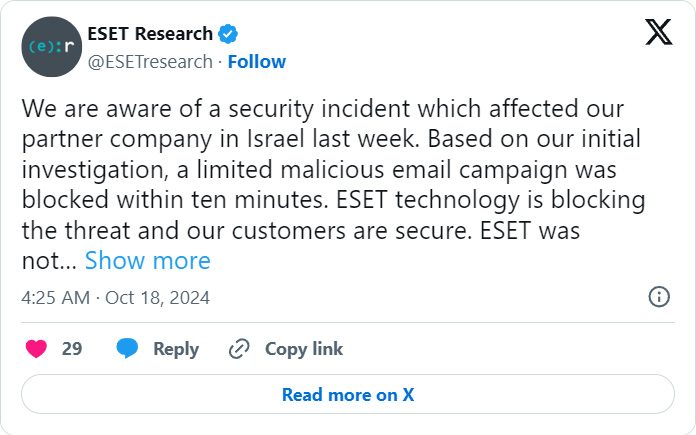
Hackers breached ESET’s unique companion in Israel to ship phishing emails to Israeli companies that pushed knowledge wipers disguised as antivirus software program for damaging assaults.
A knowledge wiper is malware that deliberately deletes all the recordsdata on a pc and generally removes or corrupts the partition desk to make it more durable to get well the info.
In a phishing marketing campaign that began on October eighth, emails branded with ESET’s brand have been despatched from the respectable eset.co.il area, indicating that the Israel division’s electronic mail server was breached as a part of the assault.
Whereas the eset.co.il area is branded with ESET’s content material and logos, ESET informed BleepingComputer it’s operated by Comsecure, their Israel distributor.
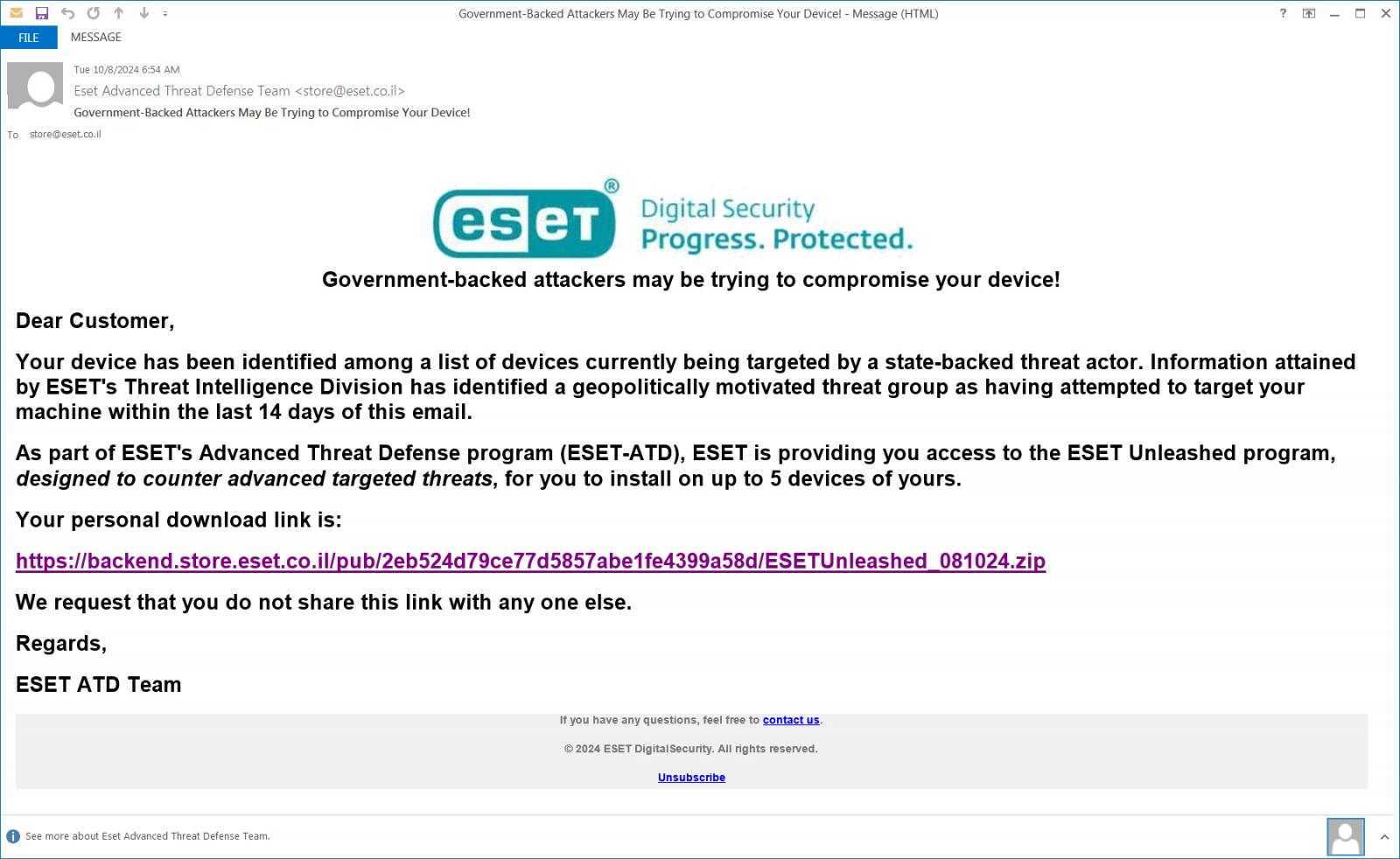
The emails fake to be from “ESET’s Advanded Threat Defense Team,” warning clients that government-backed attackers try to focus on the recipient’s machine. To assist defend the machine, ESET gives a extra superior antivirus software referred to as “ESET Unleashed” to guard in opposition to the risk.
