Ariane Techniques self check-in techniques put in at 1000’s of inns worldwide are weak to a kiosk mode bypass flaw that would permit entry to friends’ private data and the keys for different rooms.
These terminals permit folks to ebook and test into the lodge themselves, deal with the cost course of through a POS subsystem, print invoices, and provision RFID transponders used as room keys.
Again in March, Pentagrid safety researcher Martin Schobert found that he may simply bypass the Ariane Allegro Situation Participant working in kiosk mode on the self check-in terminal on the lodge he was staying, and entry the underlying Home windows desktop with all buyer particulars.
Regardless of a number of makes an attempt to alert the seller, the researcher has but to obtain a correct response from the seller in regards to the firmware model that addresses the problem.
Single quote escape
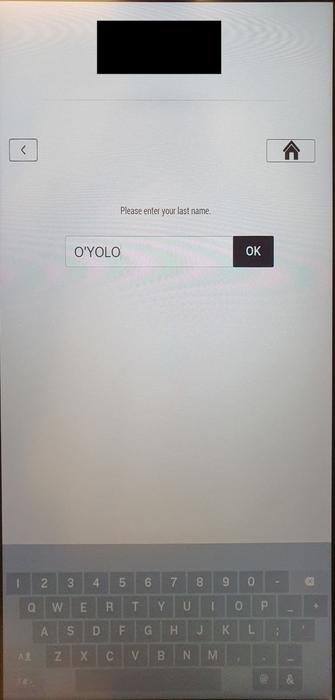
Schobert found that the appliance hangs when getting into a single quote on the reservations look-up display of the terminal.
When touching the display once more, the underlying Home windows working system presents the person the choice to finish the app’s course of, which terminates the Ariane Allegro Situation Participant and offers entry to the desktop.
From there, the person might entry any information saved on the system, which may embody something from reservation entries with personally identifiable data (PII) to invoices.
Supply: Pentagrid
“With access to the Windows desktop, attacks on the hotel network could become possible as well as access to data stored on the terminal, which includes PII, reservations, and invoices,” explains the Pentagrid report.
“With the ability to inject and execute program code, it seems possible to get room keys created for other rooms because the functionality of provisioning RFID transponders is implemented in the terminal.”
Influence and fixing
The weak terminals are sometimes utilized in small to medium-sized institutions the place emplying check-in workers 24/7 could be to expensive for the enterprise.
In accordance with Ariane Techniques, its self-checkout options are presently utilized by 3,000 inns in 25 nations, which collectively have over 500,000 rooms. Amongst their shoppers are one-third of the world’s high 100 lodge chains.
Schobert tried a number of instances to speak his findings to Ariane since discovering the problem in early March however he solely acquired a brief response claiming that the problems had been fastened.
At the moment, it’s unknown which model of the appliance fixes the issue, what number of terminals are utilizing a weak model, and which lodge chains are impacted.
BleepingComputer has contacted Ariane Techniques with questions in regards to the remediation effort however a press release wasn’t instantly obtainable.
Lodge operators utilizing Ariane Techniques terminals are advisable to isolate the self check-in machines from the lodge community and different crucial techniques and make contact with the seller to find out if they’re working a safe model.
In April, Schobert found an analogous situation at a self check-in terminal utilized by a German Ibis lodge. He discovered that an enter of six consecutive dashes for the reserving reference quantity would trigger the terminal to return reserving particulars comparable to worth, room quantity, and legitimate entry keycodes.
