Intro
The variety of the open-source packages is consistently rising, complicating how builders select a package deal that matches their wants and is safe. Bundle repositories supply varied metrics to assist builders select the correct package deal, just like the variety of downloads, GitHub statistics, and consumer scores. Bundle repositories supply varied metrics to assist builders select the correct package deal, just like the variety of downloads, GitHub statistics, and consumer scores. Nonetheless, reputation continues to be probably the most influential elements in package deal choice. After we see a preferred package deal, we assume it’s well-maintained and dependable. This widespread assumption led to the emergence of starjacking two years in the past.
Starjacking is a method that artificially inflates a package deal’s obvious reputation by exploiting how package deal repositories show details about related GitHub repositories. After the method grew to become public, a number of main repositories, together with npm and Yarn, have been discovered to permit package deal publications with hyperlinks to GitHub repositories not owned by the package deal writer. We just lately performed complete analysis throughout greater than 20 package deal repositories to judge the present state of starjacking, and the findings present promising developments in safety measures.
Researched package deal repositories
Our analysis encompassed 21 separate package deal repositories, Starting from the massive ones like npm, maven, and PyPI to smaller ones like CPAN, LuaRocks, and Hackage. The desk under lists every repository and its major programming language, included within the analysis.
| Repo Title | Language |
| npm | JS |
| Maven Central | java |
| Pypi | python |
| NuGet | csharp |
| pkg.go.dev | go |
| Packagist | PHP |
| Rubygems | Ruby |
| crates.io | Rust |
| CocoaPods | ObjC/Swift |
| Pub.dev | dart |
| CPAN | perl |
| CRAN | R |
| Clojars | JS |
| Yarn | JS |
| anaconda | python, r |
| LuaRocks | lua |
| Hackage | haskell |
| Opam | ocaml |
| Hex | erlang |
| Meteor | JS |
| Swift package deal index | Swift |
- Some retailer the artifacts created throughout constructing, compiling, or packaging the code.
- Others merely present references to GitHub repositories containing the required information for package deal set up.
Bundle managers that completely reference GitHub repositories, comparable to pkg.go.dev and RubyGems, are inherently protected in opposition to starjacking since they show knowledge straight from GitHub repositories. This direct integration eliminates the opportunity of linking to 1 repository whereas serving code from one other.
