A brand new ClickFix marketing campaign is luring customers to fraudulent Google Meet convention pages displaying faux connectivity errors that ship info-stealing malware for Home windows and macOS working techniques.
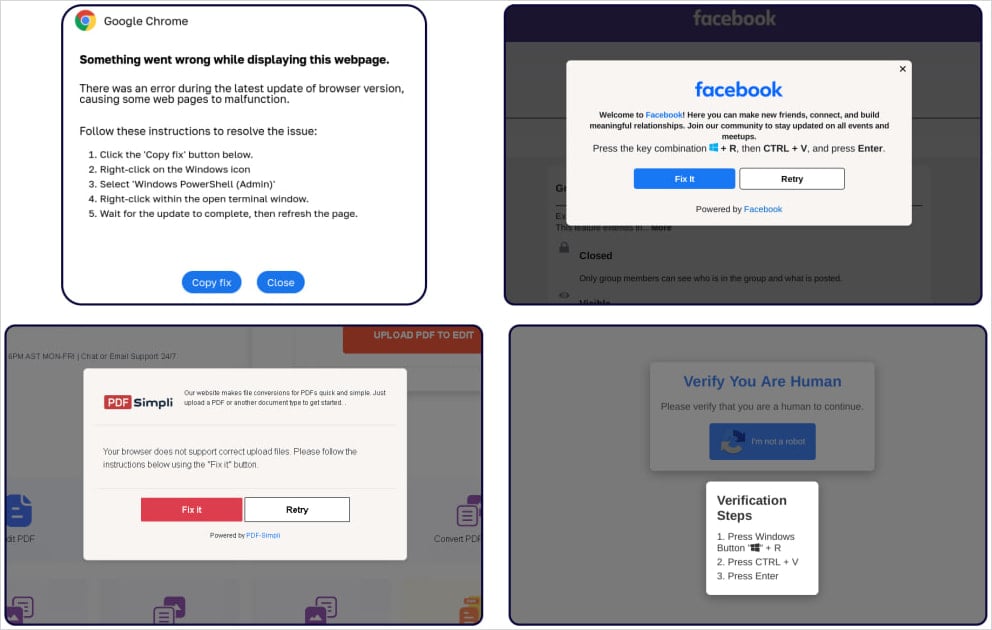
ClickFix is a social-engineering tactic that emerged in Might, first reported by cybersecurity firm Proofpoint, from a risk actor (TA571) that used messages impersonating errors for Google Chrome, Microsoft Phrase, and OneDrive.
The errors prompted the sufferer to repeat to clipboard a bit of PowerShell code that will repair the problems by working it in Home windows Command Immediate.
Victims would thus infect techniques with varied malware comparable to DarkGate, Matanbuchus, NetSupport, Amadey Loader, XMRig, a clipboard hijacker, and Lumma Stealer.
In July, McAfee reported that the ClickFix campaigns had been turning into mode frequent, particularly in the USA and Japan.
