The time period “dark web” conjures up photographs of a shadowy netherworld of cybercrime, espionage, medication, and weapons. In actuality “dark web” websites are merely web sites ending in .onion that have to be accessed via a particular browser, The Onion Router (Tor).
Cybersecurity corporations have lengthy bought “dark web monitoring” packages, with every bundle that means one thing barely completely different.
In lots of instances, practitioners have struggled to search out worth in monitoring the darkish internet, significantly the place a vendor sells them on a complete bundle however doesn’t align the worth with the group’s safety wants.
In different instances organizations could imagine they’re too small for darkish internet monitoring to be invaluable, however in lots of instances startups and different small organizations are focused as a result of they’re small.
This text goes to look at the safety worth in darkish internet monitoring with a selected emphasis on deconfusion.
Darkish Internet Breach Monitoring
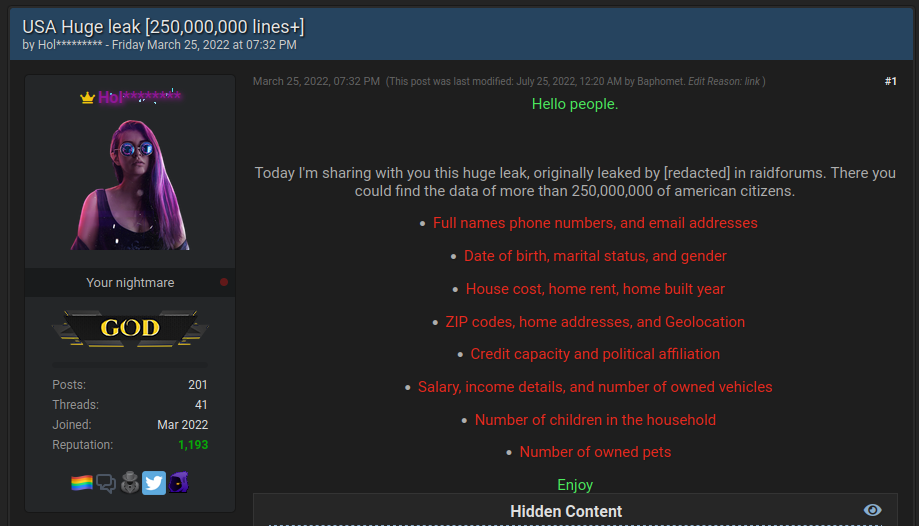
One of many first and most necessary distinctions to make is monitoring .onion websites, versus the recordsdata hosted on them. Have you ever ever acquired an alert that your credentials to a web site or utility had been compromised? When risk actors breach a service (or discover an uncovered cloud bucket!) they usually find yourself with enormous databases of consumer credentials to that service.
Recent units of breached credentials are distributed on the aptly named Breach Boards and different .onion websites in giant recordsdata.
Different risk actors are then capable of buy this knowledge, and replay the breached credentials towards different seemingly web sites the customers had signed up for. For instance, if a risk actor is aware of you latterly used an e-mail tackle and password on a enterprise accounting utility, they’ll strive those self same credentials on enterprise banking web sites.
This type of monitoring is without doubt one of the most elementary but in addition most actionable types of darkish internet monitoring.
Supply: Flare
Darkish Internet Discussion board, Market, and Ransomware Monitoring
The following stage up of monitoring is to gather and archive the precise content material of darkish internet pages. This encompasses issues like conversations about cybercrime, techniques, strategies, and procedures, and listings for company entry that risk actors are promoting.
The actual use-case right here is for classy organizations that haven’t solely a must establish leaked credentials however wish to proactively perceive the cybercrime ecosystem and the way it’s evolving.