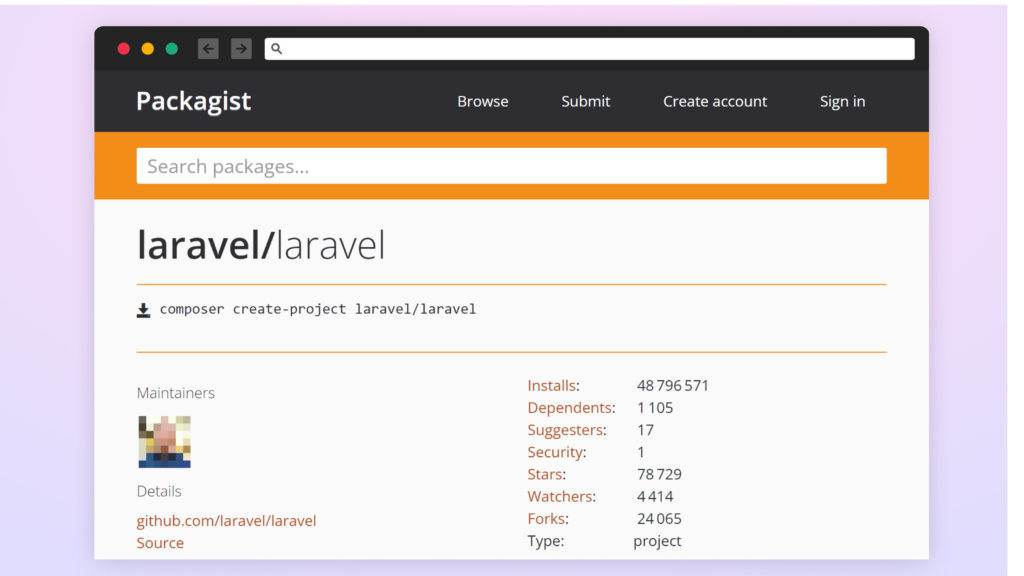
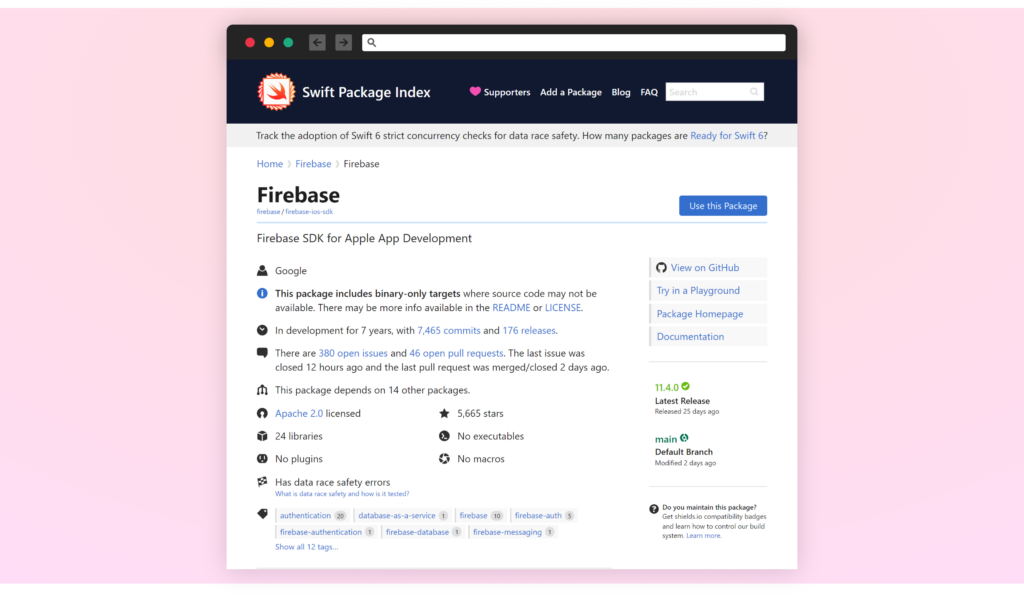
Whereas such package deal repositories should not prone to Starjacking, the displayed GitHub statistics can nonetheless be deceptive. They are often manipulated utilizing extra refined methods. For instance, Swift Bundle Index and Packagist show complete GitHub repository particulars, which may trick the customers, if the stats are spoofed.
Outcomes
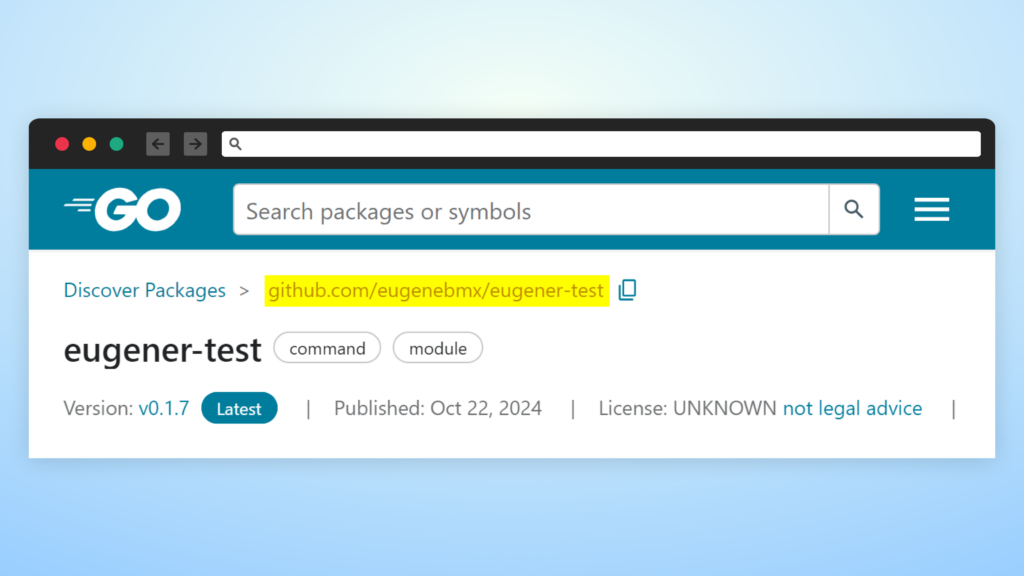
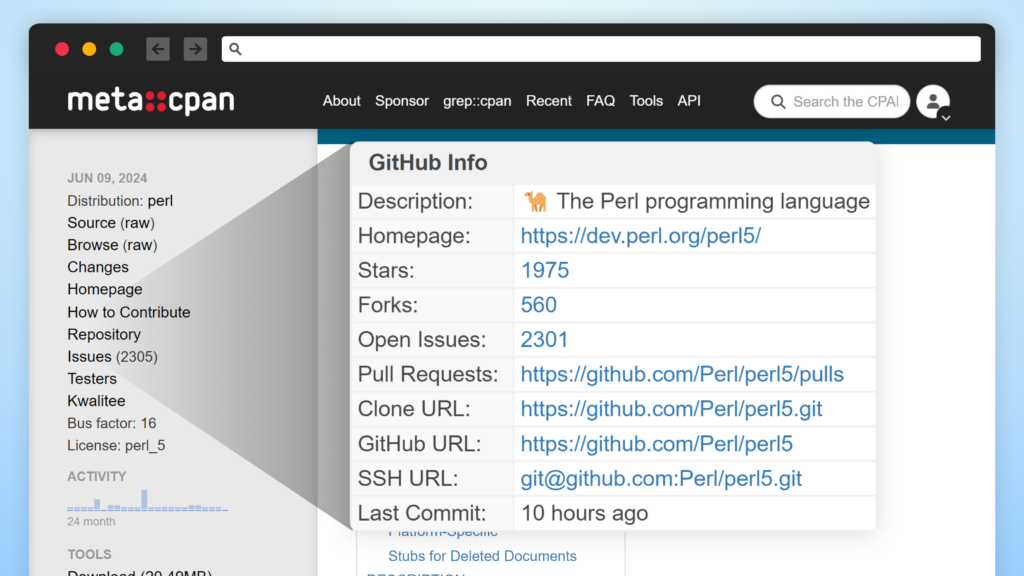
Most repositories don’t show the GitHub repository statistics referred to by the package deal. Whereas PyPI and Yarn beforehand confirmed these stats, they’ve since modified their approaches: Yarn has fully eliminated the statistics whereas PyPI carried out a extra refined metadata show system. But some package deal repos nonetheless show GitHub statistics; for instance, npm continues to indicate the variety of points and pull requests from the GitHub repository specified within the package deal metadata.
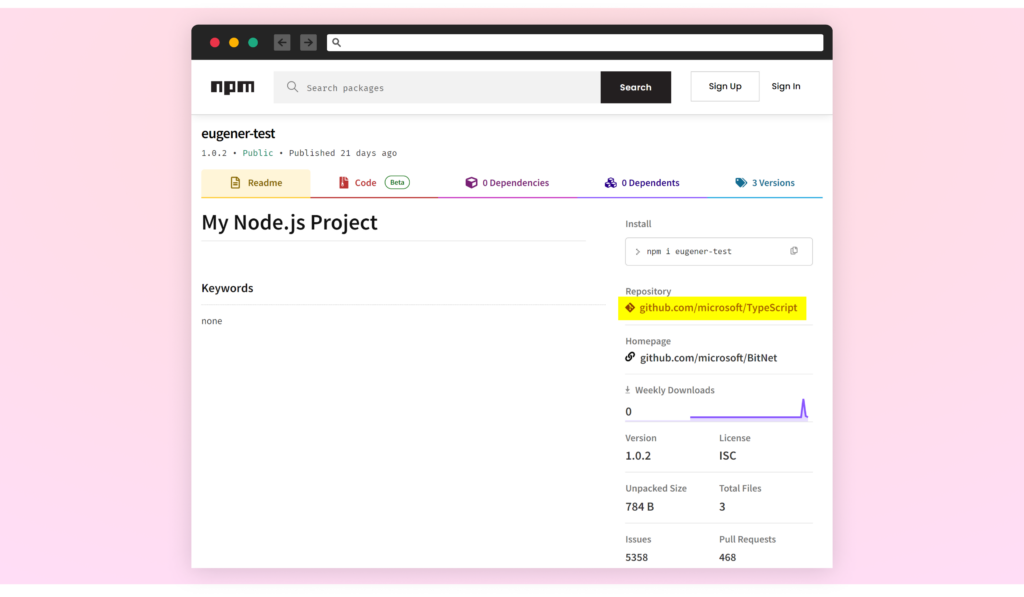
Furthermore, the CPAN Perl package deal repository shows the GitHub stats.
Pypi’s Transformation of GitHub Statistics Show
PyPI slowly however steadily added verification of the package deal metadata.