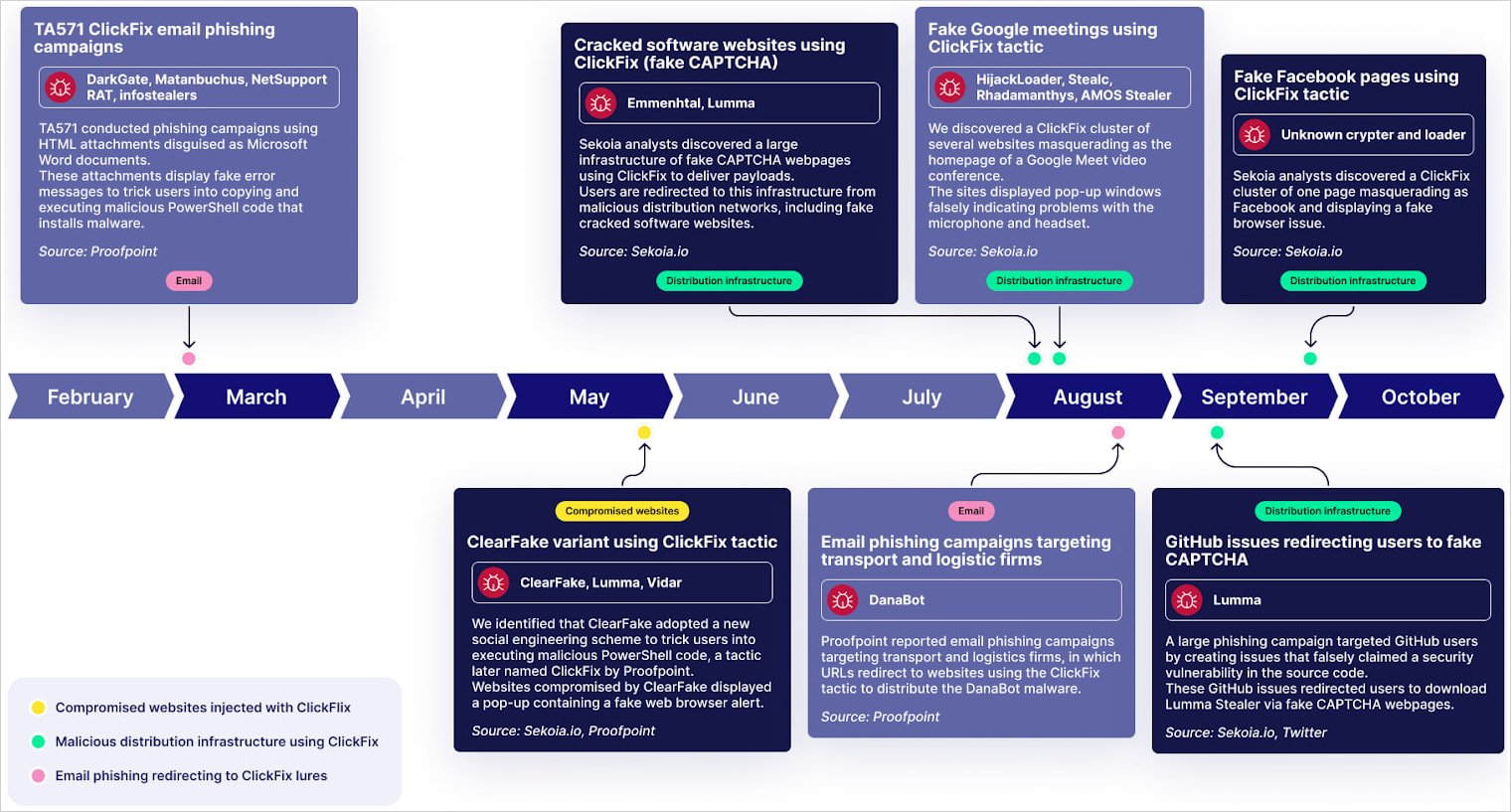
A brand new report from Sekoia, a SaaS cybersecurity supplier, notes that ClickFix campaigns have developed considerably and now use a Google Meet lure, phishing emails focusing on transport and logistics corporations, faux Fb pages, and misleading GitHub points.
Supply: Sekoia
Based on the French cybersecurity firm, a number of the more moderen campaigns are performed by two risk teams, the Slavic Nation Empire (SNE) and Scamquerteo, thought of to be sub-teams of the cryptocurrency rip-off gangs Marko Polo and CryptoLove.
Supply: Sekoia
The Google Meet entice
The risk actors are utilizing faux pages for Google Meet, the video communication service a part of Google Workspace suite, well-liked in company environments for digital conferences, webinars, and on-line collaboration.
An attacker would ship victims emails that seem like official Google Meet invites associated to a piece assembly/convention or another vital occasion.
