A proof-of-concept (PoC) exploit for a Veeam Backup Enterprise Supervisor authentication bypass flaw tracked as CVE-2024-29849 is now publicly accessible, making it pressing that admins apply the newest safety updates.
Veeam Backup Enterprise Supervisor (VBEM) is a web-based platform for managing Veeam Backup & Replication installations by way of an internet console. It helps management backup jobs and carry out restoration operations throughout a corporation’s backup infrastructure and large-scale deployments.
Veeam issued a safety bulletin in regards to the vital flaw on Might 21, warning a few vital vulnerability enabling distant unauthenticated attackers to log in to VBEM’s net interface as any consumer.
The seller urged its clients to deal with the issue by upgrading to VBEM model 12.1.2.172, whereas additionally sharing mitigation suggestions for these unable to use the replace instantly.
Exploit particulars
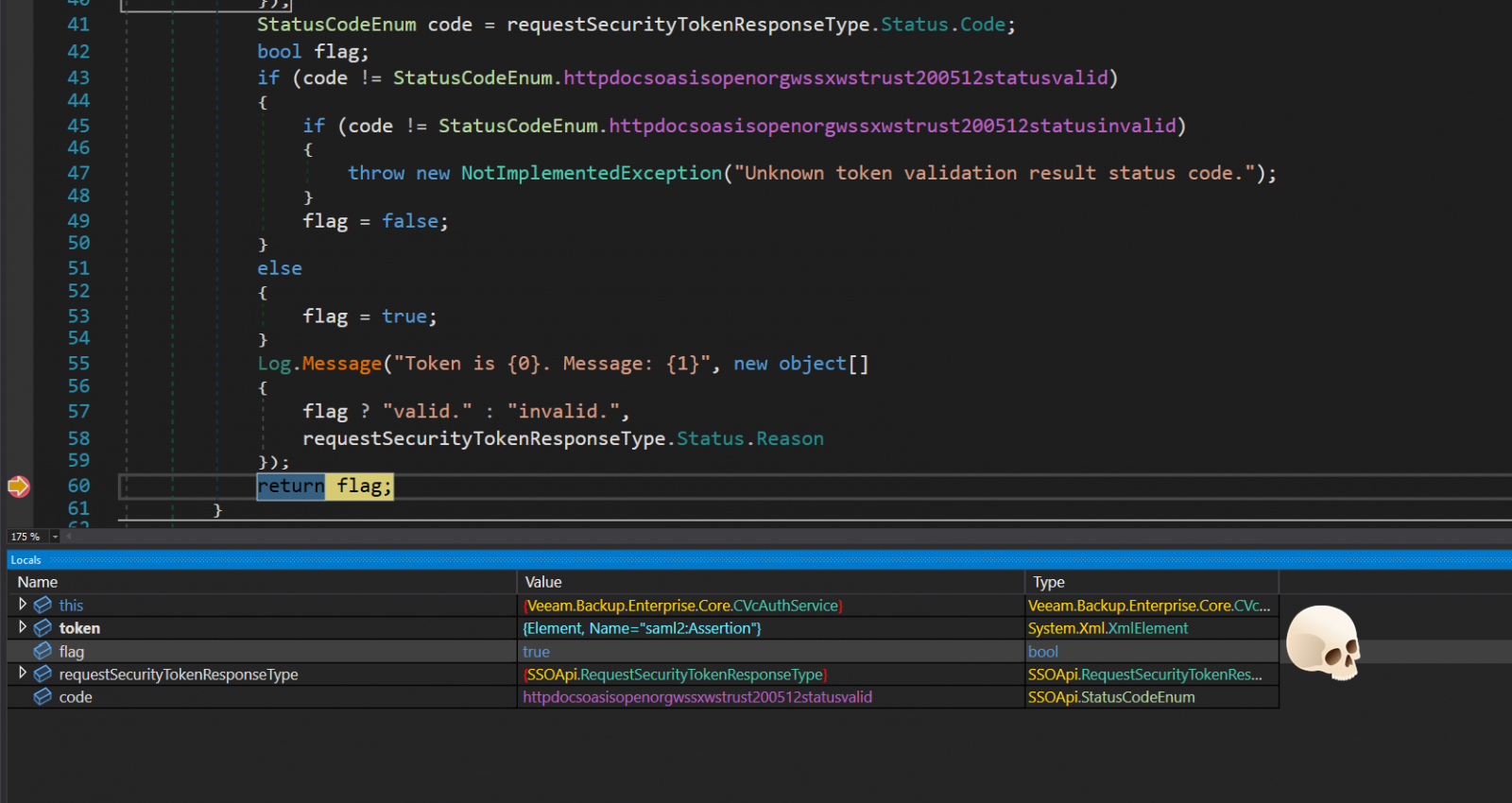
In a technical writeup by Sina Kheirkha, the cybersecurity researcher explains that the flaw lies within the ‘Veeam.Backup.Enterprise.RestAPIService.exe’ service, which listens on TCP port 9398, functioning as a REST API server for the primary net utility.
The exploit entails sending a specifically crafted VMware single-sign-on (SSO) token to the susceptible service utilizing the Veeam API.
The token comprises an authentication request that impersonates an administrator consumer and an SSO service URL that Veeam, crucially, does not confirm.
The base64-encoded SSO token is decoded and interpreted in XML type to confirm its validity by way of a SOAP request to an attacker-controlled URL.
This rogue server arrange by the attacker responds positively to validation requests, so Veeam accepts the authentication request and offers administrator entry to the attacker.
Supply: summoning.workforce
The offered exploit demonstrates all of the steps to take advantage of the vulnerability, together with establishing a callback server, sending the crafted token, and retrieving a listing of file servers as proof of profitable exploitation.
Addressing the dangers
Though no in-the-wild exploitation of CVE-2024-29849 has been reported but, the general public availability of a working exploit might change this in a short while. Subsequently, updating to model 12.1.2.172 or later as quickly as attainable is vital.
These unable to patch ought to comply with these suggestions:
- Restrict entry to the VBEM net interface by proscribing community entry to solely trusted IP addresses.
- Implement firewall guidelines to dam unauthorized entry to the ports utilized by Veeam companies (e.g., port 9398 for the REST API).
- Allow multi-factor authentication for all accounts accessing VBEM.
- Deploy a Internet Software Firewall to assist detect and block malicious requests concentrating on VBEM.
- Repeatedly monitor and audit entry logs for any suspicious or unauthorized entry makes an attempt, and arrange alerts for login makes an attempt from untrusted IP addresses.
- Isolate the VBEM server from different vital techniques inside your community to include lateral motion threat.