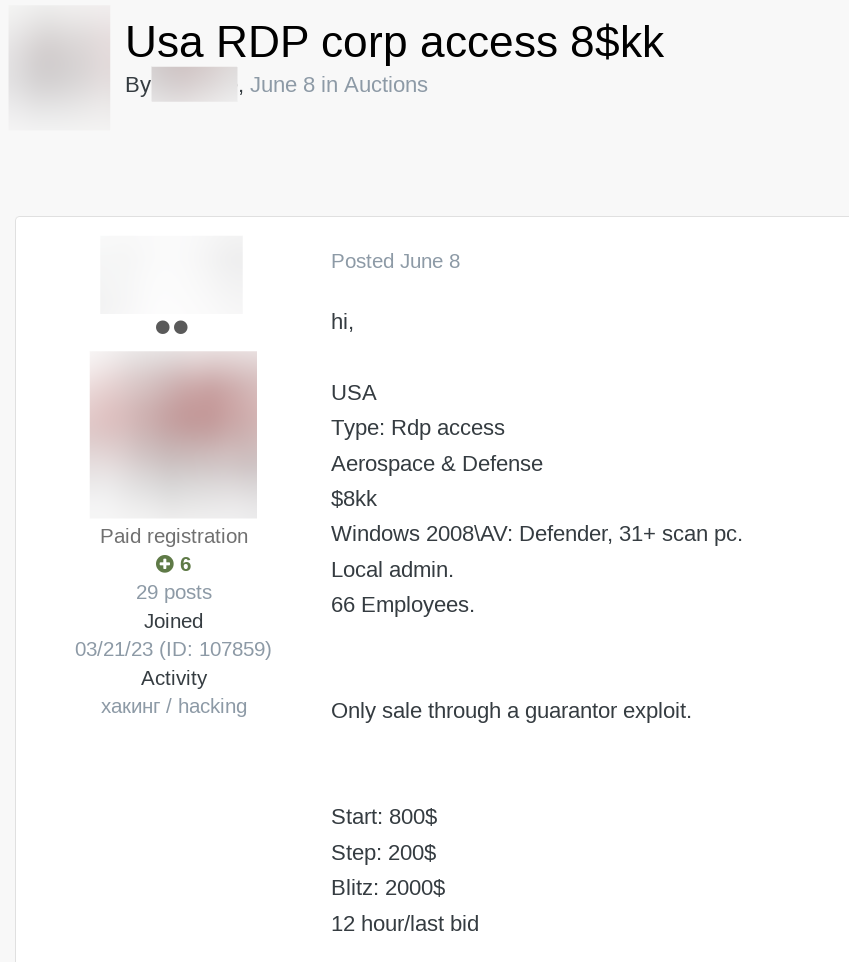
Monitoring Preliminary Entry Brokers on the Darkish Internet
In some instances there are alternatives to cease assaults in progress. For instance, preliminary entry brokers hack into firms then resell the obtained entry on specialised darkish internet boards. Figuring out that your group, or a third-party has community entry being bought generally is a enormous worth proposition.
Supply: Flare
One other key space of worth that organizations can get from darkish internet monitoring is monitoring
ransomware blogs discovered on .onion websites. In recent times ransomware teams have more and more shifted to double and triple extortion schemes, designed to place most stress on the sufferer to pay the ransom.
In consequence, ransomware teams now steal the information previous to encryption, and put up it on darkish internet leak websites if the sufferer doesn’t pay.
Chances are high you’d know in case you had been a sufferer of ransomware, however many organizations discover {that a} third-party has uncovered enormous numbers of delicate recordsdata, weeks or months after the very fact.
Monitoring ransom leak websites may be of huge worth, significantly in case your darkish internet monitoring platform can parse the file archives and match particular person file names.
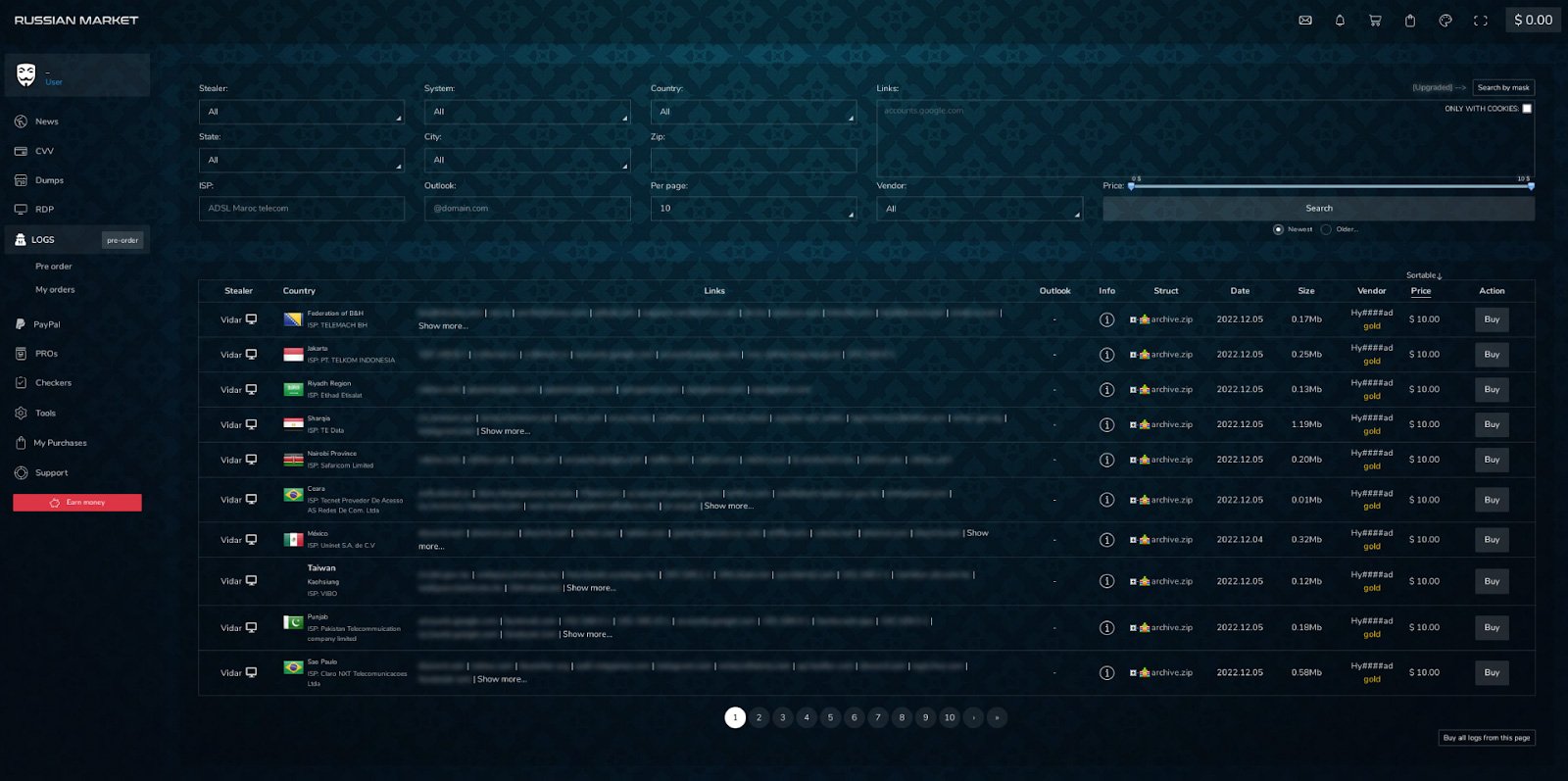
Lastly, Russian Market can be a essential supply to observe in 2024. Russian Market is a “stealer logs” market the place risk actors promote particular person stealer logs.
Supply: Flare
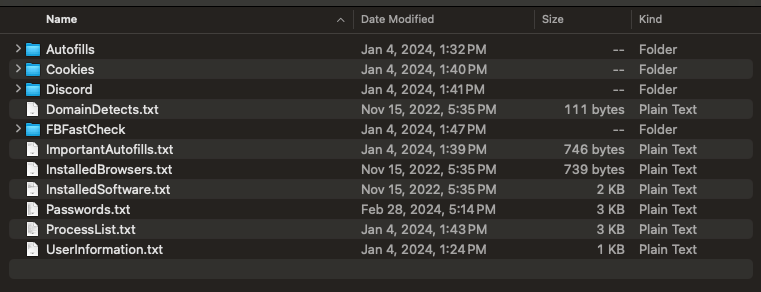
Stealer logs are a results of infostealer malware infections and embrace all the saved credentials of a single browser.
For instance we advocate monitoring for entry to your company area to establish a list that additionally incorporates entry to company credentials. Stealer logs are a prime vector for risk actors and ransomware teams in 2024.
Supply: Flare