The URLs intently resemble precise Google Meet hyperlinks:
- meet[.]google[.]us-join[.]com
- meet[.]google[.]web-join[.]com
- meet[.]googie[.]com-join[.]us
- meet[.]google[.]cdm-join[.]us
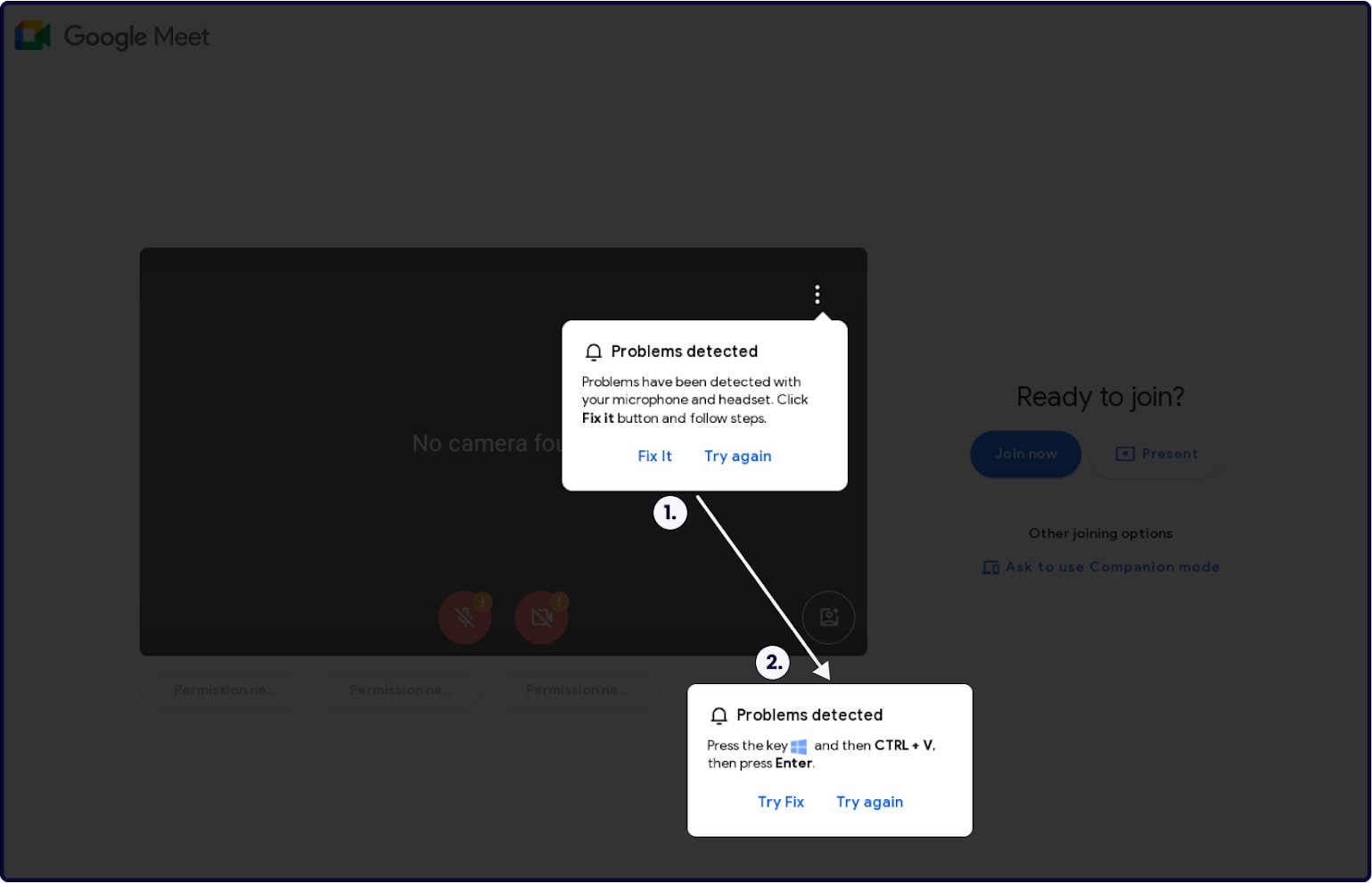
As soon as the sufferer will get on the faux web page, they obtain a pop-up message informing of a technical situation, comparable to a microphone or headset drawback.
Supply: Sekoia
In the event that they click on on “Try Fix,” an ordinary ClickFix an infection course of begins the place PowerShell code copied by the web site and pasted on the Home windows immediate infects their laptop with malware, fetching the payload from the ‘googiedrivers[.]com’ area.
The ultimate payloads are infostealing malware Stealc or Rhadamanthys on Home windows. On a macOS machine, the risk actor drops the AMOS Stealer as a .DMG (Apple disk picture) file named ‘Launcher_v194.’
Sekoia has recognized a number of different malware distribution clusters along with Google Meet, together with Zoom, PDF readers, faux video video games (Lunacy, Calipso, Battleforge, Ragon), web3 browsers and initiatives (NGT Studio), and messenger apps (Nortex).
