Beware of pretend GlobalProtect VPN downloads! A brand new malware marketing campaign makes use of search engine optimisation poisoning and spoofed web sites to ship WikiLoader malware. Primarily focusing on schooling & transportation, it tips customers with pretend installers, resulting in information theft & additional infections.
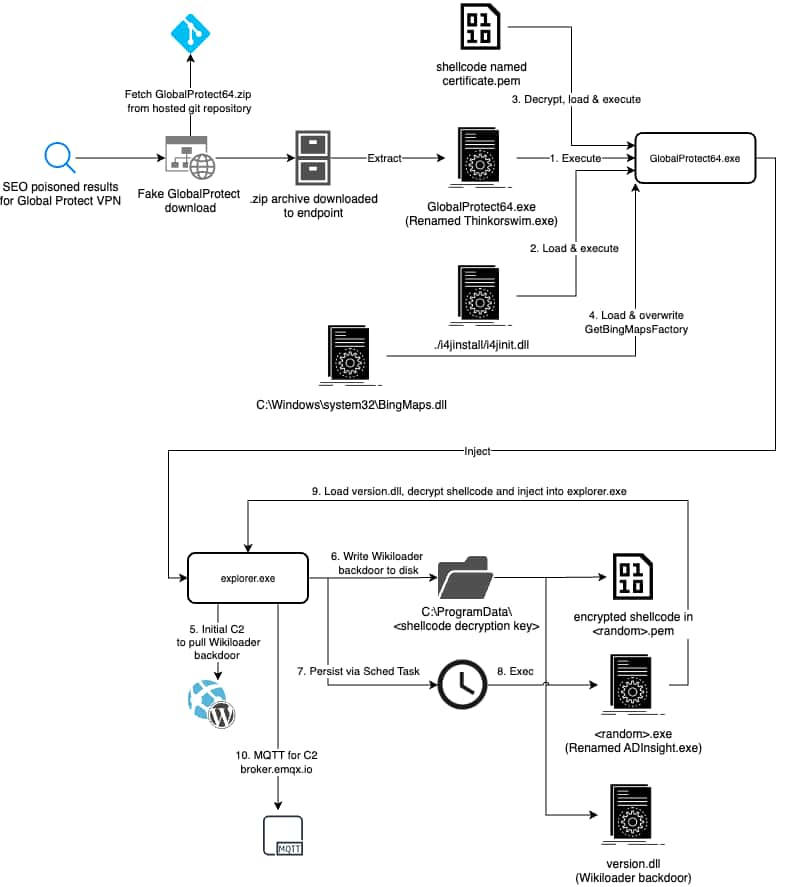
Cybersecurity researchers at Palo Alto Networks have found a brand new malware marketing campaign that leverages Search Engine Optimization (search engine optimisation) poisoning to trick customers into downloading pretend GlobalProtect VPN installers. These pretend installers comprise a harmful malware loader often known as WikiLoader (aka WailingCrab).
WikiLoader is often recognized for being rented out by cybercriminals to assist them ship different malicious applications onto victims’ computer systems. It was initially unfold via phishing emails, however latest studies point out that its distributors have shifted to a way known as search engine optimisation poisoning.
On your info, search engine optimisation poisoning entails manipulating search engine outcomes to make malicious web sites seem excessive in search outcomes. A number of malware households, together with ZenRAT, Zeus Panda, and SpyNote, have beforehand relied on this tactic to contaminate customers by tricking them into visiting malicious websites that seem authentic.
On this case, the attackers have created pretend web sites that mimic Palo Alto Networks’ GlobalProtect VPN software program obtain pages. Unsuspecting customers making an attempt to obtain the VPN software program could as an alternative find yourself downloading WikiLoader.
WikiLoader acts as a “loader” for different malicious payloads, reminiscent of banking Trojans, which might steal delicate info and trigger additional harm.
Based on Palo Alto Networks’ weblog submit, the marketing campaign has primarily focused organizations within the schooling and transportation sectors in america. Nonetheless, the usage of search engine optimisation poisoning implies that anybody trying to find GlobalProtect downloads could possibly be doubtlessly affected.
Other than utilizing use legitimate-looking web sites, researchers warn that the menace actors behind this marketing campaign additionally used varied different methods and instruments to evade detection together with cloud-hosted companies. WikiLoader additionally makes use of tips like exhibiting pretend error messages and hiding malicious recordsdata inside apparently innocent applications to keep away from evaluation.
Palo Alto Networks has carried out measures to guard its prospects from this menace via its suite of safety merchandise, together with Cortex XDR and Superior WildFire. The corporate has additionally shared detailed details about this marketing campaign, together with indicators of compromise and detection guidelines. Organizations and people ought to evaluation this info and take steps to guard themselves from this menace.
RELATED TOPICS
- Hackers Goal Test Level VPNs, Safety Repair Launched
- Ivanti VPN Flaws Exploited by DSLog Backdoor and Crypto Miners
- Hackers Calling Workers to Steal VPN Credentials from US Companies
- Cisco Fixes Excessive-Severity Code Execution and VPN Hijacking Flaws
- BlackByte Ransomware Exploits VMware Flaw in VPN-Primarily based Assaults