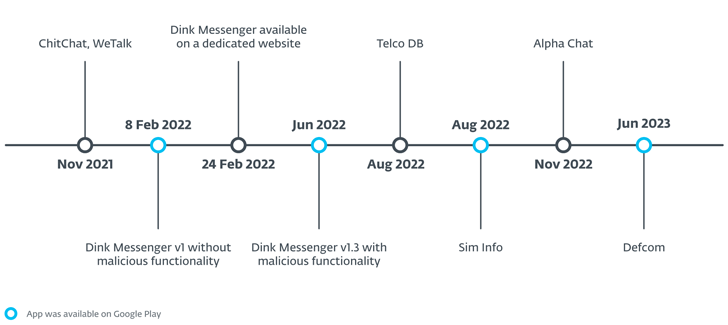
An lively Android malware marketing campaign dubbed eXotic Go to has been primarily focusing on customers in South Asia, notably these in India and Pakistan, with malware distributed through devoted web sites and Google Play Retailer.
Slovak cybersecurity agency stated the exercise, ongoing since November 2021, isn’t linked to any identified menace actor or group. It is monitoring the group behind the operation below the title Digital Invaders.
“Downloaded apps provide legitimate functionality, but also include code from the open-source Android XploitSPY RAT,” ESET safety researcher Lukáš Štefanko stated in a technical report launched at present.
The marketing campaign is claimed to be extremely focused in nature, with the apps out there on Google Play having negligible variety of installs starting from zero to 45. The apps have since been taken down.
The fake-but-functional apps primarily masquerade as messaging providers like Alpha Chat, ChitChat, Defcom, Dink Messenger, Sign Lite, TalkU, WeTalk, Wicker Messenger, and Zaangi Chat. Roughly 380 victims are stated to have downloaded the apps and created accounts to make use of them for messaging functions.
Additionally employed as a part of eXotic Go to are apps reminiscent of Sim Information and Telco DB, each of which declare to supply particulars about SIM house owners just by getting into a Pakistan-based telephone quantity. Different functions cross off as a meals ordering service in Pakistan in addition to a respectable Indian hospital referred to as Specialist Hospital (now rebranded as Trilife Hospital).
XploitSPY, uploaded to GitHub as early as April 2020 by a consumer named RaoMK, is related to an Indian cyber safety options firm referred to as XploitWizer. It has additionally been described as a fork of one other open-source Android trojan referred to as L3MON, which, in flip, attracts inspiration from AhMyth.
It comes with a large gamut of options that enables it to assemble delicate knowledge from contaminated gadgets, reminiscent of GPS places, microphone recordings, contacts, SMS messages, name logs, and clipboard content material; extract notification particulars from apps like WhatsApp, Fb, Instagram, and Gmail; obtain and add recordsdata; view put in apps; and queue instructions.
On prime of that, the malicious apps are designed to take photos and enumerate recordsdata in a number of directories associated to screenshots, WhatApp, WhatsApp Enterprise, Telegram, and an unofficial WhatsApp mod often known as GBWhatsApp.
“Throughout the years, these threat actors have customized their malicious code by adding obfuscation, emulator detection, hiding of [command-and-control] addresses, and use of a native library,” Štefanko stated.
The primary objective of the native library (“defcome-lib.so”) is to maintain the C2 server data encoded and hidden from static evaluation instruments. If an emulator is detected, the app makes use of a pretend C2 server to evade detection.
A number of the apps have been propagated by web sites particularly created for this objective (“chitchat.ngrok[.]io”) that present a hyperlink to an Android bundle file (“ChitChat.apk”) hosted on GitHub. It is presently not clear how victims are directed to those apps.
“Distribution started on dedicated websites and then even moved to the official Google Play store,” Štefanko concluded. “The purpose of the campaign is espionage and probably is targeting victims in Pakistan and India.”