A design flaw within the Fortinet VPN server’s logging mechanism could be leveraged to hide the profitable verification of credentials throughout a brute-force assault with out tipping off defenders of compromised logins.
Though the brute-force assault remains to be seen, a brand new method permits logging solely failed makes an attempt and never profitable ones, producing a false sense of safety.
Verifying VPN credentials
The FortiClient VPN server shops login exercise utilizing a two-step course of that consists of an authentication and an authorization stage.
Researchers at Pentera, an organization offering automated safety validation options, found {that a} profitable login is recorded provided that the method passes each the authentication and the authorization steps; in any other case, FortiClient VPN will log a failed authentication.
“[…] the failed ones are logged in the authentication phase but the successful ones are logged in the authorization phase, so yes, a full login with either a script or a VPN client would create a log,” Pentera safety researcher Peter Viernik advised BleepingComputer.
In a report at present, the cybersecurity firm describes how its researchers devised a technique to cease the total login course of after the authentication stage, permitting them to validateVPN credentials with out logging the success.
The researchers used the Burp software safety testing device to document the interactions between the consumer and the VPN server.
They observed that the response to the preliminary HTTPS request exhibits legitimate credentials (via a “ret=1” worth), a failed authentication (“ret=0”), or “An error occurred” response in case of a number of consecutive failed makes an attempt.
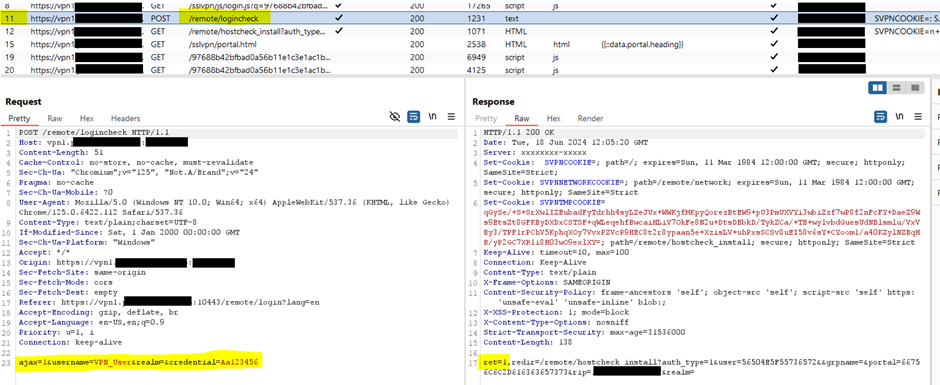
supply: Pentera
In easier phrases, authentication simply confirms that the credentials are legitimate and authorization establishes a VPN session.
Nonetheless, if the method is stopped after the authentication stage, the VPN server solely logs the failed makes an attempt, and never the profitable ones, because it didn’t proceed to the subsequent authorization step.
“The inability to log successful authentication attempts at the authentication phase presents a significant security risk. Attackers could potentially exploit this vulnerability to conduct brute-force attacks without a detection of their successful attempts” – Pentera
The problem generated this manner is that an incident response crew can’t decide if a brute-force try in such an assault was profitable and can solely see logs for failed processes.
The failed authentication makes an attempt will nonetheless tip off an Fortinet admin that their machine is beneath a brute-force assault and permit them to doubtlessly block the makes an attempt.
Nonetheless, they won’t know that the attacker was in a position to efficiently confirm credentials. These credentials can then be offered to different risk actors or used at a later time to breach the community, when the admins are not alert to the malicious exercise.
It’s value noting that even when a risk actor determines an accurate login set and makes use of them in an assault, the authorization course of completes solely after FortiClient VPN sends two API calls that confirm the machine’s safety compliance and the consumer’s entry stage.

supply: Pentera
This verify complicates the assault considerably however a well-resourced attacker may nonetheless use Pentera’s methodology to breach a company’s community.
Pentera says that they shared the analysis with Fortinet and the corporate replied by saying it didn’t think about the difficulty a vulnerability. It’s unclear if Fortinet will tackle the issue, particularly since it’s not an advanced repair.
As a part of at present’s disclosure, Pentera launched a script that exploits this design flaw to confirm Fortinet VPN credentials.
BleepingComputer reached out to Fortinet for a touch upon the difficulty yesterday however a press release was not out there earlier than publishing time.
