An Alabama man was arrested as we speak by the FBI for his suspected position in hacking the SEC’s X account to make a faux announcement that Bitcoin ETFs have been accredited.
The Division of Justice mentioned that 25-year-old Eric Council, of Alabama, and conspirators performed a SIM-swap assault to take over the id of the particular person in control of SEC’s X account.
“The conspirators gained control of the SEC’s X account through an unauthorized Subscriber Identity Module (SIM) swap, allegedly carried out by Council. A SIM swap refers to the process of fraudulently inducing a cell phone carrier to reassign a cell phone number from the legitimate subscriber or user’s SIM card to a SIM card controlled by a criminal actor. As part of the scheme, Council and the co-conspirators allegedly created a fraudulent identification document in the victim’s name, which Council used to impersonate the victim; took over the victim’s cellular telephone account; and accessed the online social media account linked to the victim’s cellular phone number for the purpose of accessing the SEC’s X account and generating the fraudulent post in the name of SEC Chairman Gensler.”
The SEC’s X account was hacked on January ninth, 2024, to tweet that it had lastly accredited Bitcoin ETFs to be listed on inventory exchanges.
“Today the SEC grants approval to Bitcoin ETFs for listing on registered national security exchanges. The approved Bitcoin ETFs will be subject to ongoing surveillance and compliance measures to ensure continued investor protection,” learn the faux publish on X.
This tweet included a picture of SEC Chairperson Gary Gensler, with a quote praising the choice.
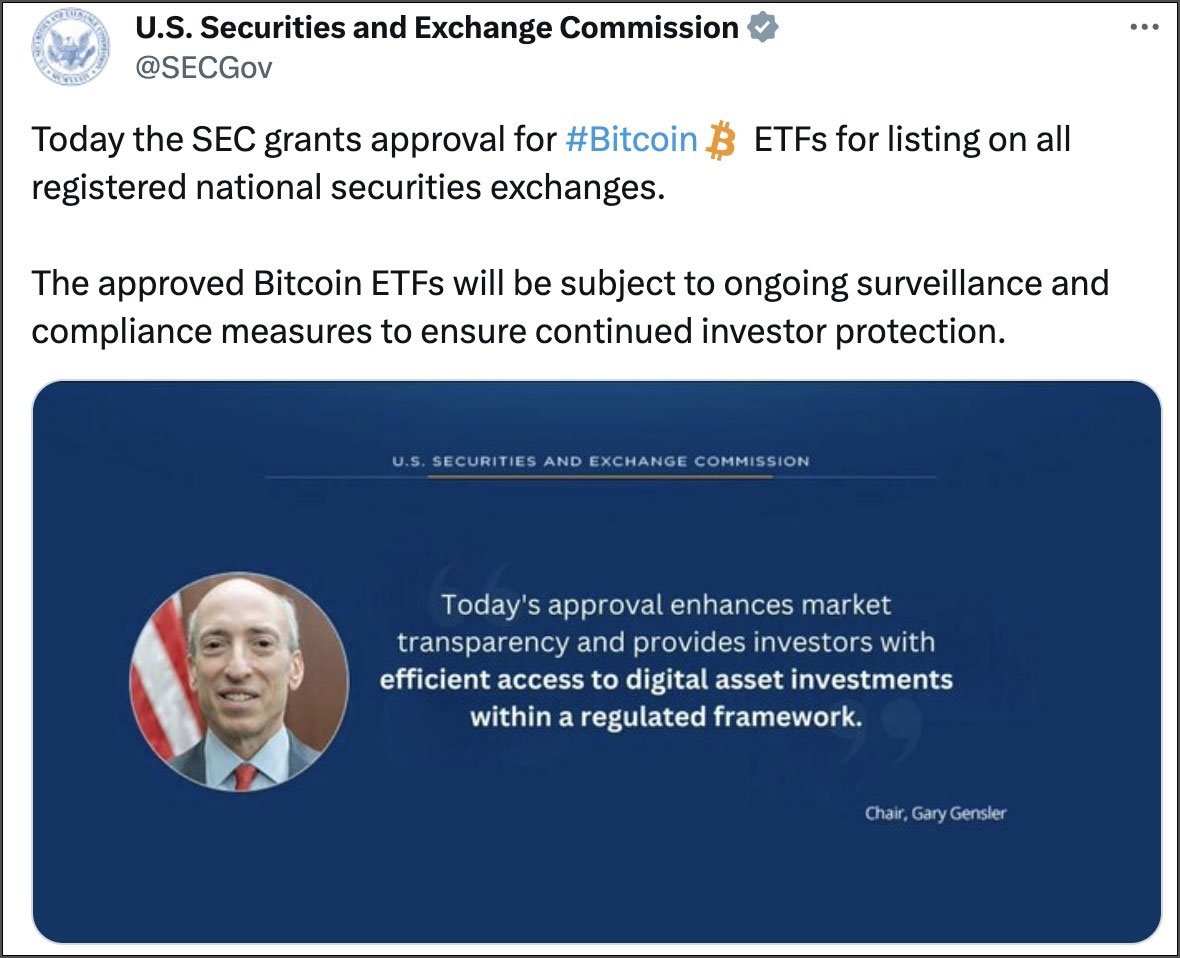
Supply: BleepingComputer
Bitcoin rapidly jumped in worth by $1,000 over the announcement, after which simply as rapidly plummetted by $2,000 after Gensler tweeted that the SEC account had been hacked and the announcement was faux.
The following day, the SEC confirmed the hack was doable by a SIM-swapping assault on the mobile phone quantity related to the particular person in control of the X account.
In SIM swapping assaults, menace actors trick a sufferer’s wi-fi provider into porting a buyer’s cellphone quantity to a distinct cell machine below the attacker’s management. This enables hackers to retrieve all texts and cellphone calls linked to the cellphone quantity, together with password reset hyperlinks and one-time passcodes for multi-factor authentication (MFA).
In keeping with the SEC, the hackers didn’t have entry to the company’s inside techniques, knowledge, units, or different social media accounts, and the SIM swap occurred by tricking their cell provider into porting the quantity.
As soon as the menace actors managed the quantity, they reset the password for the @SECGov X account to create the faux announcement.
Council was indicted on October tenth by a federal grand jury within the District of Columbia for his alleged position within the assault. The suspect is now charged with one rely of conspiracy to commit aggravated id theft and entry machine fraud, which faces a most penalty of 5 years in jail.
Sim swapping assaults have turn into a well-liked instrument for menace actors to take over the cellphone numbers of focused customers, permitting them to obtain one-time passcodes and breach accounts.
These assaults are generally used to steal cryptocurrency from customers whose accounts are usually protected by multi-factor authentication.
Most carriers have launched methods to lock your quantity from being ported to a different provider with out permission, and it’s strongly suggested that every one customers allow these protections if obtainable.
