Hackers are brute-forcing passwords for extremely privileged accounts on uncovered Basis accounting servers, extensively used within the building {industry}, to breach company networks.
The malicious exercise was first noticed by Huntress, whose researchers detected the assaults on September 14, 2024.
Huntress has already seen lively breaches by way of these assaults at plumbing, HVAC, concrete, and different sub-industry corporations.
Open ports and weak passwords
In these assaults, the attackers are benefiting from a mixture of uncovered providers amplified by customers not altering default credentials on privileged accounts.
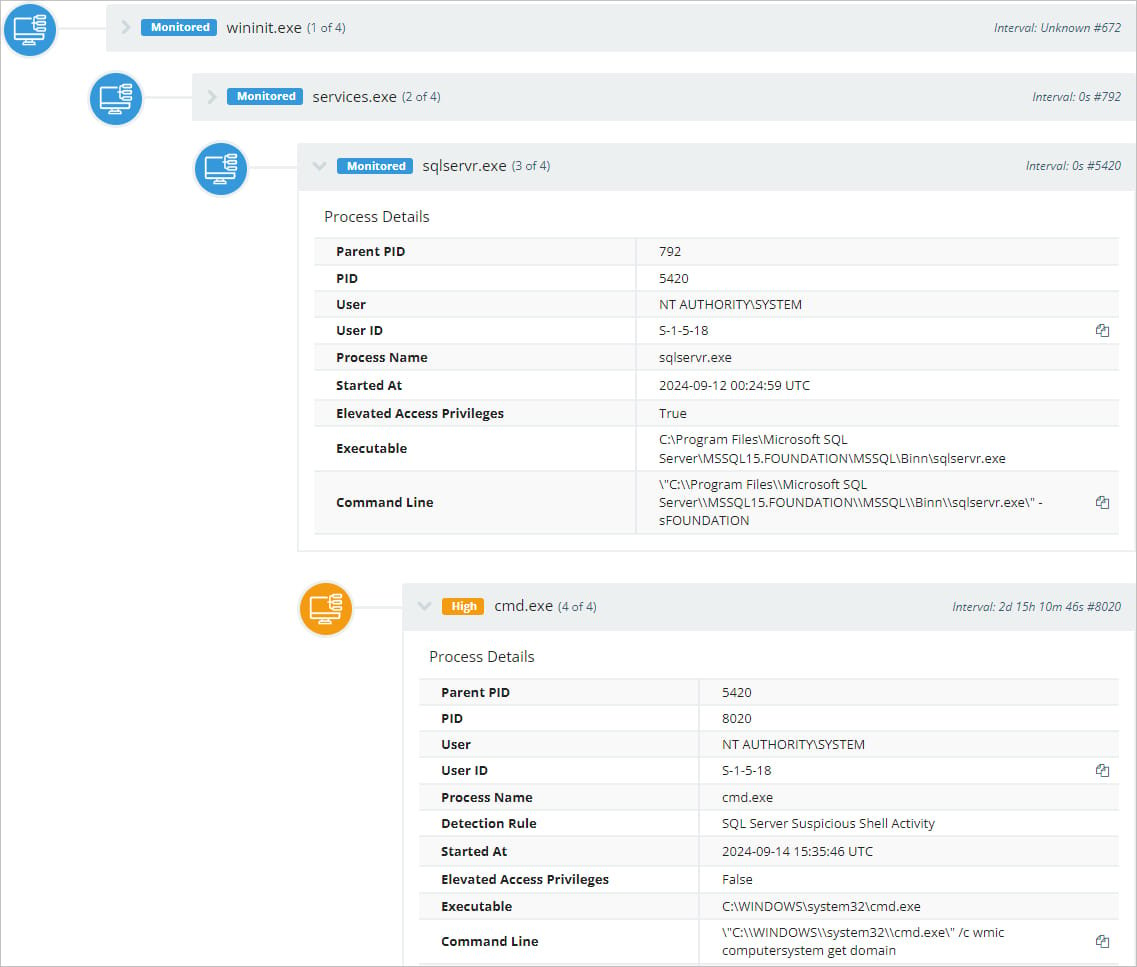
Huntress explains that the Basis software program features a Microsoft SQL Server (MSSQL) that may be configured to be publicly accessible through TCP port 4243 to help a companion cellular app.
Nonetheless, this additionally exposes the Microsoft SQL server to exterior assaults that try to brute drive MSSQL accounts configured on the server.
By default, MSSQL has an admin account named ‘sa’ whereas Basis has added a second one named ‘dba.’
Customers who haven’t modified the default passwords on these accounts are prone to hijacks by exterior actors. Those that did however picked weak passwords should be compromised through brute-forcing.
Huntress experiences that it noticed very aggressive brute-force assaults in opposition to these servers, typically reaching as much as 35,000 makes an attempt on a single host over an hour earlier than they efficiently guessed a password.
As soon as the attackers acquire entry, they allow the MSSQL ‘xp_cmdshell’ characteristic, which permits the risk actors to execute instructions within the working system by way of an SQL question.
For instance, the EXEC xp_cmdshell 'ipconfig' question will trigger the ipconfig command to be executed in a Home windows command shell, and the output can be displayed within the response.
Supply: Huntress
Two instructions noticed within the assaults are ‘ipconfig,’ to retrieve community configuration particulars, and ‘wmic,’ to extract details about the {hardware}, OS, and consumer accounts.
Huntress’s investigation from the three million endpoints beneath its safety unveiled 500 hosts working the focused accounting software program, 33 of which publicly uncovered MSSQL databases with default admin credentials.
Huntress instructed BleepingComputer it had alerted Basis of its findings, and the software program vendor responded by saying the difficulty solely affected the on-premise model of its software and never their cloud-based product.
Basis additionally famous that not all servers have port 4243 open, and never all focused accounts use the identical default credentials.
Huntress recommends that Basis admins rotate account credentials and guarantee they are not publicly exposing the MSSQL server if not wanted.