The Prolonged Darkish Internet: Monitoring Telegram, Stealer Logs, and the Evolution of the Cybercrime Ecosystem
The cybercrime ecosystem is not confined to .onion websites discovered on Tor. Risk actors now routinely use immediate messaging functions similar to Telegram to commit cybercrime, promote knowledge, and work together with one another.
There at the moment are 1000’s of Telegram channels targeted on financial institution fraud, stolen accounts, credential theft, and stealer log distribution on Telegram.
Flare at present tracks greater than 6,000 cybercrime Telegram channels and screens multiple million stealer logs per week from Telegram for our prospects. Telegram, different social media, and P2P immediate messaging functions are a completely essential vector of progress for the cybercrime ecosystem.
By way of quantity, actionability, and safety worth, getting complete monitoring of the stealer log ecosystem is completely important. At Flare we estimate that between 5%-10% of stealer logs have company credentials, and in some instances have seen CRMs, company financial institution accounts, VPN, and RDP entry leaked into Telegram.
Darkish internet monitoring shouldn’t be a “low actionability” gross sales gimmick, it’s as an alternative a essential part of an efficient info safety program that helps organizations establish exterior threats to their cybersecurity posture.
Darkish Internet Monitoring with Flare
The Flare Risk Publicity Administration (TEM) resolution empowers organizations to proactively detect, prioritize, and mitigate the sorts of exposures generally exploited by risk actors.
Our platform robotically scans the clear & darkish internet and illicit Telegram channels 24/7 to find unknown occasions, prioritize dangers, and ship actionable intelligence you should use immediately to enhance safety.
Flare integrates into your safety program in half-hour and sometimes replaces a number of SaaS and open supply instruments.
Study extra by signing up for our free trial.
Sponsored and written by Flare.