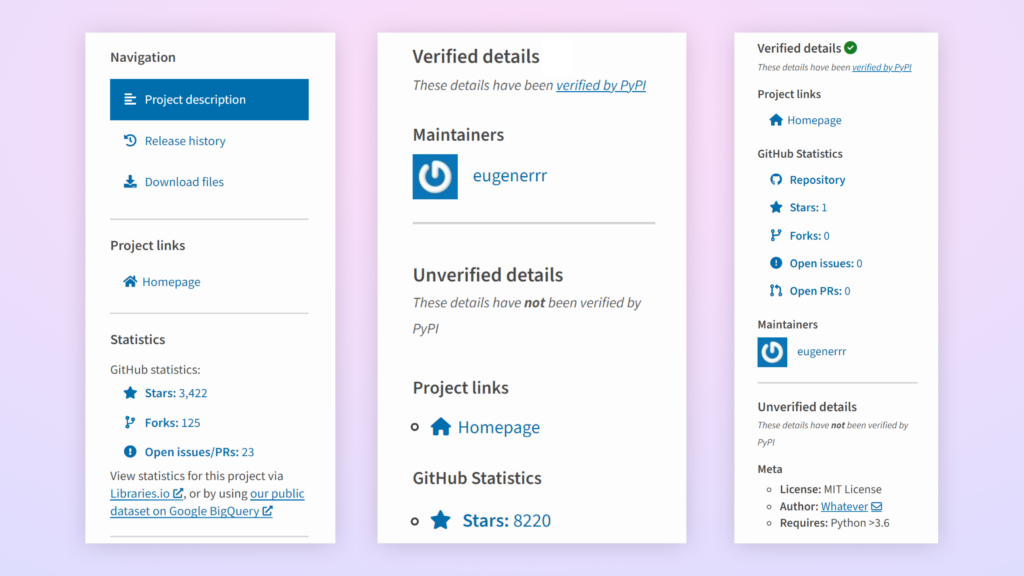
Initially, PyPI displayed GitHub repository statistics with none verification mechanism. This method made the platform weak to starjacking makes an attempt, as any package deal may declare affiliation with any GitHub repository. PyPI’s first safety enchancment divided package deal data into two distinct sections: unverified and verified particulars.
Whereas this division helped customers establish trusted data, statistics of arbitrary GitHub repositories have been nonetheless proven within the unverified particulars part. This was a superb step in the direction of informing the consumer which knowledge they will belief. Nonetheless, this was not sufficient since most individuals don’t fastidiously distinguish between verified and unverified data.
PyPI made an important development by implementing a complete verification system by means of the Trusted Writer Administration function. Ranging from August 2024, the platform now ensures GitHub statistics seem completely within the verified particulars part and are solely displayed for packages uploaded by means of the Trusted Writer Administration function. This method makes use of OpenID Hook up with allow safe publishing by means of trusted companies like GitHub Actions.
The brand new publishing course of works as follows: A PyPI challenge maintainer specifies a workflow of their GitHub repository for automated package deal publishing. When triggered, the workflow authenticates with PyPI, proving that the code comes from the meant supply. Solely after verification can the package deal be revealed. Underneath this new system, PyPI shows GitHub repository statistics solely when the hyperlinks level to verified code repositories which have been authenticated by means of the trusted publishing workflow.
The evolution of PyPI’s safety measures in opposition to Starjacking could be seen in three distinct phases (left to proper):
- Preliminary section: GitHub statistics have been displayed with none verification or indication of their authenticity.
2. Second section: Separation of verified and unverified particulars, with GitHub statistics particularly positioned
within the unverified particulars part.
3. Present section: GitHub statistics at the moment are solely displayed within the verified particulars part and seem
completely for packages uploaded by means of the Trusted Writer Administration function.
This development demonstrates PyPI’s dedication to sustaining safety whereas offering invaluable repository data to customers.
Conclusion
Whereas npm and CPAN proceed to show unverified GitHub statistics, the chance of Starjacking has considerably decreased over the previous two years. This enchancment stems from most repositories both eradicating GitHub statistics totally or implementing extra strong verification programs, as exemplified by PyPI. It’s price noting that the majority repositories (with PyPI being the exception) nonetheless show package deal metadata hyperlinks with out verification. Whereas this vulnerability may doubtlessly be exploited by malicious actors, it poses a considerably decrease danger of deceptive customers in comparison with the unique Starjacking method.