A proof-of-concept (PoC) exploit for CVE-2024-29847, a important distant code execution (RCE) vulnerability in Ivanti Endpoint Supervisor, is now publicly launched, making it essential to replace units.
The flaw is a deserialization of untrusted information problem impacting Ivanti Endpoint Supervisor earlier than 2022 SU6 and EPM 2024, which was mounted as a part of the September 2024 replace on September 10, 2024.
The vulnerability was found by safety researcher Sina Kheirkhah (@SinSinology), who reported it by way of the Zero Day Initiative (ZDI) on Might 1, 2024.
The identical researcher has now revealed the total particulars on how CVE-2024-29847 may be exploited, which can seemingly gas assaults within the wild.
The CVE-2024-29847 flaw
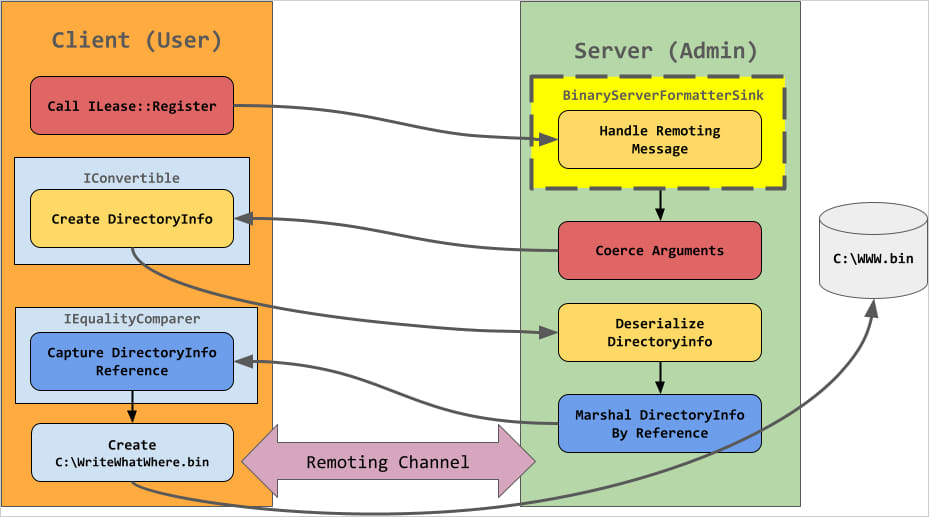
The basis reason behind the flaw lies within the insecure deserialization throughout the AgentPortal.exe executable, particularly, the OnStart methodology of the service, which makes use of the deprecated Microsoft .NET Remoting framework to facilitate communication between distant objects.
The service registers a TCP channel with dynamically assigned ports and no safety enforcement, making it potential for a distant attacker to inject malicious objects.
Kheirkhah’s assault circulate entails crafting a Hashtable containing serialized objects to ship to the weak endpoint, which, upon deserialization, executes arbitrary operations by calling strategies on the DirectoryInfo or FileInfo objects.
These allow the attacker to carry out file operations comparable to studying or writing recordsdata on the server, together with internet shells that may execute arbitrary code.
It’s famous within the write-up {that a} low-type filter restricts which objects may be deserialized. Nonetheless, utilizing a method described by James Forshaw, it is potential to bypass the safety mechanism.
Supply: summoning.staff
Patch now!
Ivanti has made a safety ‘sizzling patch’ out there for EPM 2022 and 2024, with SU6 and September 2024 updates, respectively.
The seller affords no different mitigations or workarounds, so making use of the safety replace within the bulletin is the one advice.
In January, CISA warned {that a} important authentication bypass vulnerability in Ivanti’s Endpoint Supervisor Cellular product was actively exploited in assaults.
Final week, Ivanti confirmed that hackers are actively exploiting a high-severity distant code execution flaw, tracked as CVE-2024-8190, in its Cloud Providers Equipment (CSA).
CISA additionally added the flaw to its Recognized Exploited Vulnerabilities catalog, setting the deadline to safe weak home equipment to October 4, 2024.
