A brand new info-stealing malware linked to Redline poses as a recreation cheat known as ‘Cheat Lab,’ promising downloaders a free copy in the event that they persuade their associates to put in it too.
Redline is a highly effective information-stealing malware able to harvesting delicate info from contaminated computer systems, together with passwords, cookies, autofill info, and cryptocurrency pockets info.
The malware is extremely popular amongst cybercriminals and is unfold worldwide utilizing various distribution channels.
(McAfee)
McAfee risk researchers reported that the brand new info stealer leverages Lua bytecode to evade detection, permitting the malware to inject into reputable processes for stealth and in addition reap the benefits of Simply-In-Time (JIT) compilation efficiency.
The researchers hyperlink this variant to Redline because it makes use of a command and management server beforehand related to the malware.
Nonetheless, in response to BleepingComputer’s checks, the malware doesn’t exhibit conduct sometimes related to Redline, similar to stealing browser info, saving passwords, and cookies.
Desires you to contaminate your pals too!
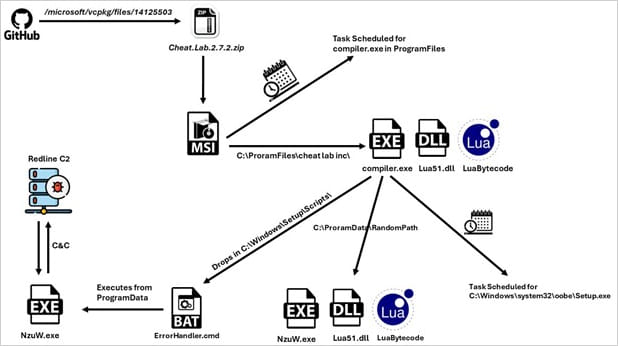
The malicious Redline payloads impersonate demos of dishonest instruments known as “Cheat Lab” and “Cheater Pro” via URLs linked to Microsoft’s ‘vcpkg’ GitHub repository.
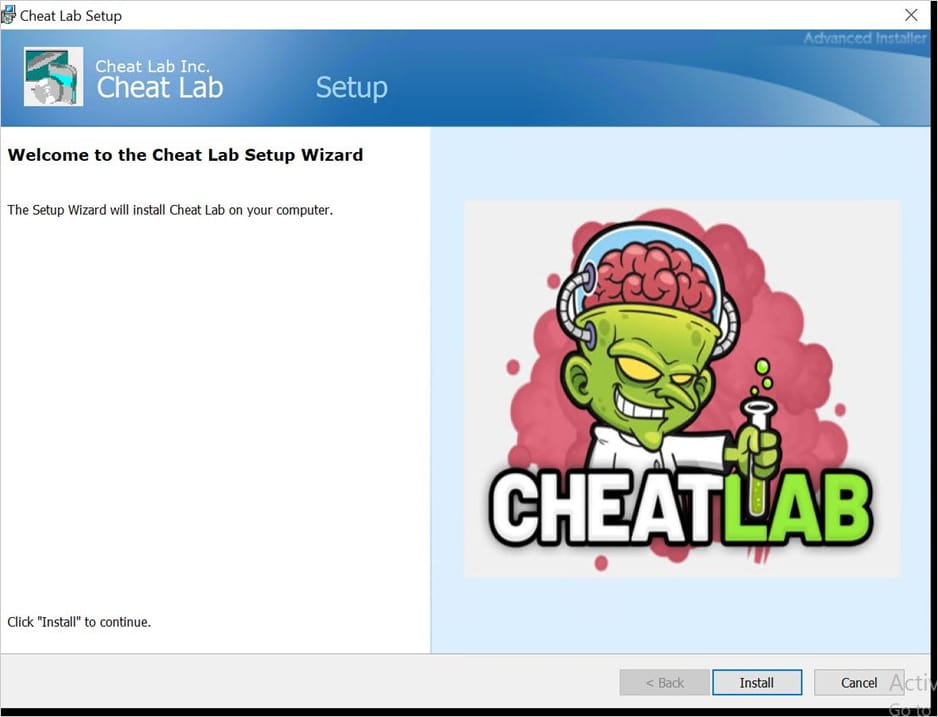
The malware is distributed as ZIP information containing an MSI installer that unpacks two information, compiler.exe and lua51.dll, when launched. It additionally drops a ‘readme.txt’ file containing the malicious Lua bytecode.
Supply:McAfee
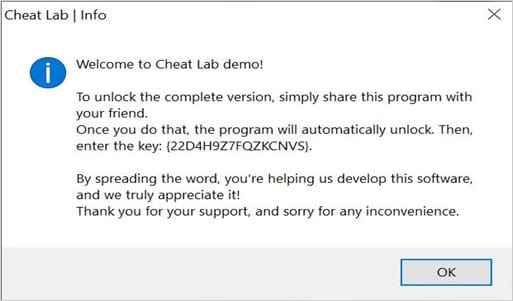
This marketing campaign makes use of an fascinating lure to additional distribute the malware by telling victims they’ll get a free, absolutely licensed copy of the dishonest program in the event that they persuade their associates to put in it, too.
The message additionally accommodates an activation key for added legitimacy.
“To unlock the complete version, simply share this program with your friend. Once you do that, the program will automatically unlock,” reads the set up immediate proven under.
Supply:McAfee
To evade detection, the malware payload just isn’t distributed as an executable however relatively as uncompiled bytecode.
When put in, the compiler.exe program compiles the Lua bytecode saved within the readme.txt file and executes it. The identical executable additionally units up persistence by creating scheduled duties that execute throughout system startup.
McAfee stories that the malware makes use of a fallback mechanism for persistence, copying the three information to a protracted random path underneath program information.
Supply:McAfee
As soon as energetic on the contaminated system, the malware communicates with a C2 server, sending screenshots of the energetic home windows and system info and ready for instructions to execute on the host.
The precise technique used for preliminary an infection hasn’t been decided, however information-stealers are sometimes unfold through malvertising, YouTube video descriptions, P2P downloads, and misleading software program obtain websites.
Customers are suggested to keep away from unsigned executables and information downloaded from shady web sites.
This assault reveals that even putting in packages from seemingly reliable areas like Microsoft’s GitHub can set individuals up for a Redline an infection.
BleepingComputer contacted Microsoft in regards to the executables distributed via its GitHub URLs however didn’t obtain a response by the point of publication.
