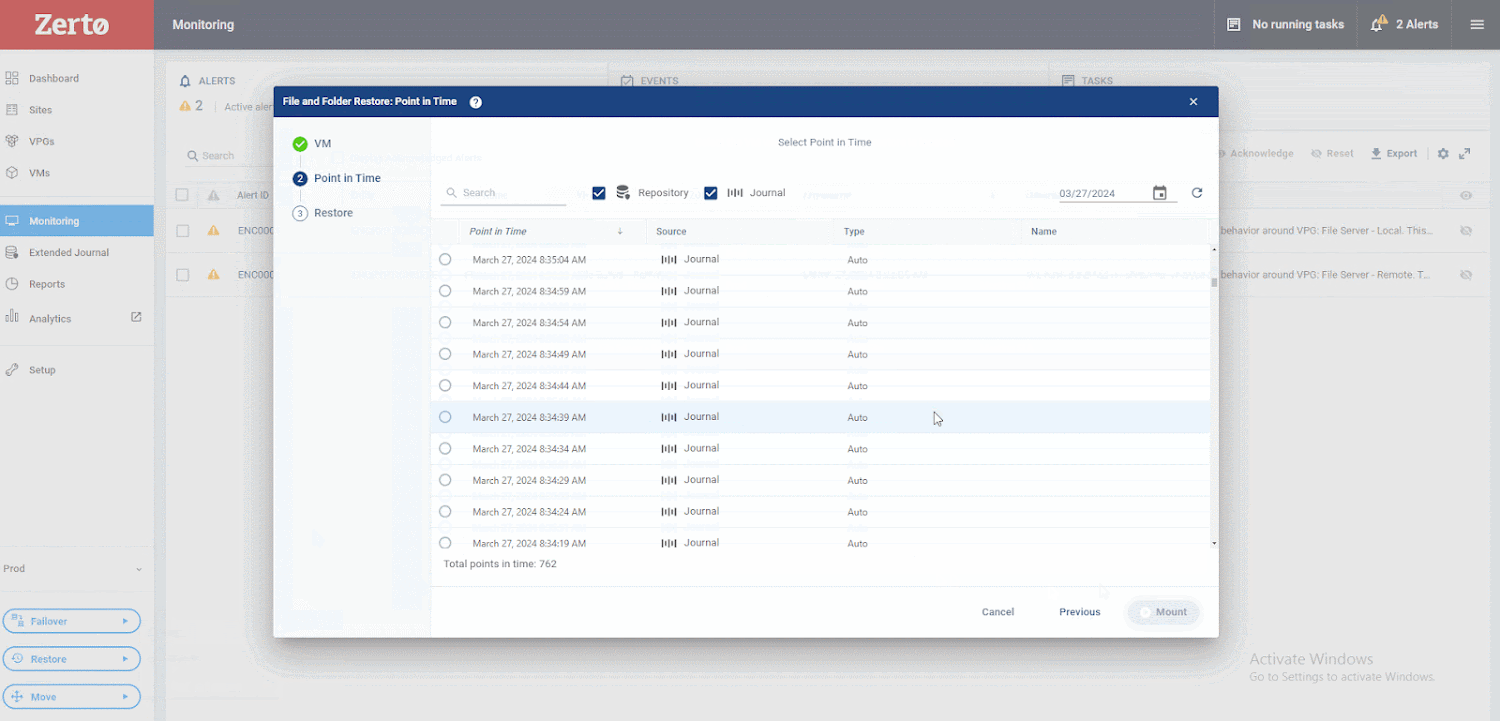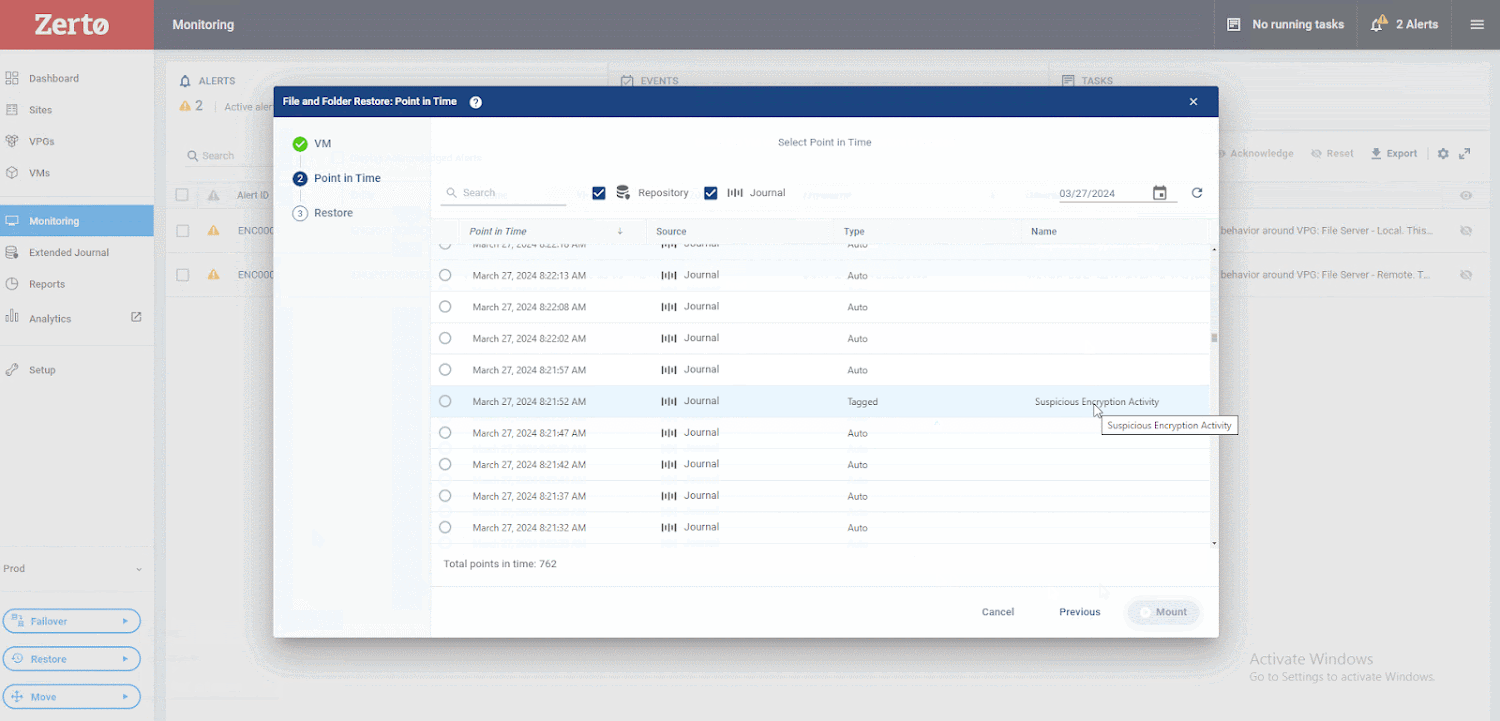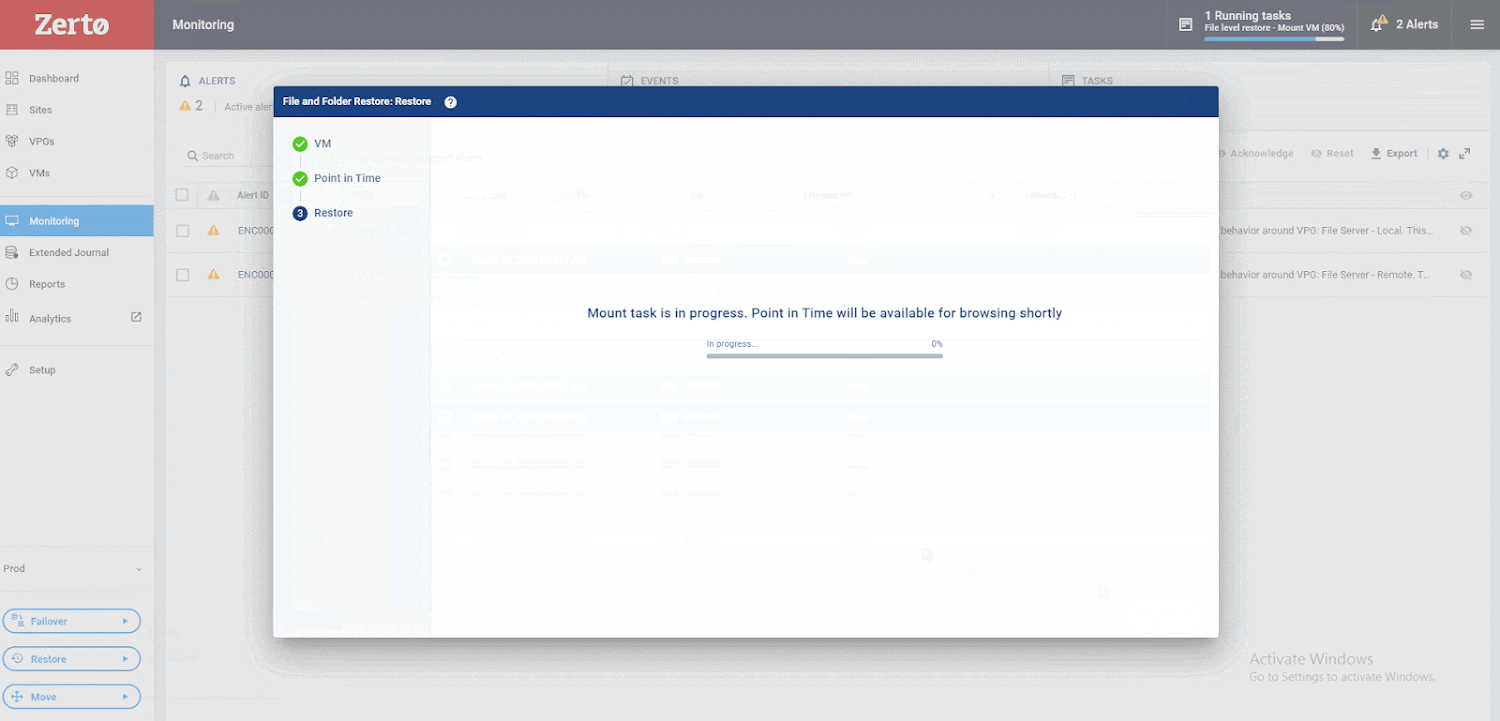
The graphic under exhibits how. First, choose Restore, then Information.
Subsequent, select the VM you wish to restore from and to. As soon as you’ve got made these choices, you may browse Zerto’s distinctive journaling capabilities. You may discover there are over 700 cut-off dates, solely seconds aside, which you could get well from. This ensures your RPO is as little as doable. Then, you may evaluation these checkpoints, figuring out those Zerto has tagged as suspicious. Afterward, you may return a little bit additional and look at those marked as clear. This course of lets you get well instantly earlier than suspicious exercise was detected.
Now, you may browse the information and folders you want to restore utilizing a easy wizard. Choose the information you wish to restore, select a set of credentials to authenticate into the VM, and hit Restore,
