On Tuesday, January 14, 2025, a set of vulnerabilities had been introduced that have an effect on the “rsync” utility. Rsync permits information and directories to be flexibly transferred domestically and remotely. It’s usually used for deployments and backup functions. In complete, 6 vulnerabilities had been introduced to the OSS Safety mailing record. Probably the most extreme vulnerability, CVE-2024-12084, could lead to distant code execution. This put up will cowl easy methods to detect and mitigate CVE-2024-12084.
On the time of this writing, no proof of idea has been launched, nor has there been any indication of energetic exploitation.
Vulnerabilities
CVE-2024-12084 (CVSS 9.8) – Heap overflow that would result in distant code execution
CVE-2024-12085 (CVSS 7.5) – Info leak
CVE-2024-12086 (CVSS 6.1) – Info leak
CVE-2024-12087 (CVSS 6.5) – Path traversal
CVE-2024-12088 (CVSS 6.5) – Path traversal
CVE-2024-12747 (CVSS 5.6) – Symbolic hyperlink race situation
How RSync works
Rsync is a file switch device that has been round for a very long time. One of many key options of rsync is that it’s going to solely switch information which have modified or are lacking. This enables customers to maintain information in sync throughout totally different directories, each domestically and remotely. Since it may be used remotely, it may be listening on port 873 (TCP) as a daemon course of. When working as a daemon, it’s known as “rsyncd.”
Rsync may also be run remotely on demand. On this state of affairs, a person would arrange “rsync” to hear on the distant server, after which use rsync domestically to start out the switch. To study extra about “rsync” and what it may well do, here’s a helpful information.
Detecting CVE-2024-12084
A heap overflow vulnerability was reported on January 14, 2025, which may result in distant code execution within the focused course of. This class of vulnerability permits an attacker to redirect the execution of a course of to an space of reminiscence they management, the place they’ve positioned malicious code. One technique for detecting that is to watch the method for uncommon habits, akin to command executions.
Falco is properly suited to this process because it has full visibility into the system calls made by “rsync.” In our detection, we are going to monitor the method for suspicious command executions. For instance, rsync shouldn’t execute many instructions (iptables, mongodump, curl, …) or different system instructions. There’s a use case the place rsync can execute a shell utilizing the “-e” choice, which may enable for a privilege escalation if the binary is SETUID.
# This macro may be modified for different, non-shell, instructions.
- macro: shell_binaries_arg_filename
situation: ( evt.arg.filename endswith "/ash" or evt.arg.filename endswith "/bash" or evt.arg.filename endswith "/csh" or evt.arg.filename endswith "/ksh" or evt.arg.filename endswith "/sh" or evt.arg.filename endswith "/tcsh" or evt.arg.filename endswith "/zsh" or evt.arg.filename endswith "/dash" )
- rule: Attainable Distant Code Execution utilizing rsync
desc: This rule detects rsync and rsyncd processes executing surprising binaries, which could point out arbitrary command execution via CVE-2024-12084.
situation: evt.kind in ( execve, execveat ) and evt.dir=> and proc.identify in ( rsync, rsyncd ) and shell_binaries_arg_filename
output: The %proc.identify course of was seen executing surprising binary %evt.arg.filename which could point out arbitrary command execution via the rsync or potential vulnerability exploitation (proc.exepath=%proc.exepath evt.arg.filename=%evt.arg.filename fd.identify=%fd.identify person.identify=%person.identify proc.identify=%proc.identify proc.pname=%proc.pname picture=%container.picture.repository:%container.picture.tag proc.cmdline=%proc.cmdline evt.res=%evt.res proc.pcmdline=%proc.pcmdline person.uid=%person.uid person.loginuid=%person.loginuid person.loginname=%person.loginname container.identify=%container.identify)
precedence: CRITICAL
tags: [host, container, MITRE, MITRE_TA0002_execution, MITRE_T1203_exploitation_for_client_execution]Code language: YAML (yaml)Sysdig Safe prospects robotically have this rule within the Sysdig Runtime Notable Occasions coverage.