“Your device has been identified among a list of devices currently being targeted by a state-backed threat actor. Information attained by ESET’s Threat Intelligence Division has identified a geopolitically motivated threat group as having attempted to target your machine within the last 14 days of this email,” reads the phishing electronic mail obtained by BleepingComputer.
“As part of ESET’s Advanced Threat Defense program (ESET-ATD), ESET is providing you access to the ESET Unleashed program, designed to counter advanced targeted threats, for you to install on up to 5 devices of yours.”
Supply: BleepingComputer
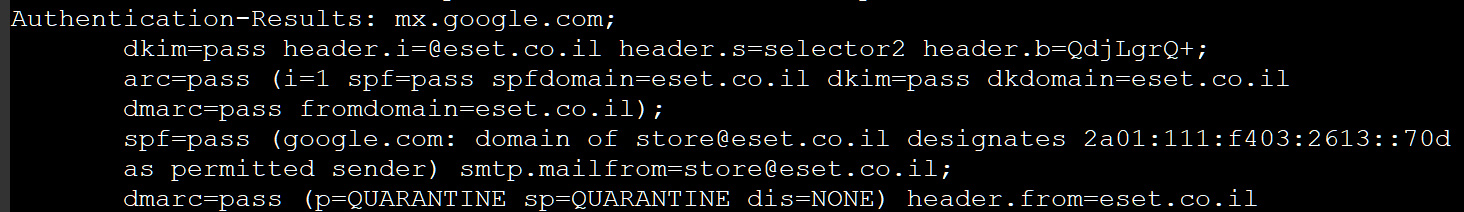
From the phishing electronic mail headers, BleepingComputer has confirmed that the e-mail originated from respectable mail servers for eset.co.il, passing SPF, DKIM, and DMARC authentication checks.
Supply: BleepingComputer
To additional add legitimacy to the assault, the hyperlink to the obtain was hosted on eset.co.il area at URLs like, https://backend.retailer.eset.co[.]il/pub/2eb524d79ce77d5857abe1fe4399a58d/ESETUnleashed_081024.zip, that are now disabled.
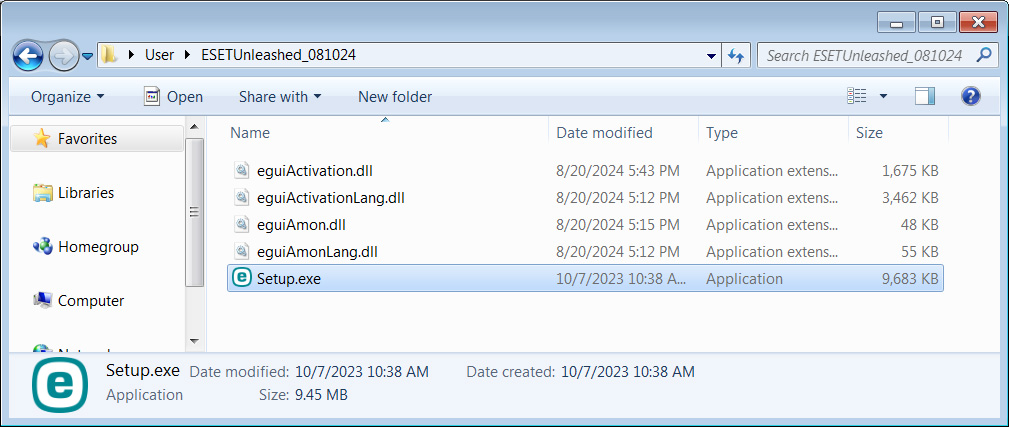
This ZIP archive [VirusTotal] accommodates 4 DLL recordsdata digitally signed by ESET’s respectable code signing certificates and a Setup.exe that’s not signed.
The 4 DLLs are respectable recordsdata distributed as a part of ESET’s antivirus software program. Nevertheless, the Setup.exe [VirusTotal] is the malicious knowledge wiper.
Supply: BleepingComputer
BleepingComputer tried to check the wiper on a digital machine, however the executable routinely crashed.
Cybersecurity knowledgeable Kevin Beaumont had higher success when run on a bodily PC, stating that it could attain out to a respectable Israeli information web site at www.oref.org.il.
“etup.exe is malicious. It uses a host of obvious techniques to try to evade detection,” explains Beaumont.
“I could only get it to detonate properly on a physical PC. It calls variously obviously malicious things, e.g. it uses a Mutex from the Yanluowang extortion/ransomware group.”
Presently, it’s unknown what number of corporations have been focused on this phishing marketing campaign or how Comsecure, ESET’s Israeli distributor, was breached.
BleepingComputer emailed numerous folks at Comsecure, together with its CEO, however has not obtained a reply but.
Whereas the assault has not been attributed to any explicit risk actor or hacktivism, knowledge wipers have lengthy been a well-liked software in assaults in opposition to Israel.
In 2017, an anti-Israel & pro-Palestinian knowledge wiper referred to as IsraBye was found in assaults on Israeli organizations.
In 2023, Israel suffered a wave of BiBi wiper assaults focusing on organizations, together with within the training and know-how sectors.
Many of those assaults have been linked to Iranian risk actors, whose aim was to not generate income, however reasonably to sow chaos and disrupt Israel’s economic system.