Faux AI picture and video mills infect Home windows and macOS with the Lumma Stealer and AMOS information-stealing malware, used to steal credentials and cryptocurrency wallets from contaminated units.
Lumma Stealer is a Home windows malware and AMOS is for macOS, however each steal cryptocurrency wallets and cookies, credentials, passwords, bank cards, and searching historical past from Google Chrome, Microsoft Edge, Mozilla Firefox, and different Chromium browsers.
This information is collected into an archive and despatched again to the attacker, the place they’ll use the knowledge in additional assaults or promote it on cybercrime marketplaces.
Faux AI picture mills push Lumma Stealer
Over the previous month, risk actors have created pretend web sites that impersonate an AI video and picture editor referred to as EditPro.
As found by cybersecurity researcher g0njxa, the websites are promoted by means of search outcomes and commercials on X that share deepfake political movies, comparable to President Biden and Trump having fun with ice cream collectively.
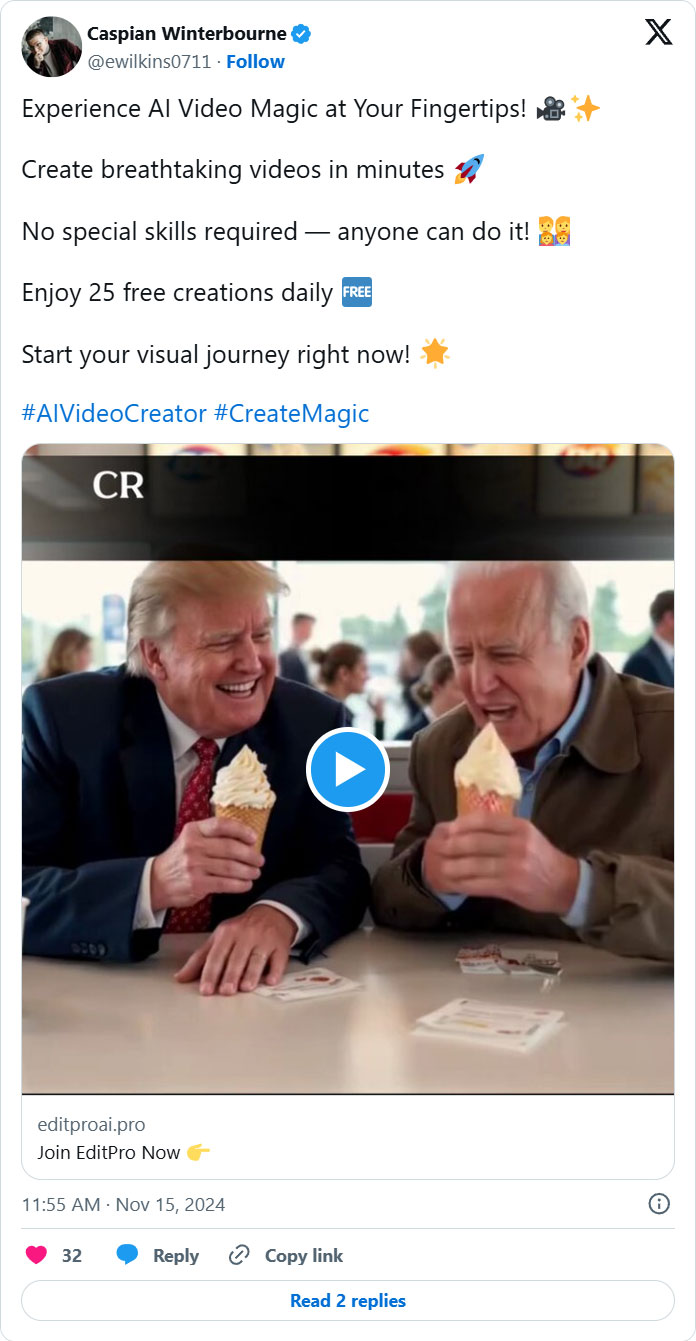
Supply: BleepingComputer.com
Clicking the pictures brings you to pretend web sites for the EditProAI utility, with editproai[.]professional created to push Home windows malware and editproai[.]org to push macOS malware.
The websites are professional-looking and even include the ever present cookie banner, making them feel and appear professional.