as proven under. Your information will now get well instantly again into manufacturing with out the usage of any brokers contained in the OS and with solely seconds of knowledge loss.
The restoration course of is straightforward and quick to attain, with minimal disruption to any group.
Now, let’s contemplate how we might get well within the occasion of a larger-scale assault that impacts a number of VMs and even tons of concurrently. By utilizing the failover perform inside Zerto, you may set off a full failover of all chosen VPGs and the VMs inside them to a secondary website. This secondary website might be one other VMware website, Hyper-V, or perhaps a public cloud. With full automation and orchestration, a Zerto failover can obtain advantages like these:
- 1000’s of VMs with an RTO of minutes
- Full re-IP of every VM, if required
- Restoring instantly onto production-grade storage of your selection with no further migrations required (comparable to Storage vMotion)
- Restoring instantly again onto production-grade compute with none additional steps comparable to vMotion
Any such restoration is right for cyber restoration as a result of large-scale recoveries might be troublesome to attain with backup instruments that aren’t designed for restoration at scale.
Quick Failover to Secondary Website with Full Automation and Orchestration: Mobilize, Transfer, and Get well with Automated Processes
As you may see, Zerto has some distinctive and thrilling capabilities in terms of ransomware resilience.
To summarize:
- Zerto lets you get well in minutes to simply seconds earlier than an assault, from information and folders to hundreds of VMs creating complicated functions.
- Actual-time, in-line encryption detection helps determine anomalous exercise, restrict blast radius, and supply the earliest warning sign that an assault could also be occurring.
- A full, built-in automation and orchestration suite means there isn’t any want for extra instruments to make sure your large-scale recoveries are as easy and quick as doable.
Do not look forward to an assault to occur! Shield your group and achieve confidence with Zerto. Strive Zerto free for 14 days!