Mitigating CVE-2024-12084
The variations affected by the heap overflow are: Rsync >= 3.2.7 and < 3.4.0
Organizations ought to prioritize remediating this vulnerability and patch all affected programs instantly. Remediation entails upgrading all cases of rsync in an atmosphere to model 3.4.0, as that model will handle the entire introduced CVEs.
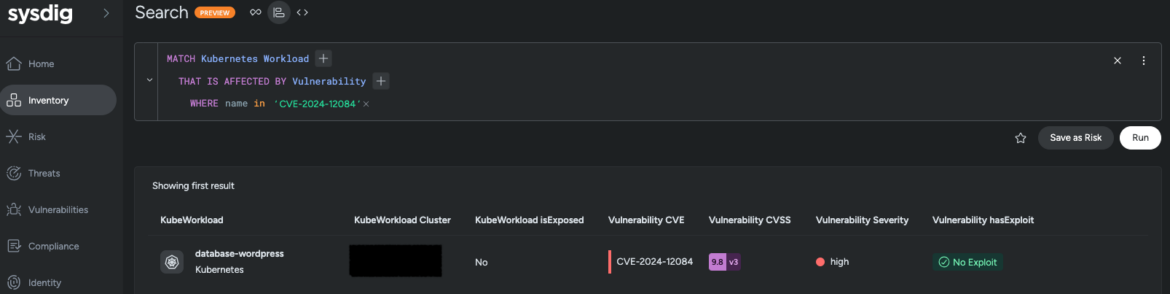
Utilizing Sysdig Safe’s Stock, customers can question all workloads affected by CVE-2024-12084. That is enabled by a versatile question language, which is one in every of a number of methods customers can search via their stock.
If patching isn’t instantly attainable, making certain not one of the cases of rsync are uncovered to the Web is one other step that may scale back the chance. By default, rsync listens on TCP port 873. The port needs to be blocked or restricted on the firewall or safety group. This plan of action should still depart publicity to inner assaults although.
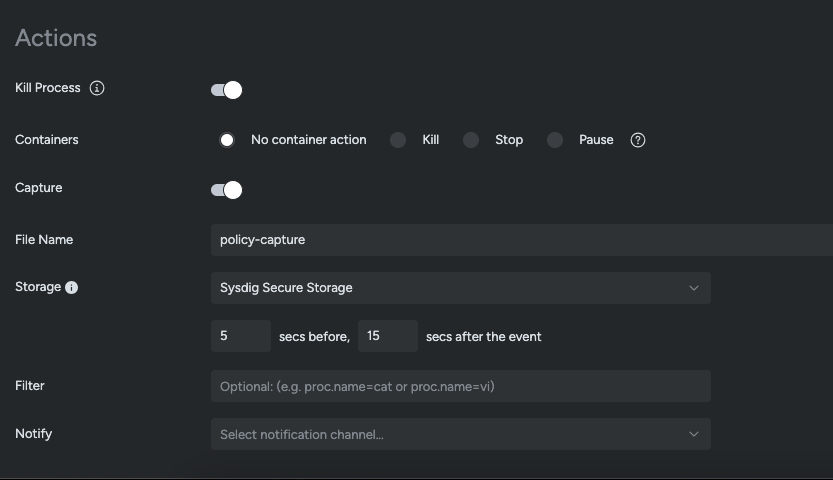
For Sysdig Safe prospects, the platform provides a number of choices for response if the above rule is triggered. “Kill Process” can be utilized to terminate the shell that the attacker launches. Or for a extra full response in a containerized atmosphere, “Kill Container” can be utilized to eradicate the complete workload. For deep forensic evaluation, a syscall seize may be taken robotically.
Conclusion
Rsync is a typical file synchronization utility that, based on Bleeping Laptop, is current on over 600k programs uncovered to the Web. Of the six new vulnerabilities, CVE-2024-12084 could enable for distant code execution. Utilizing Sysdig Safe, which is powered by open supply Falco, this sort of assault may be immediately detected and a response may be shortly initiated.