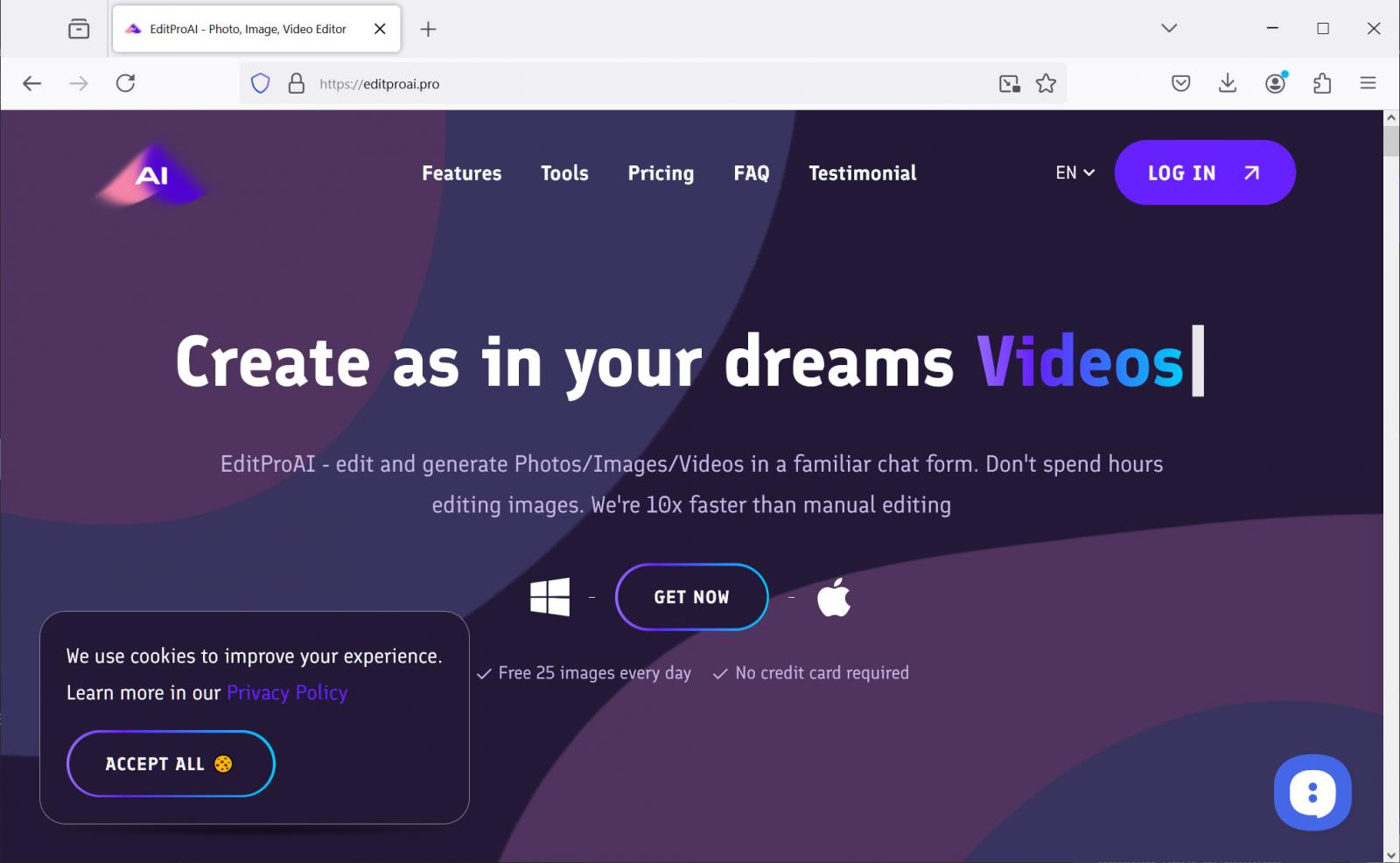
Supply: BleepingComputer
Nonetheless, clicking the “Get Now” hyperlinks will obtain an executable pretending to be the EditProAI utility. For Home windows customers, the file is known as “Edit-ProAI-Setup-newest_release.exe” [VirusTotal] and for macOS, it’s named “EditProAi_v.4.36.dmg” [VirusTotal].
The Home windows malware is signed by what seems to be a stolen code signing certificates from Softwareok.com, a freeware utility developer.
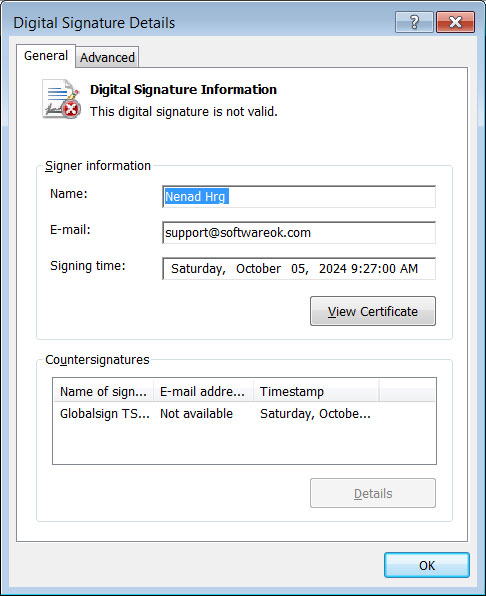
Supply: BleepingComputer
G0njxa says that malware makes use of a panel at “proai[.]club/panelgood/” to ship stolen information, which may then be retrieved at a later time by the risk actors.
An AnyRun report reveals the execution of the Home windows variant, with the sandbox service detecting the malware as Lumma Stealer.
When you’ve got downloaded this program previously, you must take into account all your saved passwords, cryptocurrency wallets, and authentications compromised and instantly reset them with distinctive passwords at each web site you go to.
You also needs to allow multi-factor authentication in any respect delicate websites, comparable to cryptocurrency exchanges, on-line banking, e mail providers, and monetary providers.
Info-stealing malware has seen large progress over the previous few years, with risk actors conducting large international operations to steal folks’s credentials and authentication tokens.
Different campaigns not too long ago pushing infostealers embody using zero-day vulnerabilities, pretend fixes to GitHub points, and even pretend solutions on StackOverflow.
The stolen credentials are then used to breach company networks, conduct information theft campaigns like we noticed with the large SnowFlake account breaches, and trigger chaos by corrupting community routing data.
